Stamus Networks will be exhibiting Forum InCyber, one of Europe’s leading cybersecurity events,...
Stamus Networks Team
Recent Posts
At Stamus Networks, we have always been driven by a commitment to openness, transparency, and...
Today, we are proud to announce the general availability of Update 40 (U40) - the latest release of...
The recent global outage caused by an update to CrowdStrike Falcon, CrowdStrike's endpoint...
The recent global outage caused by an update to CrowdStrike Falcon, CrowdStrike's endpoint...
At Stamus Networks, we are wrapping up another great year, so it is time to again review the news,...
For a large organization, keeping track of numerous security systems or internal security policies...
If you have ever worked for a large enterprise, then you may be familiar with the term “enterprise...
In our past series, “Threat! What Threats?” we covered the topic of phishing in a generic way, but...
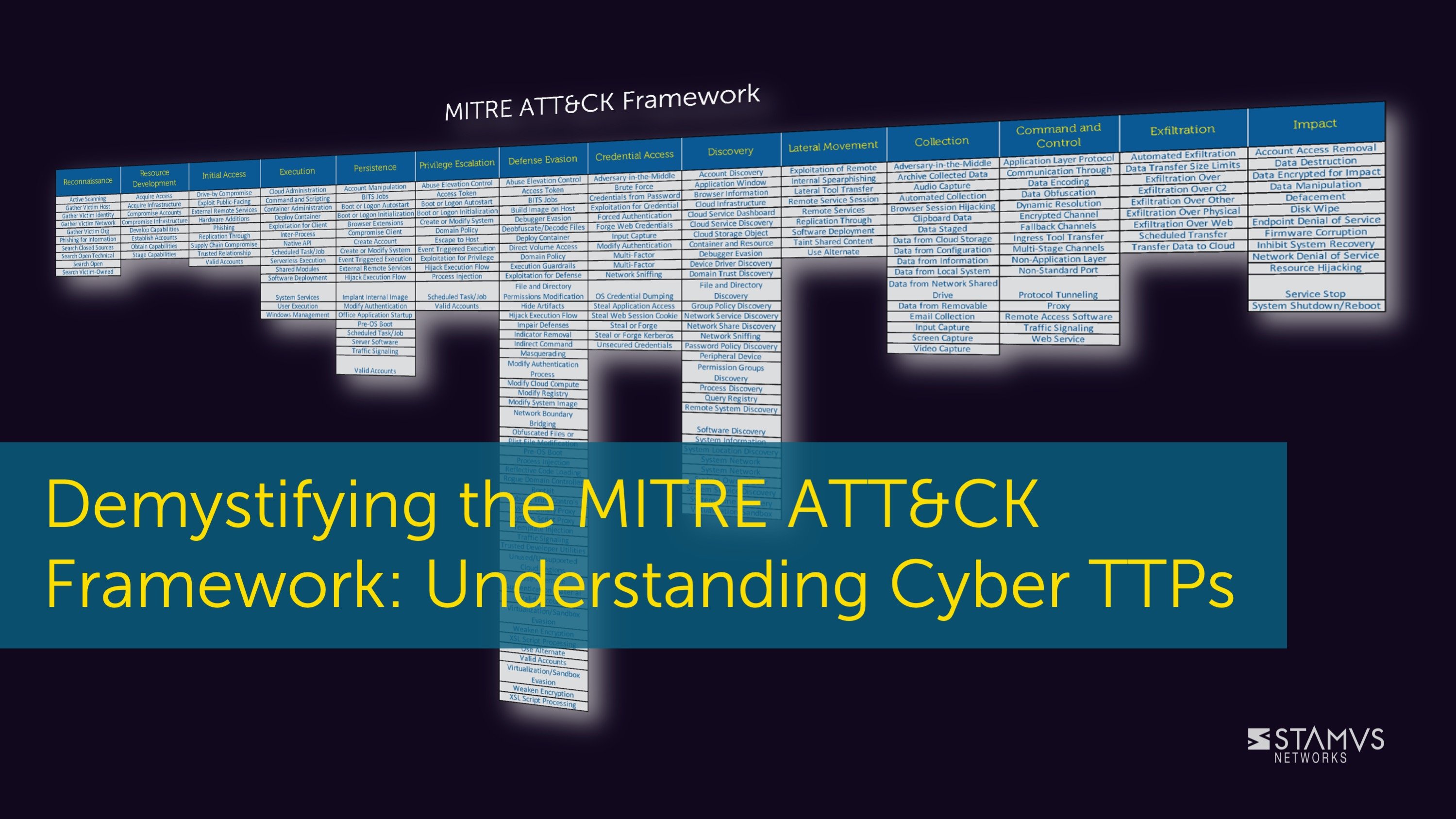
When an organization wants to learn more about the tactics, techniques, and procedures (TTP) used...
In the past few blog posts, we have discussed at length the importance of creating a comprehensive...
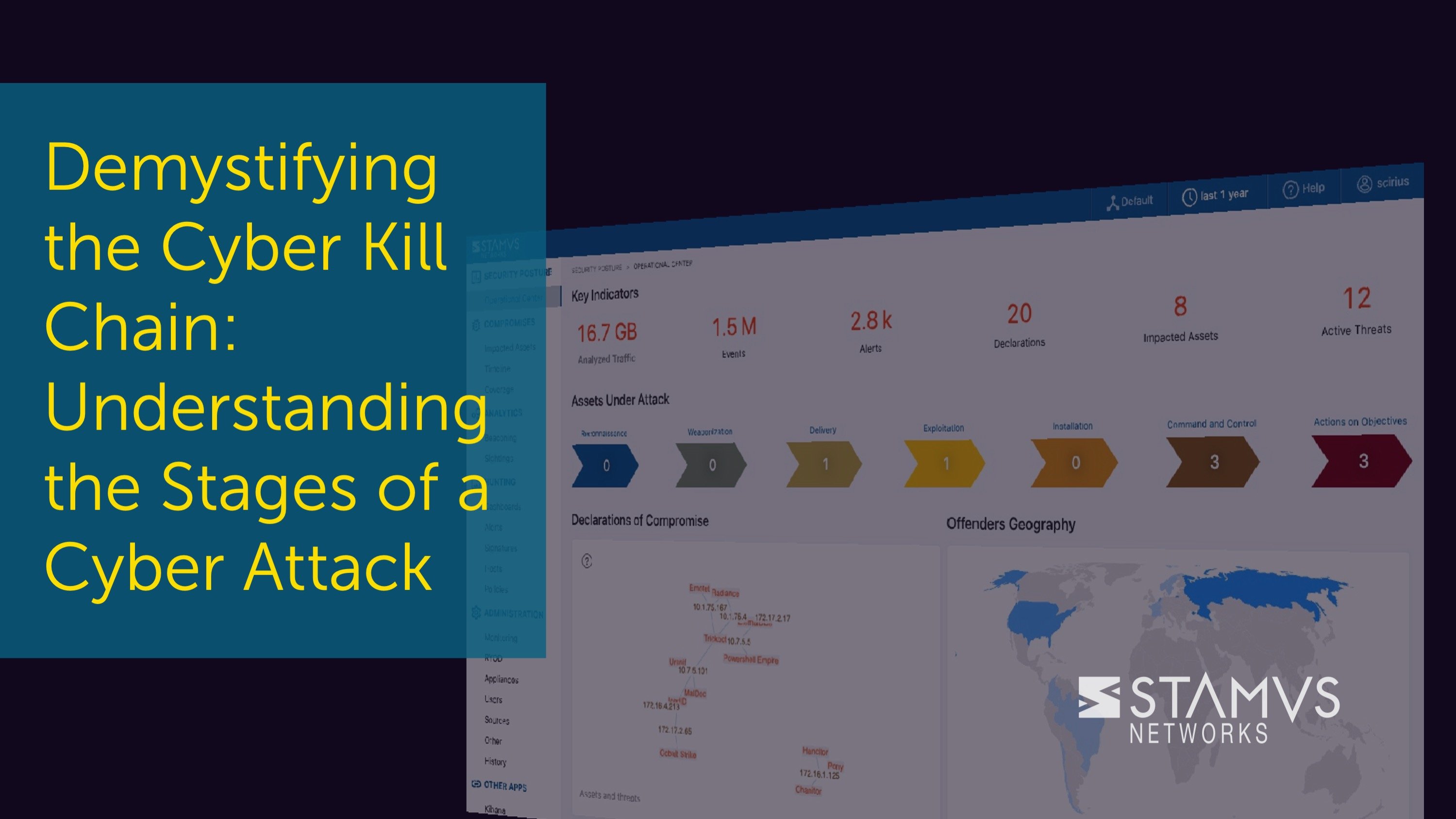
The cyber kill chain is a widely-used framework for tracking the stages of a cyber attack on an...
Endpoint security is one of the most common cybersecurity practices used by organizations today....
Network security plays a crucial role in today's digital landscape as it safeguards sensitive...
Cyber threats are becoming increasingly sophisticated and pervasive, causing organizations to place...
Intrusion Detection Systems (IDS) can be powerful threat detection tools, but IDS users frequently...
This blog describes the steps Stamus Networks customers may take to determine if any of your...
Because cybersecurity teams face numerous threats from bad actors that are continually devising new...
Maintaining an effective security posture is difficult enough for any organization. But for those...
As we celebrate the beginning of another new year, we’d like to take a glimpse back at the news,...
When you already know the specific attacks faced by your organization, then the basic detection...
Intrusion detection systems (IDS) function incredibly well when it comes to making signature based...
This blog describes the steps Stamus Networks customers may take to determine if any of your...
TL;DR
Stamus Networks uses OpenSSL in the Stamus Security Platform (SSP) as well as our open source
Command-and-control (C2) attacks are bad news for any organization. Attackers use C2 servers to...
Intrusion detection systems (IDS) have proven to be a highly effective and commonly used method of...