Thanks to the EVE JSON events and alerts format that appear in Suricata 2.0, it is now easy to import Suricata generated data into a running Splunk.
To ease the first steps of integration, Stamus Networks is providing a Splunk application: Suricata by Stamus Networks
It can be installed like any other applications and it just requires that a Suricata EVE JSON file is known and parsed by Splunk.
Current version is providing a dashboard and a few searches:
This post describes how to import the application and if you don't have already done it how to import data from a Suricata EVE file.
Importing the application
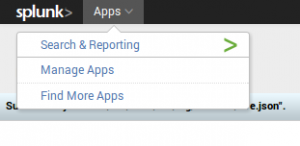
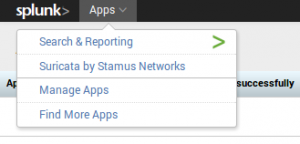
Importing the application is done via the Apps menu on top of Splunk starting page:
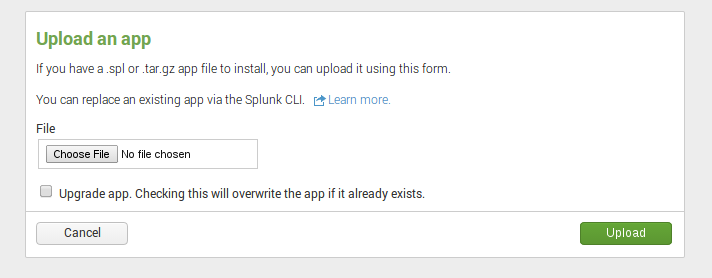
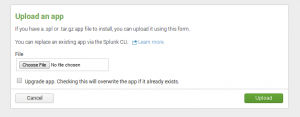
Suricata by Stamus Networks application is currently provided as a file, so you need to download it: Suricata by Stamus Networks. Once done, you can add the application:
You need to select the file
Importing a Suricata EVE JSON file
Since splunk 6.1.x, the recognition of the file format is automatic. If you are using an older version of Splunk, you may need to refer to this page to import Suricata EVE file.
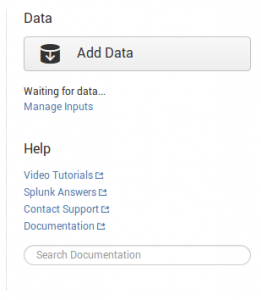
Here's the detailed procedure to import Suricata EVE data into Splunk. From the starting page, we click on Add Data:
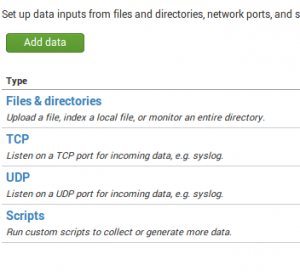
Then we click an Files & Directories to tell Splunk to import data from Suricata EVE JSON file:
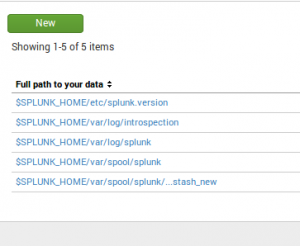
Once done, we click on the New button:
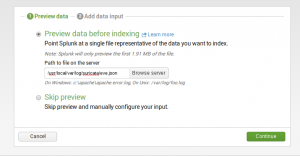
Now, we only need to give the complete path to the eve.json file:
Once this is done, we just need to click on all Continue buttons to be done.
Using the application
Now, we can go to the application by clicking on Suricata by Stamus Networks:
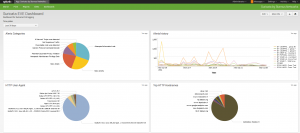
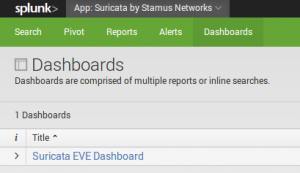
Next step can be to to go the dashboard:
The dashboard contains some interesting panels like the following one who displays the destination IP addresses that are using a self-signed certificate for TLS connections: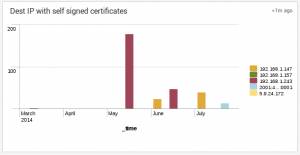
Conclusion
This application should evolve with time, so stay tuned and follow us on twitter for more information.