When an organization wants to learn more about the tactics, techniques, and procedures (TTP) used by threat actors across the attack lifecycle, the MITRE ATT&CK (pronounced “attack”) framework is perhaps the most thorough source of information available. MITRE ATT&CK is used by the Stamus Labs threat research team to inform the threat coverage information provided within Stamus Security Platform.
What is MITRE ATT&CK?
To understand what the MITRE ATT&CK framework is, one must understand its history. MITRE was founded as a non-profit organization in the late 1950’s through sponsorship by the United States Air Force. Their purpose was to act as a bridge between the academic research community and government agencies, providing objective research-based opinions and innovations. In 2013, MITRE began to develop their ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) framework. MITRE ATT&CK was released publicly in 2015 and has since become one of the most popular frameworks for understanding attack behaviors.
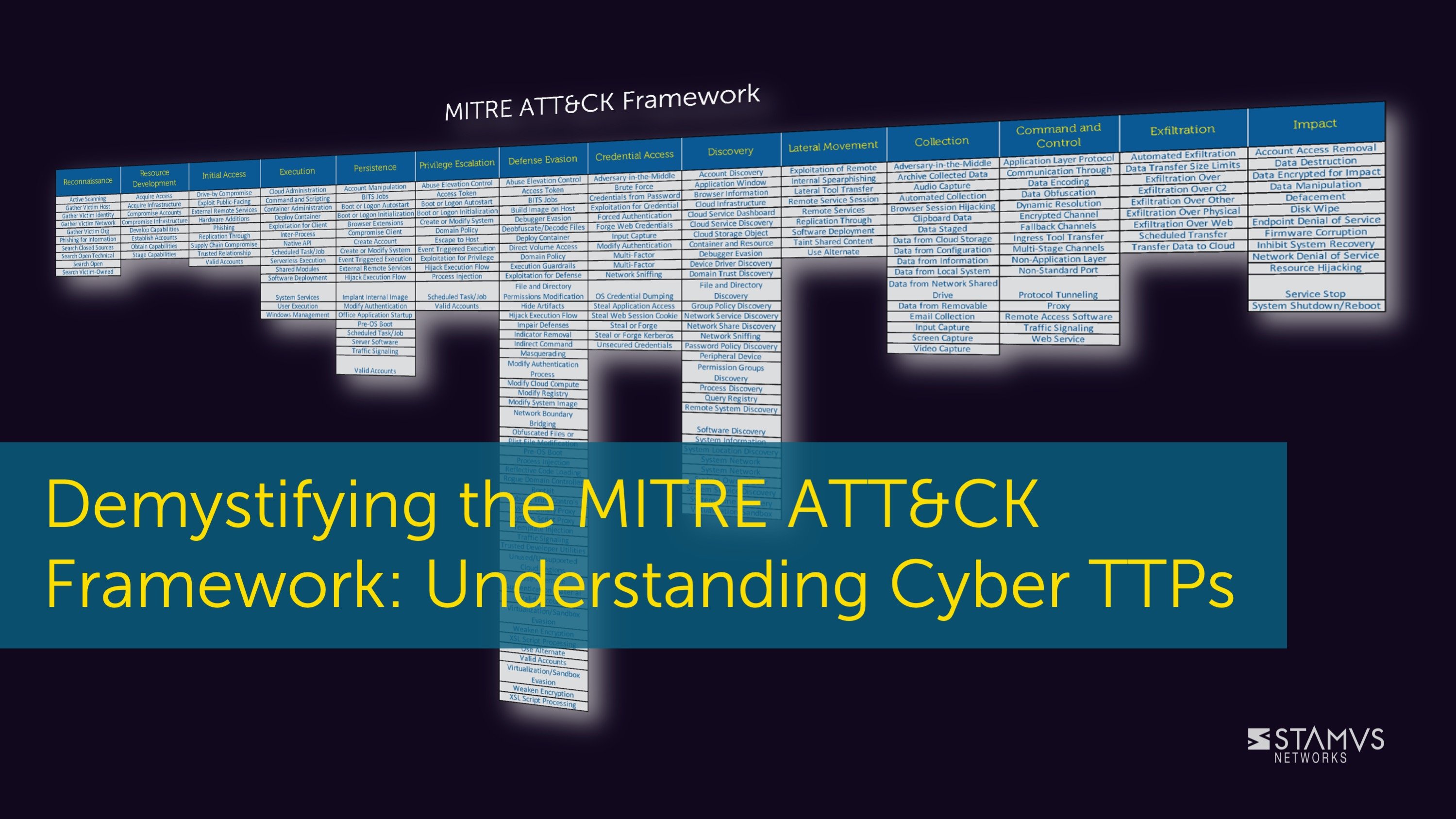
The MITRE ATT&CK Matrix
MITRE provides an enterprise level ATT&CK matrix that includes 14 commonly used tactics and over 227 techniques and sub-techniques. MITRE updates these TTPs regularly, so these numbers increase as new information becomes available.
Tactics are the specific objectives that an attacker seeks to achieve, like lateral movement, command and control, or impact. Each tactic has a set of related techniques, and some techniques are even composed of smaller sub-techniques.
A “technique” is one way that an attacker might achieve their objective. For each “technique”, MITRE provides information on that specific method, including a description, the systems and platforms it pertains to, which adversaries are known to use that method (if known), ways to mitigate the activity, and real-world examples.
MITRE ATT&CK and the Cyber Kill Chain
We recently released another blog post detailing the cyber kill chain. It is important to make a distinction between the cyber kill chain and the MITRE ATT&CK framework because there is some overlap in the vocabulary of these tools. While they do share some descriptive words like “Reconnaissance” and “Command and Control”, there are key differences between the two.
The cyber kill chain details the sequence of events used in most cyber attacks, broken into seven steps that define a typical attack structure. MITRE ATT&CK, on the other hand, is a matrix of techniques that includes information on both the attacker as well as resources for the defender.
These are both highly useful tools and there is great value in using them simultaneously, as they both help to inform each other.
MITRE ATT&CK and Stamus Security Platform
A key feature of the Stamus Security Platform (SSP) is the system’s high-fidelity threat detections, called Declarations of Compromise™ (DoC). SSP includes coverage for hundreds of known threat types grouped into 23 different threat families.
When SSP issues a Declaration of Compromise that can be associated with a TTP from the MITRE ATT&CK framework, the threat event record includes information about that TTP along with other important metadata.
The SSP coverage screen displays a description of each threat and additional resources for analysts to learn more. The vast majority of this information is curated by the Stamus Labs team and informed by the MITRE ATT&CK matrix. See two screenshots of the SSP coverage screens below.
The MITRE ATT&CK Framework: Information is Power
Detecting threats is only part of the battle. Once a serious threat has been identified, organizations must gather all the information they can to understand what happened, how it happened, who did it, and how to stop it. The MITRE ATT&CK framework helps organizations answer some of these questions.
To stay updated with new blog posts from Stamus Networks, make sure to subscribe to the Stamus Networks blog, follow us on Twitter, LinkedIn, and Facebook, or join our Discord.