So, what’s next? You’ve had a successful hunt, uncovered some type of threat or anomalous behavior on your network, and now you need to do something about it. We felt it was important to include additional details on all the automation and escalation functionalities that are available to users so they can respond to threats sooner in the future - after the hunt.
If you missed our introduction to the SSP Guided Threat Hunting Interface you can go back to read more about enriched hunting with SSP and the various features available to users who wish to take a more proactive defensive stance to protect their organization and search for specific threats, alerts, or behaviors. That article kicks off the beginning of our “Discover SSP” series, which will detail a different guided threat hunting filter every week.
Automation and Escalation Overview
One of the most useful and enabling features built into the Stamus Security Platform (SSP) is the integrated guided threat hunting. This “Stamus Enriched Hunting” empowers hunters to investigate, classify, automate, and escalate vast amounts of event data, alerts, and contextual metadata.
In many cases, hunting is driven by a hypothesis and infused by knowledge and expectation with the specifics of their organization in mind. Any of these hypotheses an analyst might have can be formulated into an SSP automation, and the results can be classified or automatically escalated.
The ability to turn a hypothesis into an automated hunt that is driven by context and knowledge is greatly appreciated among SOC team members and management alike, as it allows security practitioners to lower their time to act, respond, and make decisions. Security teams can respond sooner when they are empowered by the capabilities of SSP because they are able to detect threats faster, more accurately, and with greater context.
Oftentimes, organizations already have some tools, software, or integration mechanisms that support automation. The good news is that Stamus Security Platform is 100% RestAPI enabled and natively integrates with such technologies.
In this article we will describe some ways security teams can benefit from augmenting the the hunting filters with automation on the Stamus Security Platform to save time and effort and enable more seamless knowledge transfer while leveraging existing tools and technology.
Integrations
Integrations enable any escalated event to trigger a follow up action. These actions might include a simple notification message in a chat channel, populating and logging an incident response ticket, or triggering a playbook response in a SOAR.
Stamus Security Platform allows users to simply configure integrations. Whether it is e-mail, SOAR , opening an incident response ticket or a webhook, or more, security analysts using SSP can integrate with just a few clicks. This ability to automate the final action or notification is arguably more important than the automation of the hunt itself.
To set up integrations, access the options from the drop down Administration menu on the top left of the screen.
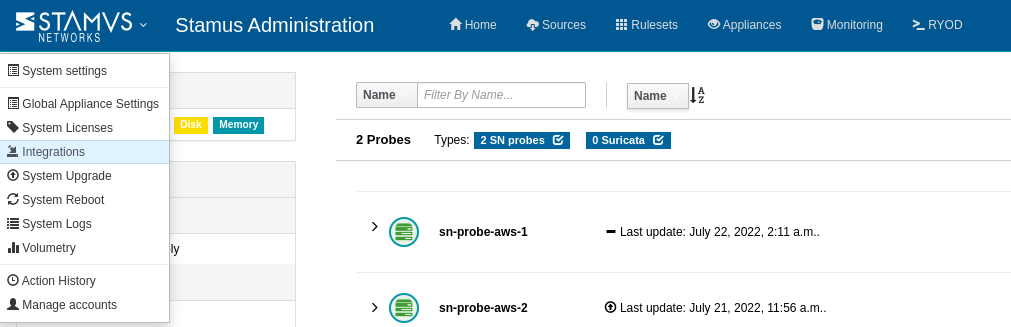
Let’s explore a few integration examples below:
Email is a more traditional method of communication, but for many security teams it represents an important integration.
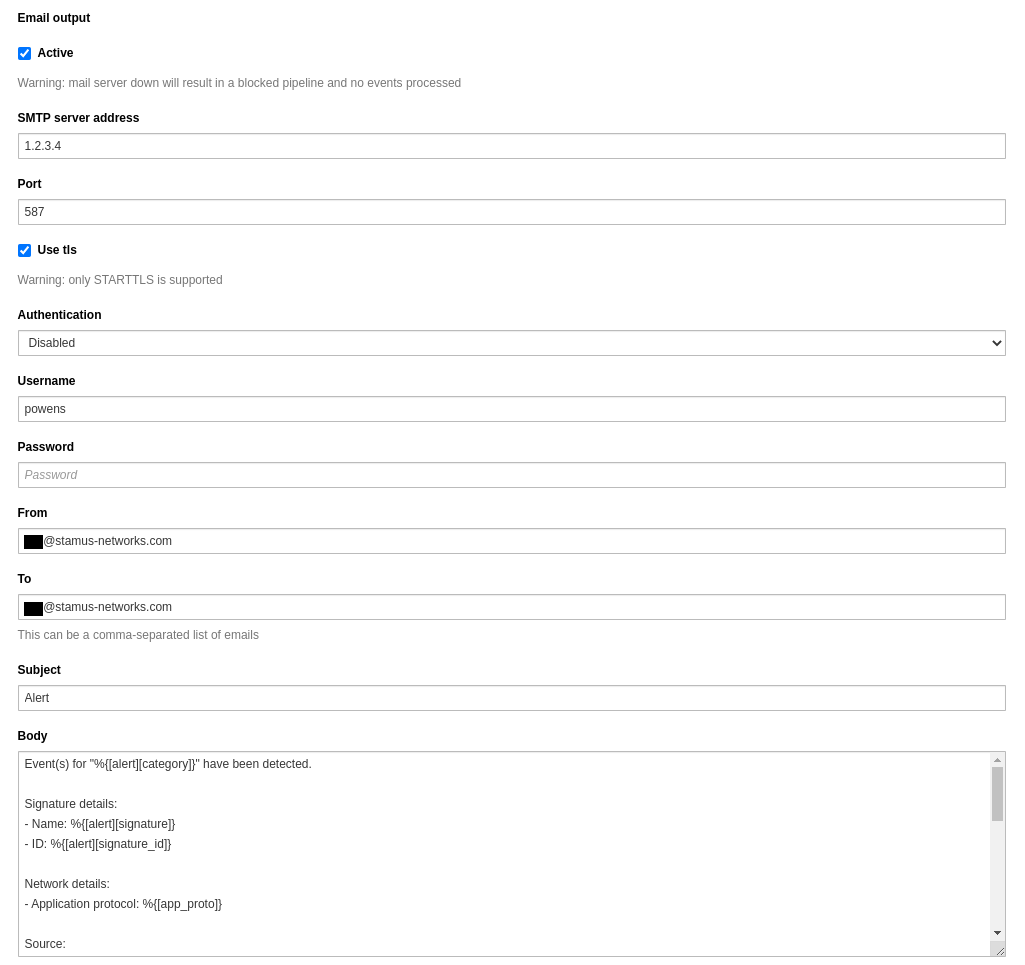
Webhooks
Webhooks provide a very versatile and easy method of notification. Stamus Networks provides extensive documentation which covers a myriad of possible variables and customizations that range from simple IoCs to connection-specific and hostInsights information.
For example, configuring a webhook automatic notification is a simple one-time setup action.
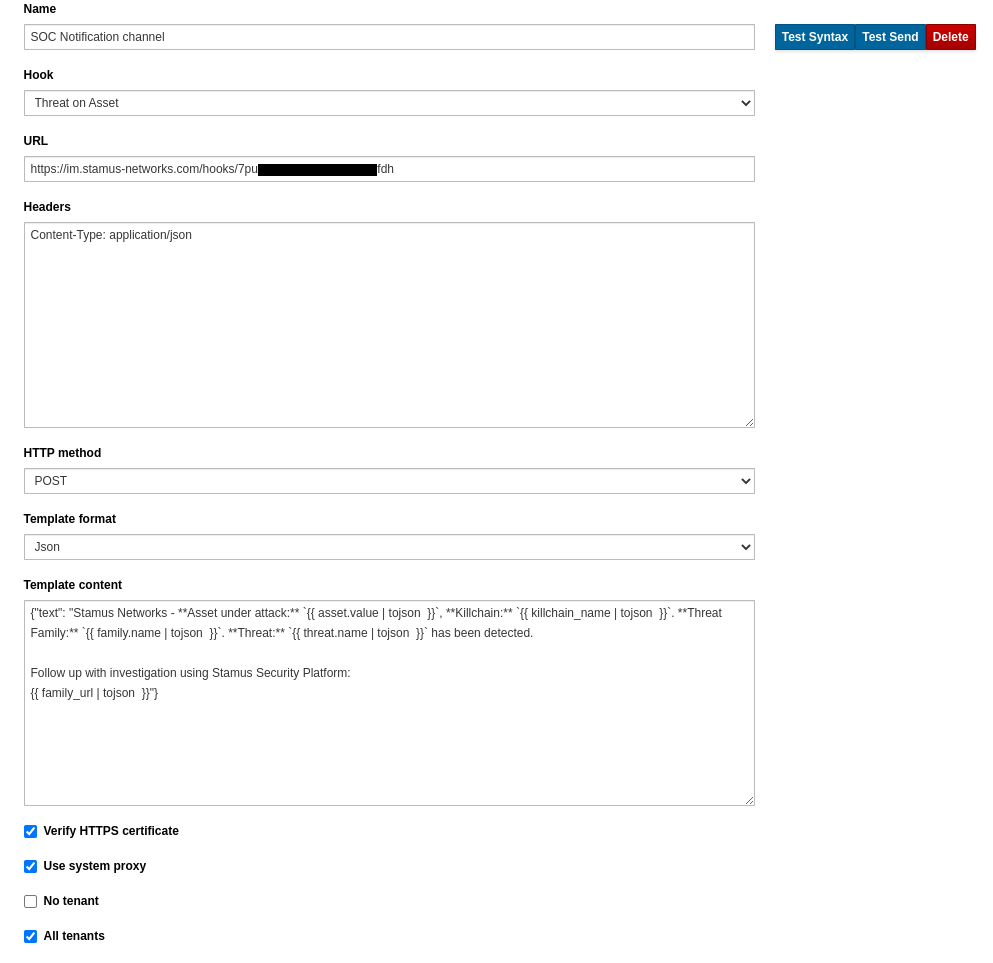
Security teams can configure a webhook notification into any supporting messaging platform like Discord, Slack, Mattermost, Microsoft Teams..
If you are interested in seeing a live feed from one of our QA lab systems, check out our public Stamus Labs feed channel on Discord. See screenshot below:
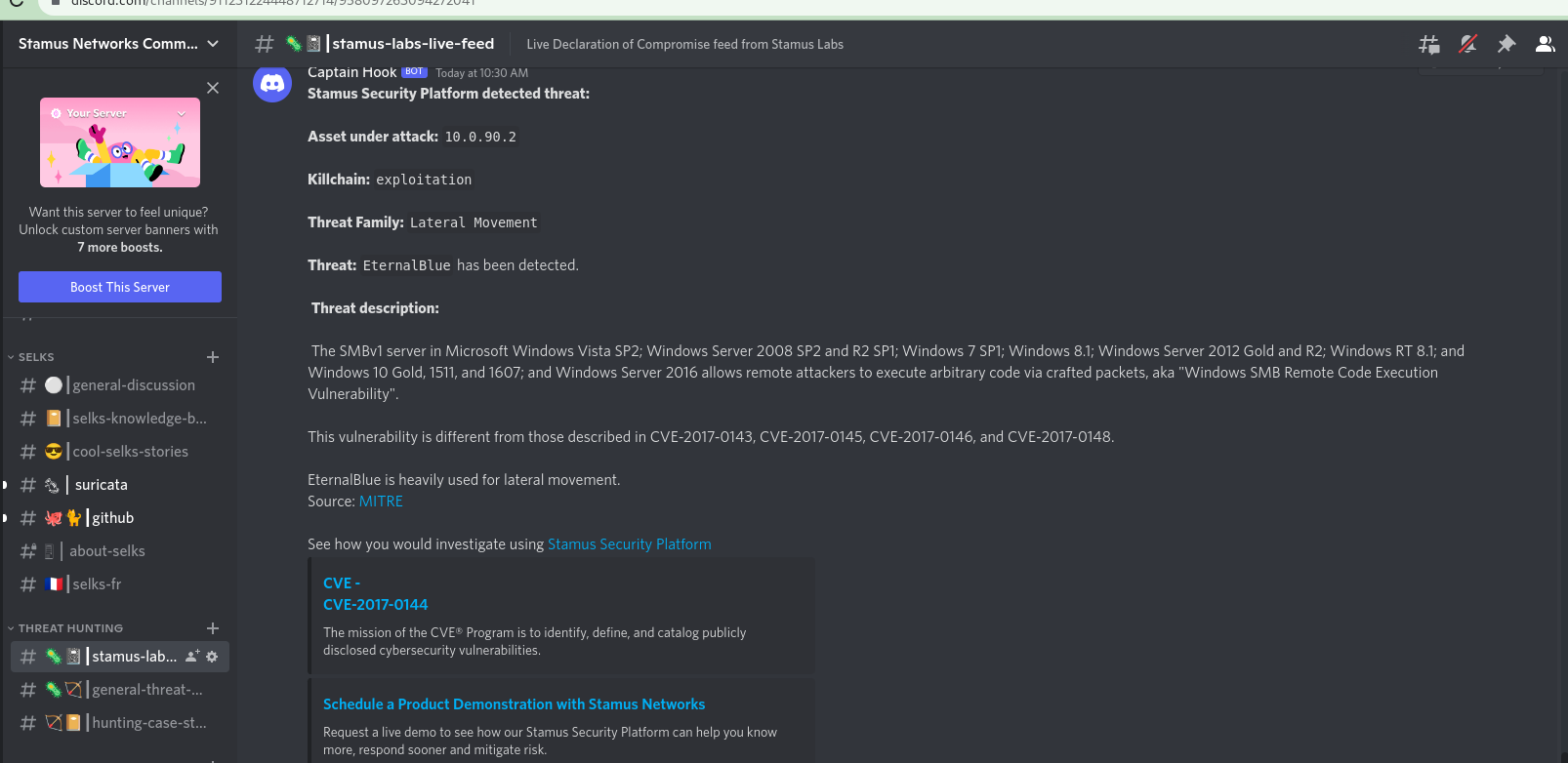
Here are a couple of examples in which SSP delivers a message via webhook to a Mattermost channel:
MalDoc
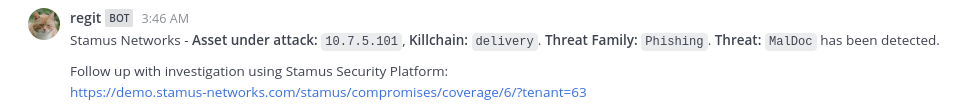 Emotet
Emotet
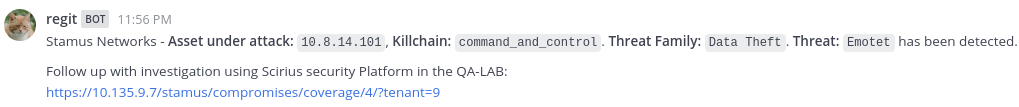
SOAR
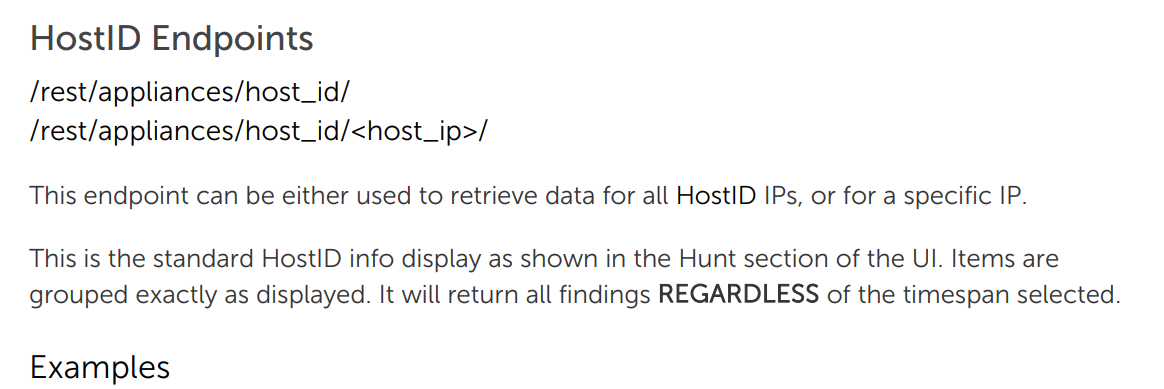
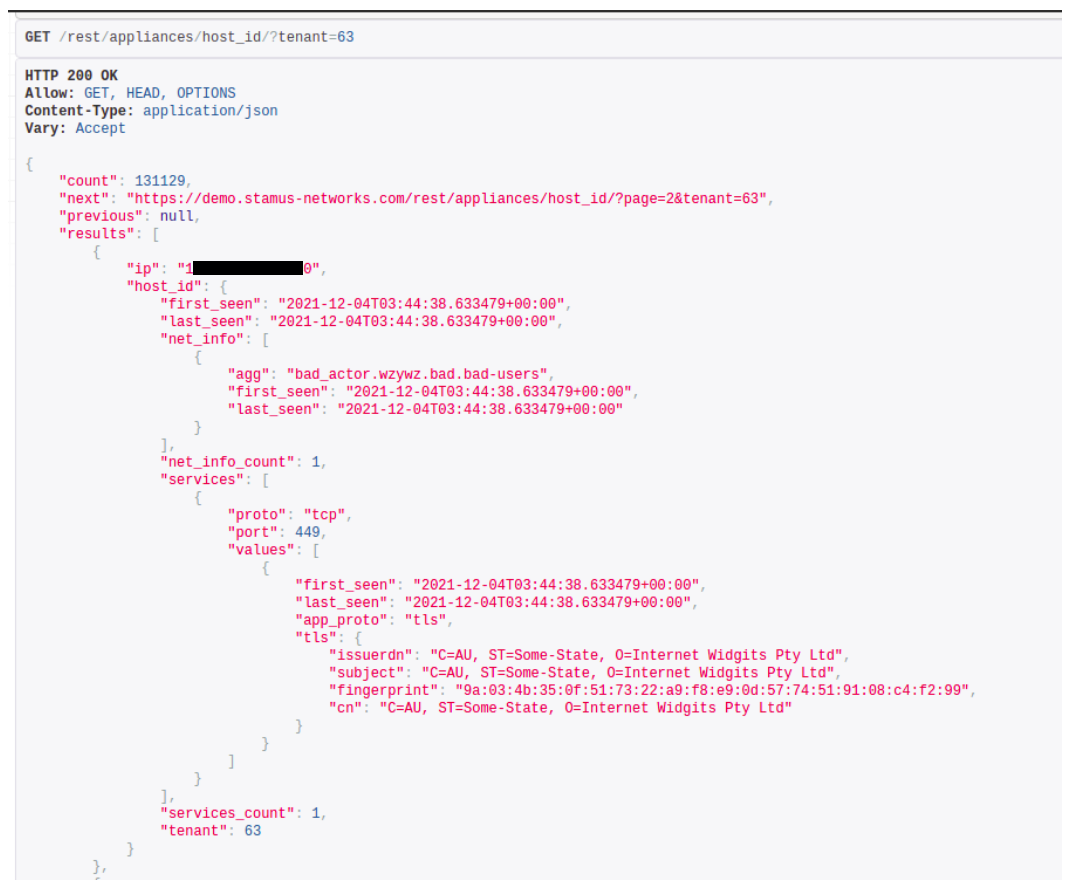
Stamus Security Platform provides a full RestAPI with extensive documentation of hundreds of actual examples. In the examples below, we show the documentation for how to query the “Host Insights” function for information about a specific host.
Using the API, it is also possible to query the system and a specific tenant for the presence of specific network services is also possible:
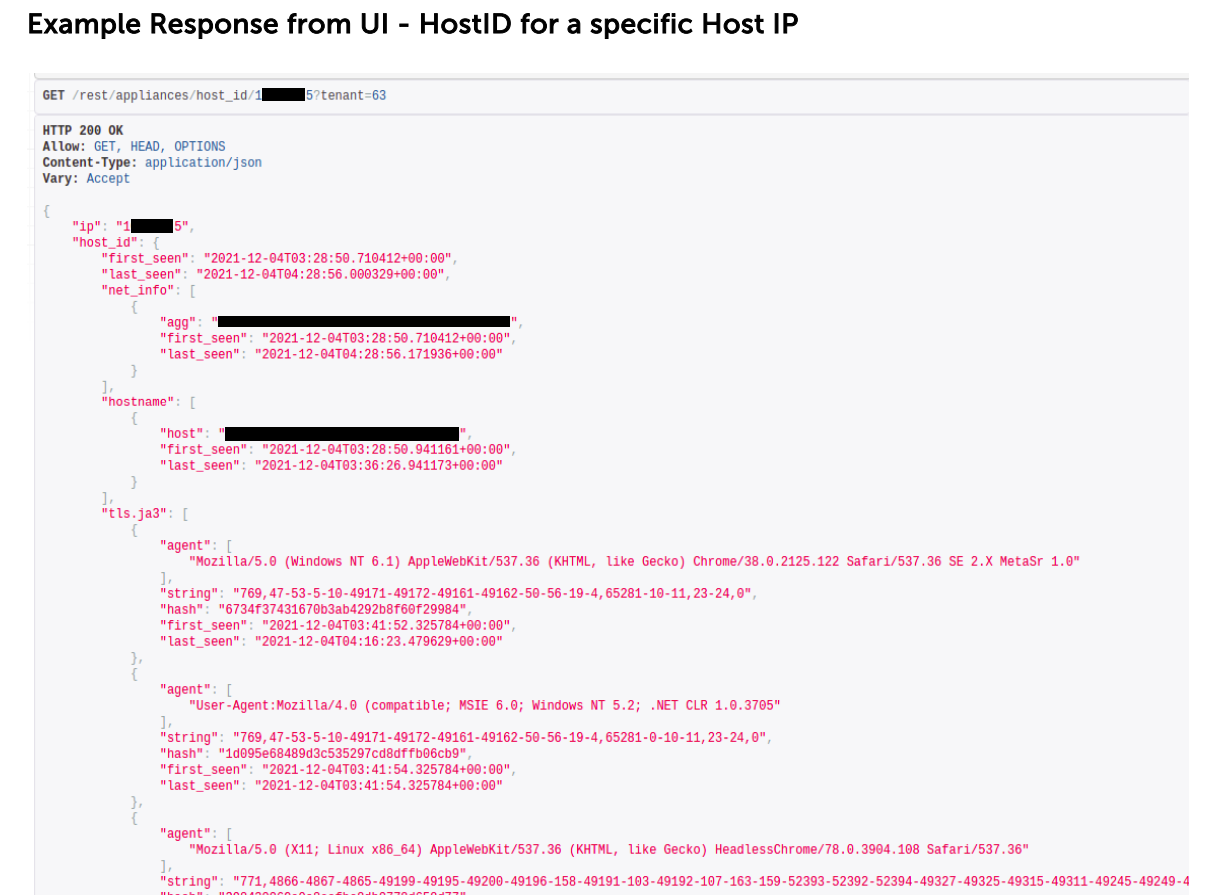
It can also be enriched with details about encrypted communications,, hostnames, user agents, or server roles that have been observed:
Incident Response
Automated response capability is important. However, it is essential that automated responses auto-populate with all the needed information in order to inform better decision making and information sharing within security teams.
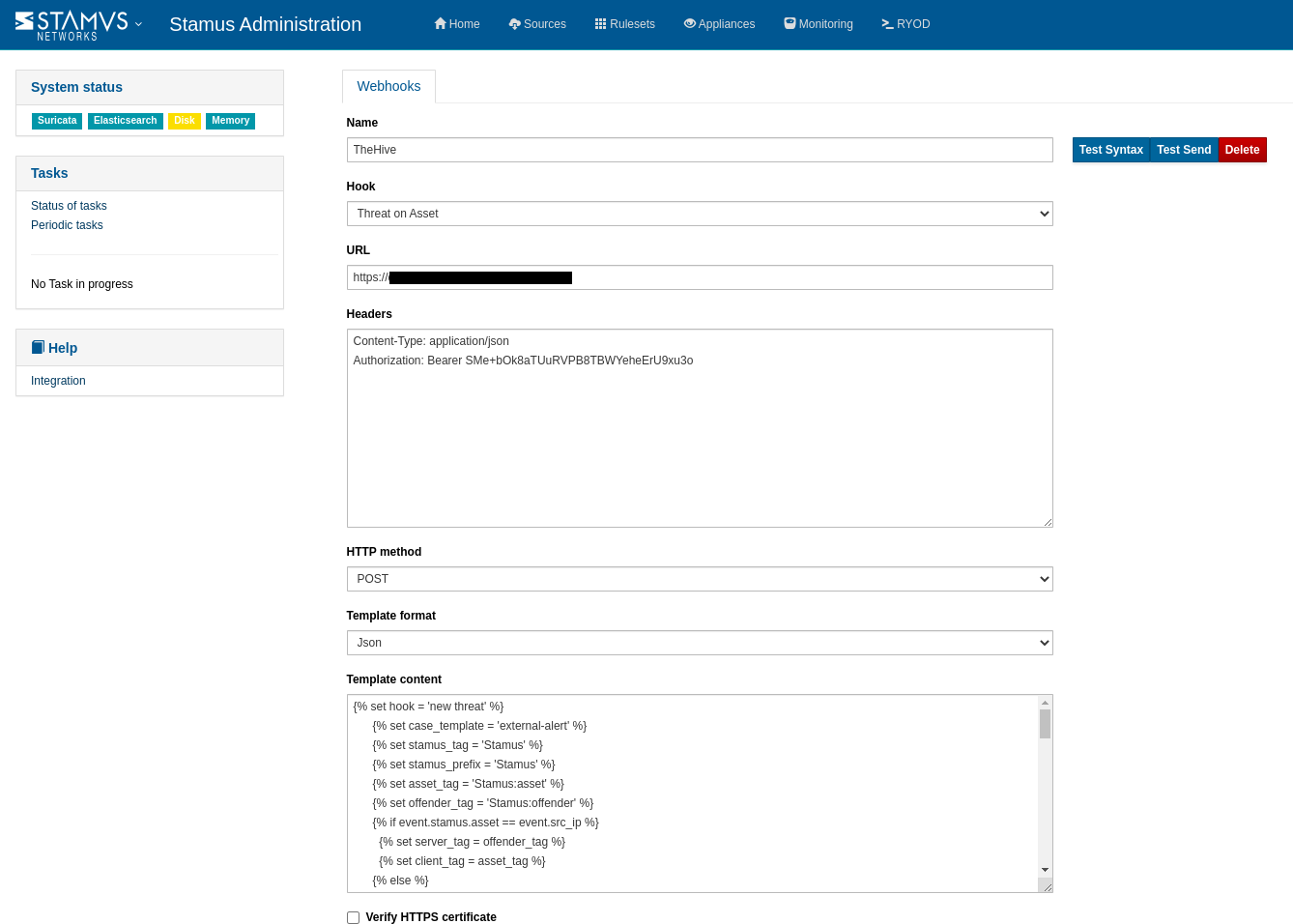
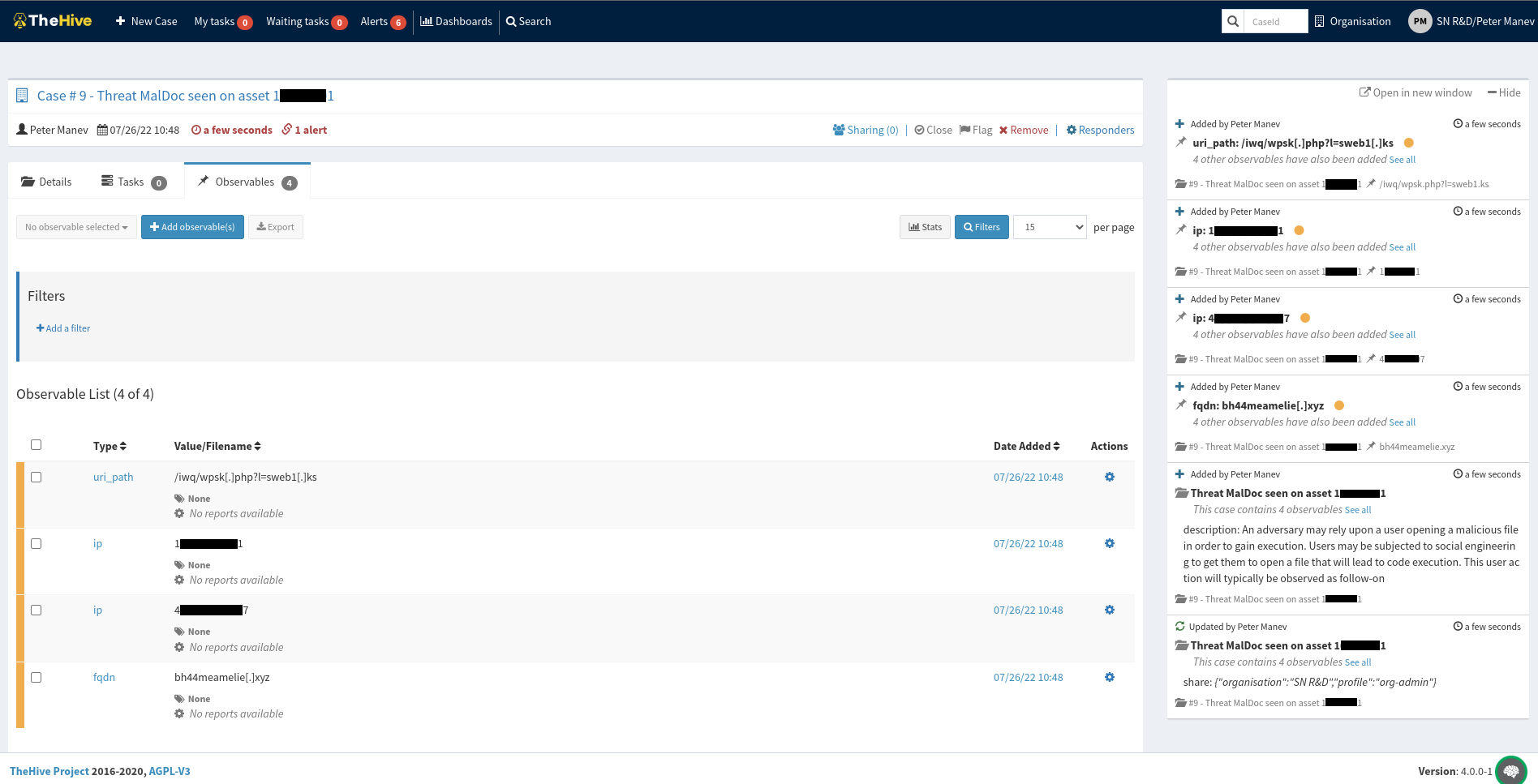
Below is an example showing the one-time setup of an automated incident response integration with The Hive. Once completed, the integration allows an escalated event to create incident response tickets per DoC.
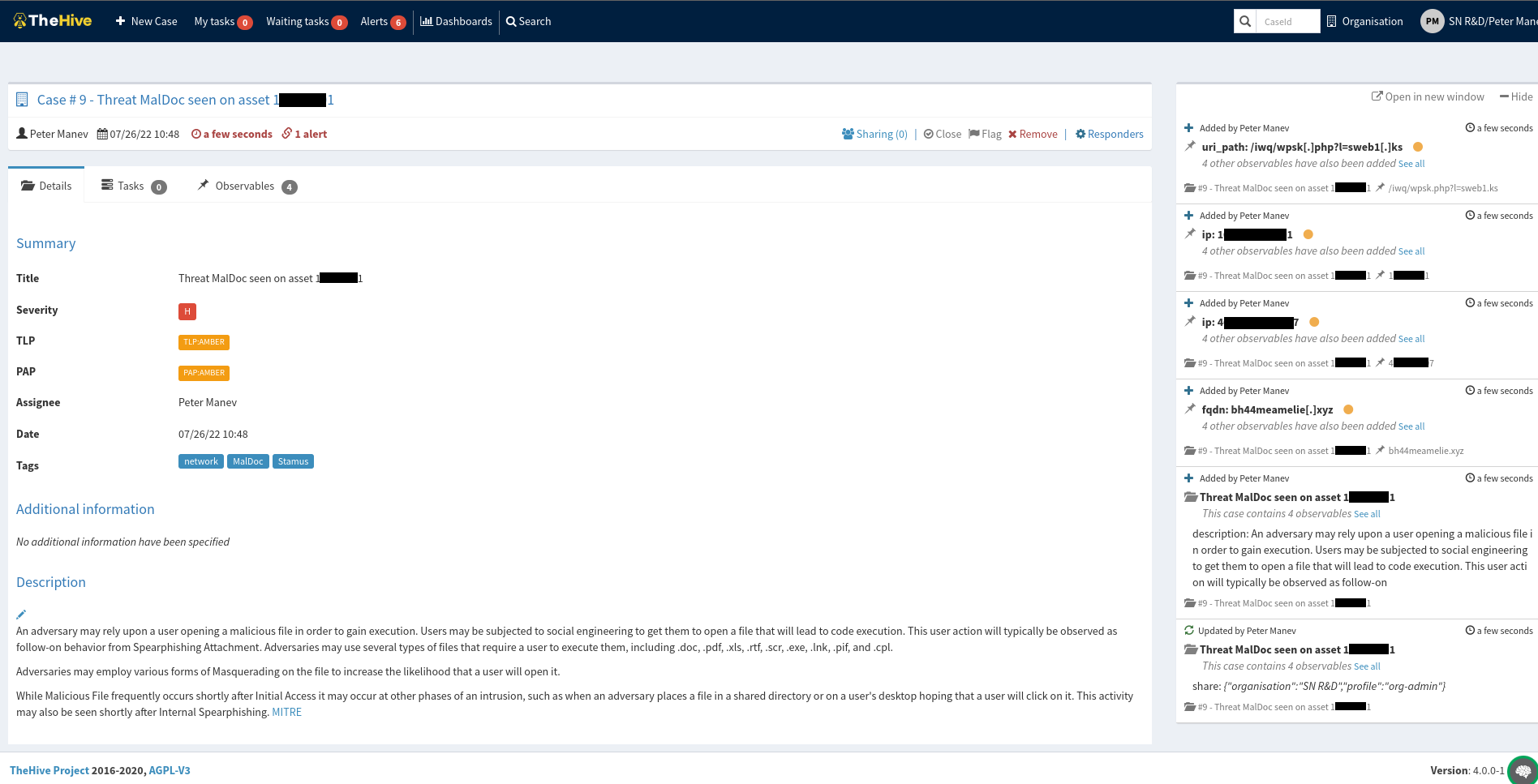
See the resulting IR ticked logged in The Hive. The automation populates the ticket logged supporting documentation, explanation, and any observables needed like URLs, FQDNs, and more.
Other
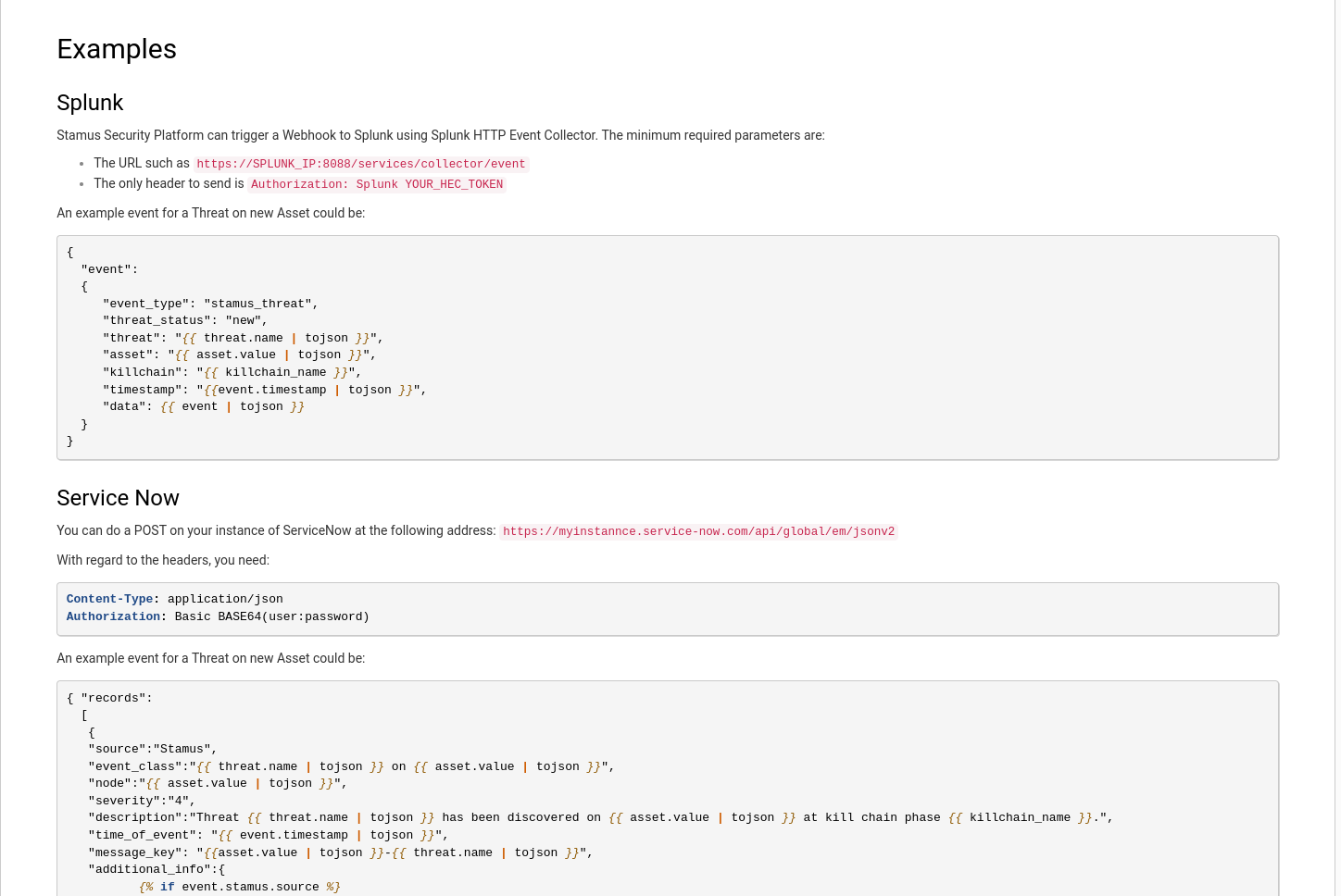
There are tons of possibilities when it comes to integrating Stamus Security Platform with other technologies in the security team’s stack. SSP can be used natively with platforms like Splunk, ServiceNow, or any other software that supports Webhook technology.
Conclusion
What comes after “After the Hunt”? Well, another hunt I suppose. These escalation and automation features can be used with any of our guided threat hunting filters. Armed with these capabilities, an analyst can know more, respond sooner, and mitigate risk to their organization.
If you would like to learn more about Stamus Security Platform (SSP) or the Stamus Enriched Hunting interface, click on the link below to schedule a demo.







