The cyber kill chain is a widely-used framework for tracking the stages of a cyber attack on an organization. The kill chain enables cybersecurity professionals to better understand and combat cyber attacks and advanced persistent threats (APTs).
What is the Cyber Kill Chain?
The cyber kill chain was originally developed in 2011 by Lockheed Martin in an effort to enhance the visibility into attacks and enrich analysts’ understanding of an adversary’s tactics, techniques and procedures (TTP). It was designed to serve as a framework specifically for defending against more sophisticated cyber attacks — known as APTs — where the attacker spends considerable amounts of time planning and executing the attack. These attacks often involve a combination of malware, ransomware, trojans, phishing, and other threats in order to breach an organization and exfiltrate valuable data.
The 7 Stages of The Cyber Kill Chain
Lockheed Martin’s original framework included 7 stages that most APTs follow:
- 1. Reconnaissance: In this stage, threat actors gather information about their potential targets. The attacker's goal in this stage is to identify any vulnerabilities that they could exploit in order to gain access to the target. This could include information gathered from publicly available sources, social engineering and phishing attempts, or domain spoofing. The more information an attacker gathers in this stage, the more sophisticated the final attack could be.
- 2. Weaponization: Once attackers have collected enough data, they move to the weaponization stage. This is when they begin to craft their attack, creating malware, ransomware, a virus, or a worm that can exploit the vulnerabilities found in the reconnaissance stage. This is also when the attacker might set up back doors that would allow them continued access to the target system in the event their original point of entry is discovered.
- 3. Delivery: In the delivery stage, attackers aim to deliver the weaponized payload to the target. This can occur through various vectors, such as phishing emails, malicious websites, or compromised third-party software.
- 4. Exploitation: Once the delivery is successful, the exploitation stage begins. Here, attackers take advantage of vulnerabilities in the target's systems, networks, or applications to gain unauthorized access.
- 5. Installation: During the installation stage, attackers establish a foothold within the target environment, often by installing backdoors or other persistent methods of access. This is the stage in the kill chain where the attacker officially has a foothold in the target system and can begin taking control.
- 6. Command and Control: Once installed, the attackers establish a command and control infrastructure to maintain communication with the compromised systems and issue commands. From here, the attacker might also begin to move laterally within the network in an effort to increase their access.
- 7. Actions on Objectives: The final stage of the cyber kill chain involves the attacker achieving their primary objectives, which could include data theft, disruption of services, or unauthorized access to sensitive information.
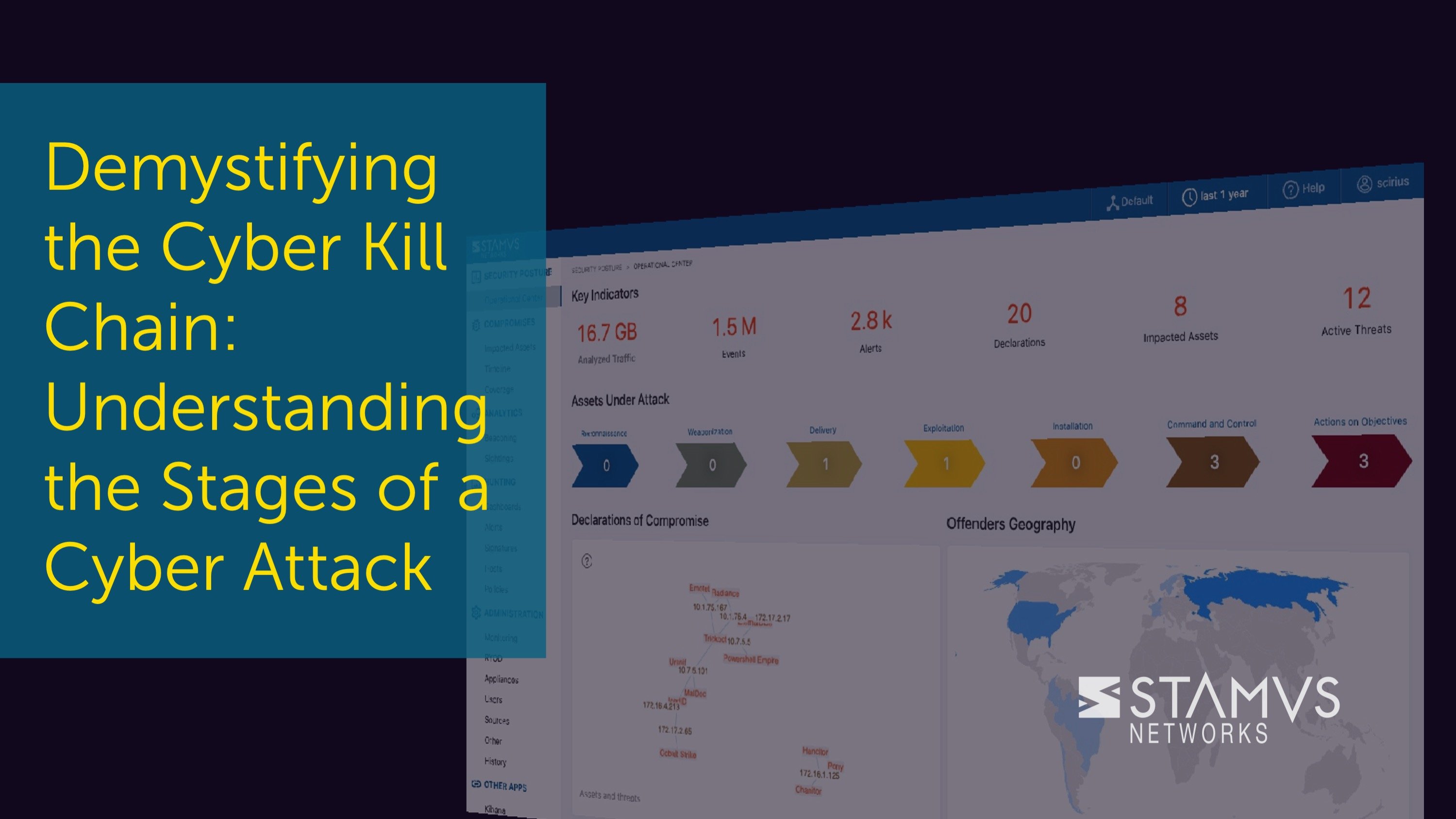
In the following screenshot you can see the number of assets under attack and their progression through the cyber kill chain. This information is on the operational center tab within the Stamus Security Platform user interface. This tab also shows key insights into other important details about the organization’s overall security posture.
It is important to note that the cyber kill chain is not always the path an attacker takes when infiltrating a target. It is possible for threat actors to combine some steps or skip others entirely. Due to the widespread use of this framework, attackers might leverage it to understand how an organization structures their defense, leading them to change their methods.
The Cyber Kill Chain and Stamus Security Platform
Stamus Security Platform (SSP) is a broad-spectrum, open network-based threat detection and response (NDR) system. It provides insights into the progression of an attack along the cyber kill chain. Using high-fidelity threat notifications, called Declarations of Compromise (DoC), SSP identifies each threat and the asset(s) it is impacting. A DoC event includes important information on the threat as well as relevant supporting evidence and context.
DoC events also include a detailed timeline of the threat’s activity on the network and its progression through the cyber kill chain. These insights are invaluable to analysts as they seek to understand not only the severity of a threat, but also when, how, and where that threat penetrated the organization’s infrastructure.
Under the “Timeline” tab in SSP users will see a visualization of the threats impacting their asset(s) and the dates and times those threats were in the different stages of the cyber kill chain.
Understanding the Cyber Kill Chain
Understanding the cyber kill chain is crucial for organizations looking to enhance their cybersecurity posture. By recognizing the stages that attackers go through during a cyber attack, organizations can proactively implement countermeasures and strengthen their defense against advanced threats. Employing a combination of preventive measures along with detection and response enables organizations to significantly reduce their exposure to cyber threats and protect their valuable assets.
Cybersecurity is an ongoing process that requires continuous vigilance, adaptation, and investment. By leveraging the insights provided by the cyber kill chain framework, organizations are better equipped to stay ahead of threat actors and safeguard their assets against evolving threats.