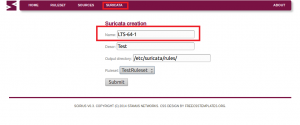
The Ubuntu used in this tutorial:
root@LTS-64-1:~/opt#uname -a
Linux LTS-64-1 3.5.0-45-generic #68~precise1-Ubuntu SMP Wed Dec 4 16:18:46 UTC 2013 x86_64 x86_64 x86_64 GNU/Linux
If you have these packages installed you need to remove them so that Scirius would work with the latest python dependencies.
Please be careful so that this actually does not affect your current running services. It is always best to test first :)
root@LTS-64-1:~/opt#apt-get remove django-tables python-django python-django-south python-git
Install the needed dependencies:
root@LTS-64-1:~/opt#aptitude install python-pip git
root@LTS-64-1:~/opt#pip install django django-tables2 South GitPython pyinotify daemon
Clone the latest version
root@LTS-64-1:~/opt#git clone https://github.com/StamusNetworks/scirius.git
root@LTS-64-1:~/opt#cd scirius/
root@LTS-64-1:~/opt/scirius# python manage.py syncdb
Start Scirius
root@LTS-64-1:~/opt/scirius#python manage.py runserver
Validating models...
Failed to setup thread-interrupt handler. This is usually not critical
0 errors found
May 20, 2014 - 19:51:27
Django version 1.6.4, using settings 'scirius.settings'
Starting development server at http://127.0.0.1:8000/
Quit the server with CONTROL-C.
If you need to connect to the server remotely (provide your ip) -
root@LTS-64-1:~/opt/scirius#python manage.py runserver 10.0.10.5:8000
Validating models...
Failed to setup thread-interrupt handler. This is usually not critical
0 errors found
May 20, 2014 - 19:51:58
Django version 1.6.4, using settings 'scirius.settings'
Starting development server at http://10.0.10.5:8000/
Quit the server with CONTROL-C.
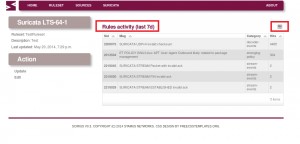
Now lets have a walk through registering and adding a ruleset
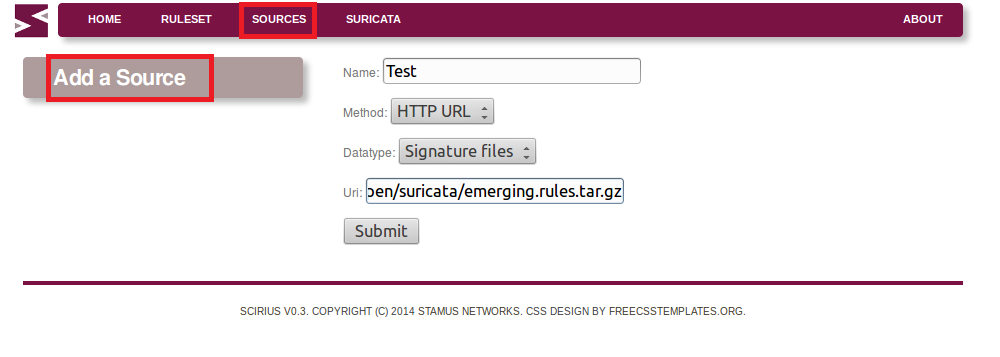
For example (for the latest stable and dev Suricata) from http://rules.emergingthreats.net/open/suricata/emerging.rules.tar.gz since Emerging Threats create, write and distribute specially tuned for Suricata rulesets that make use of the advanced features of that IDS engine.
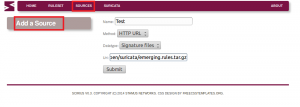
First we need to add a source: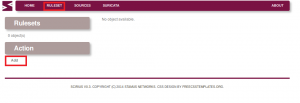
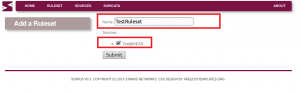
Then we add a ruleset:
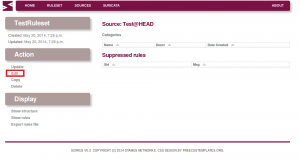
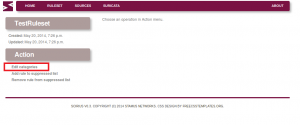
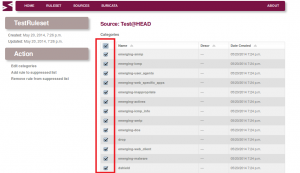
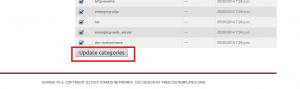
We need to edit the ruleset and select the categories we want from that ruleset:
Select categories:
Validate changes:
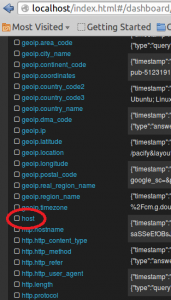
If you have already Elasticsearch, Logstash, Kibana installed on the same server,
you could do the following -> put in the values as on the picture - except the host name - chose the hostname to be exactly as your hostkey in Elasticsearch/Kibana , like in the pics below.
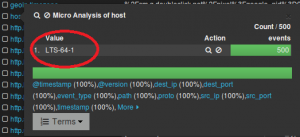
Then in Scirius ->
Now you should be able to see the hits and which rules are making the most noise :)
That's it for a quick intro.