Exciting news - the OISF just announced that Suricata 6 is now available. This is the culmination of contributions from a number of people and organisations, including a large number of dedicated volunteers. In this blog we will attempt to explain what’s new, why you should care, and how you can begin experimenting with it immediately.
But first, a bit of a history lesson.
Background
Suricata is a high performance network threat detection, IDS, IPS and network security monitoring (NSM) engine. It is open source and owned by a community-run nonprofit foundation, the Open Information Security Foundation (OISF). Suricata is developed by OISF, its supporting vendors and a passionate community of volunteers.
Suricata was started by Matt Jonkman, Victor Julian and Will Metcalf, who set out to develop a true open source detection engine that could not be commercially acquired or sold. With initial funding from a US Department of Homeland Security (DHS) grant, the group established OISF as the not-for-profit owner of the project.
The first version of Suricata was released on December 31, 2008, and it has been continually improved by an active development and user community for nearly 12 years. From its humble beginnings, Suricata grew into a powerful IDS/IPS/NSM and evolved to include full-featured packet capture, scripting, and network security monitoring capabilities that rivals those of dedicated solutions. Suricata has formed the foundation of many successful commercial products and spawned an incredible ecosystem of independent ruleset/signature and threat intelligence providers.
Éric Leblond and I joined the Suricata development team in 2009, and we now serve on the executive team at OISF. Being part of the project has always been an awesome experience and pleasure. It is an honor to work with a great group of OSS-minded professionals and contributors. It has always been amazing to meet, exchange ideas, discuss with hands-on people and organisations from the industry. It is also refreshing to receive so much volunteer help.
After several years, Suricata was gathering momentum. We at Stamus Networks recognized the industry could benefit from a turnkey ready-to-use Suricata-based IDS/IPS/NSM system with its own graphic rule manager, dashboards, and visualizations to showcase the power of Suricata. And in October of 2014, we introduced SELKS 1.0 - a free and open source solution to do just that. We believe SELKS -- now at version 6.0 and containing over 400 visualizations -- is the ideal vehicle to evaluate and experiment with Suricata in your environment. The one of the many unique advantages with SELKS is that it is always running the latest dev version of Suricata.
What’s New in Suricata 6
This week, Suricata 6 introduces a set of new advancements that we explain below.
Support for HTTP/2, RFB , GENEVE and MQTT protocols
Suricata will now automatically decode and parse HTTP/2, RFB, GENEVE, and MQTT protocol traffic and now supports detection rules/signatures written specifically for these protocol transactions.
GENEVE support improves the value of Suricata instances running in the cloud, as it is an encapsulation protocol used in this context. RFB support complements the Remote Desktop Protocol support already available in Suricata, as it is a protocol used by desktop sharing applications such as VNC. MQTT support addresses IoT applications, as it is a standard protocol for IoT messaging.
Each of these protocols is now becoming more commonly used by a number of organisations. For example, according to Wikipedia, “as of August 2020, 48% of the top 10 million websites supported HTTP/2” (Source: https://en.wikipedia.org/wiki/HTTP/2).
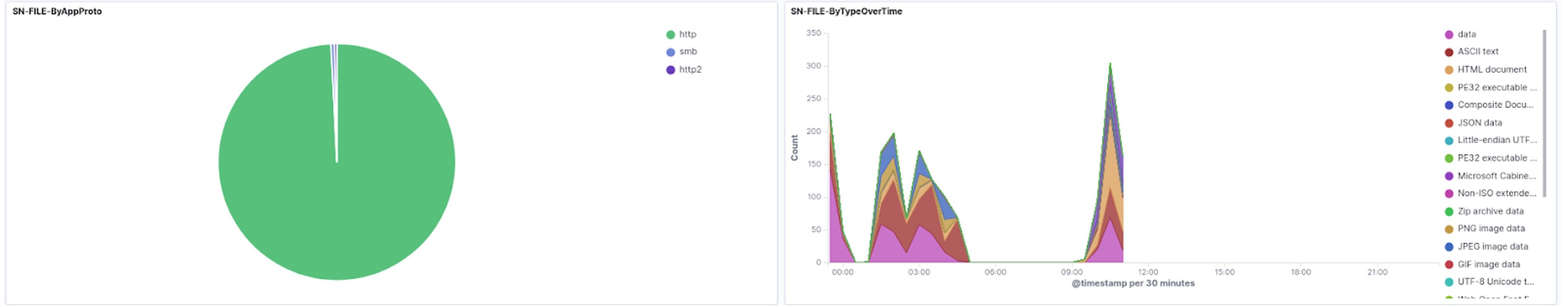
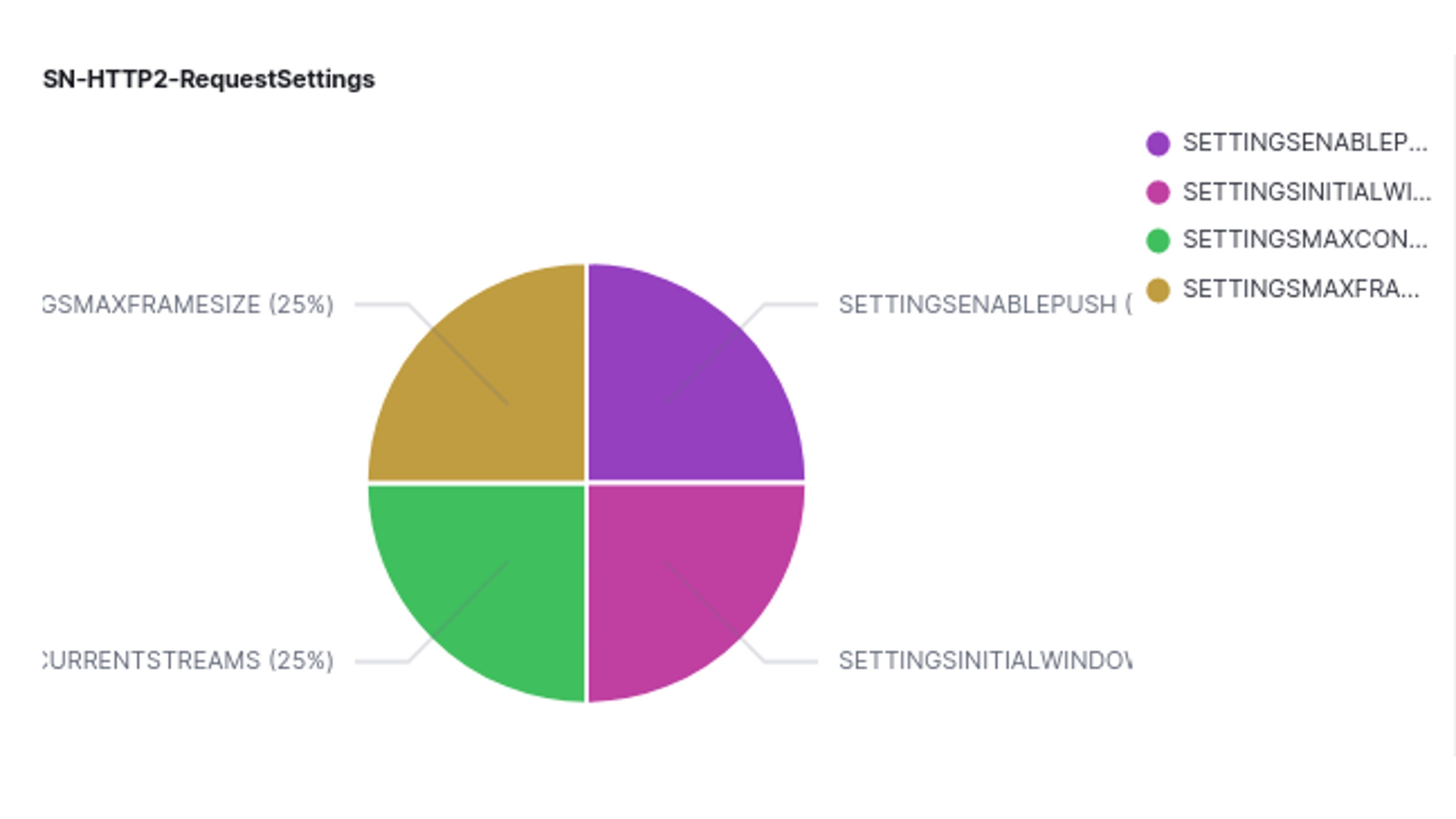
Below are examples of HTTP/2. RFB and MQTT support, staring with HTTP/2:
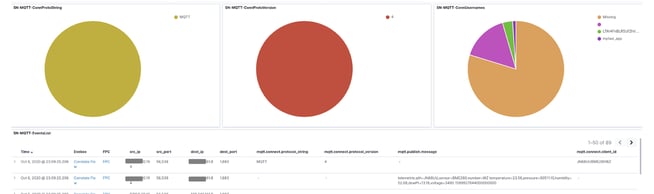
And here is an example of MQTT protocol support
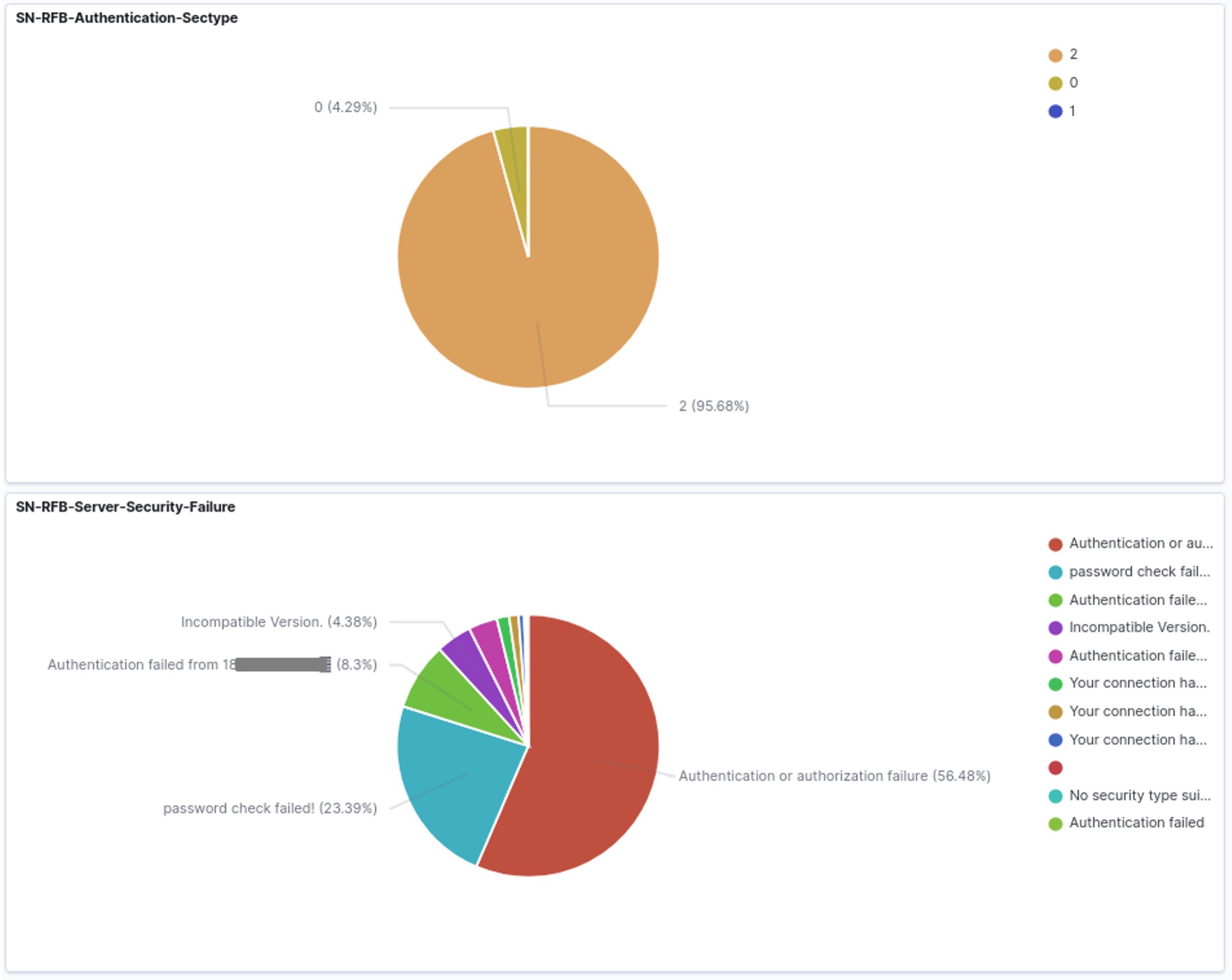
Another example showing some visualisations around RFB
DCE/RPC logging
DCE/RPC is a protocol heavily used for remote procedure calls in Microsoft Windows environment, but is not limited to this environment. It allows a system to run code on another system. And - from a security standpoint - it is often abused for lateral movement.
DCE/RPC was supported by Suricata in earlier versions, but Suricata 6 adds increased support and improvement of DCERPC multi-transaction logging. See https://github.com/OISF/suricata/commit/bab497ab2cfd7ad90f4876840fbfa3bb21426626. This greatly improves logging, detection and hunting possibilities for lateral movement activity.
Greatly improved EVE logging performance
Logging in a single file or logging per protocol in the same file has always been prone to contention that impacts performance and may result in packet loss for high speed network connections (e.g. greater than 10Gbps).
Suricata 6 allows for logging/writing per thread which streamlines and greatly improves performance when logging into eve.json.
This improvement is paired with a new JSON writer system to generate the JSON event before writing them. This change improves the performance of event serialization by 25% over the off-the-shelf JSON library.
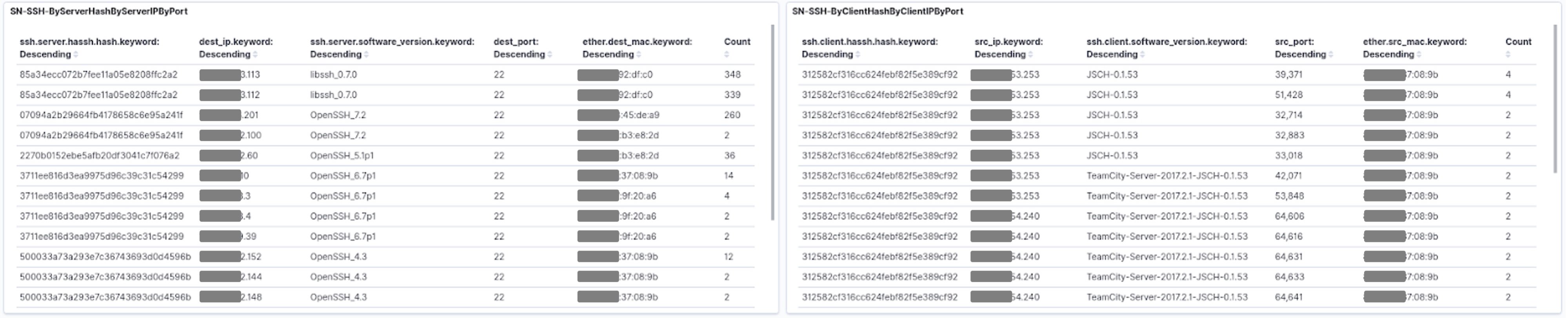
HASSH support
Suricata 6 now supports enhanced detection for SSH-encrypted traffic via support for HASSH network fingerprinting - see https://github.com/salesforce/hassh. Existing SSH client and server logging was really useful but the logged value is a user entry and are thus subject to user spoofing. With HASSH, we identify the implementation which allows security analyst to see patterns used by the various actors.
This further enhances possibilities for detection and hunting of encrypted traffic. See screenshot below.
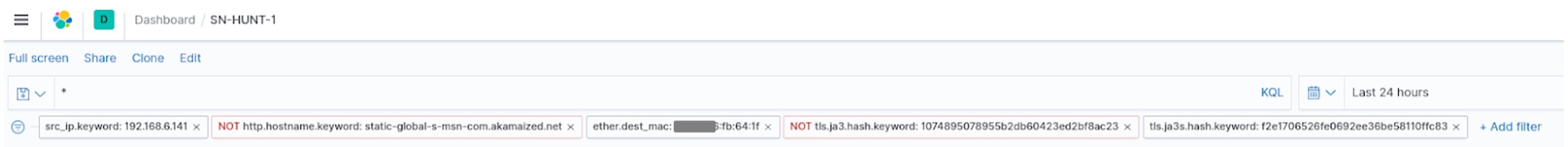
MAC address logging
Suricata 6 also includes a great contribution from volunteers, Sascha Steinbiss and Frank Honza. This was also highlighted by Victor Julien on the “what's new in Suricata 6” webinar. See tweet:
https://twitter.com/alper/status/1313430311758430210
The screenshot below demonstrates the inclusion of MAC addresses in an example filter created in SELKS.
With this new feature, it is now possible to search for hosts based or their physical address, allowing for the cross correlation of IPv4 and IPv6 traffic and addresses used on a single network interface.
General performance improvements
In every release the Suricata team strives to improve any and every aspect of performance as much as possible, because network traffic and protocol additions place more and more demands on the system. Here are a few examples of the many performance improvements in Suricata 6:
The flow timeout redesign:
https://github.com/OISF/suricata/commit/b3599507f4eb891841417575587d690ea13fe6c0
Improved performance in emergency mode
https://github.com/OISF/suricata/commit/611c991f27598b8498d34fb18262de2f280a841a
Try it today using SELKS
As mentioned earlier, we created SELKS to showcase the power of Suricata. And when you download and install SELKS, you are always getting the latest version of Suricata. So, if you are reading this and wish to begin experimenting with Suricata 6, you can download the turnkey SELKS package and begin immediately.
In addition to including the latest version of Suricata, we continually add to the useful capabilities of SELKS. For example, we recently added a number of dashboards and visualizations to the current version available. See https://github.com/StamusNetworks/KTS7
Here’s the link to the complete SELKS ISO images ready to install on a bare metal system: https://www.stamus-networks.com/scirius-open-source
Here’s the GitHub repository with all the documentation and source code: https://github.com/StamusNetworks/SELKS
Acknowledgements
We want to acknowledge the many contributors to the Suricata project and would like to thank the following people for their contributions to this latest release: (as listed on the Suricata site here):
- Zackeus Bengtsson
- Danny Browning
- Pierre Chifflier
- Stephen Donnelly
- James Dutrisac
- Roland Fischer
- Tristan Fletcher
- Frank Honza
- Zach Kelly
- Giuseppe Longo
- Joshua Lumb
- Vadym Malakhatko
- Angelo Mirabella
- Todd Mortimer
- Timo Sigurdsson
- William Stearns
- Sascha Steinbiss
- Jason Taylor
- Emmanuel Thompson
- Antti Tönkyrä
- Xiaofan Wang
- Phil Young






.jpg)
