This blog post details how Clear NDR drastically reduces Mean Time to Detect (MTTD) and Mean Time...
In today’s digital landscape, enterprise networks produce an overwhelming volume of data when...
As all cybersecurity defenders know, visibility into the network is the key to understanding what...
Determining whether or notNetwork Detection and Response (NDR) is right for your organization, and...
One of the new, exciting innovations available with the release ofClear NDRTM U40 is the inclusion...
The rapid proliferation of IoT devices, network devices, and cloud infrastructure has drastically...
As any seasoned security professional will likely tell you, detecting a threat is only part of the...
Over the course of the last decade, Network Detection and Response (NDR) naturally evolved out of...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
Today, we are proud to announce the general availability of Update 40 (U40) - the latest release of...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
The recent global outage caused by an update to CrowdStrike Falcon, CrowdStrike's endpoint...
The recent global outage caused by an update to CrowdStrike Falcon, CrowdStrike's endpoint...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
Most enterprise organizations gather extensive security data from their information (IT) and...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
Tl:DR: A Large U.S. university lacked sufficient visibility into a large segment of its environment...
TL;DR: An American school district needed to monitor over 5000 school-owned student devices, making...
TL;DR: A European managed security service provider seeking to launch an MDR service chose Stamus...
Network detection and response (NDR) is a critical component of a comprehensive cyber defense...
This week we announced that an important new software release Update 39.1 (or “U39.1”) for our...
This article describes the details of the new Open NRD threat intelligence feeds provided by Stamus...
Today I am thrilled to share some incredible news. It is with great excitement and pride that I...
This week’s guided threat hunting blog focuses on hunting for high-entropy NRD (newly registered...
Every day, new Internet domains are registered through the Domain Name System (DNS) as a natural...
One of the unique innovations in Clear NDRTM is the feature known as Declaration of Compromise™...
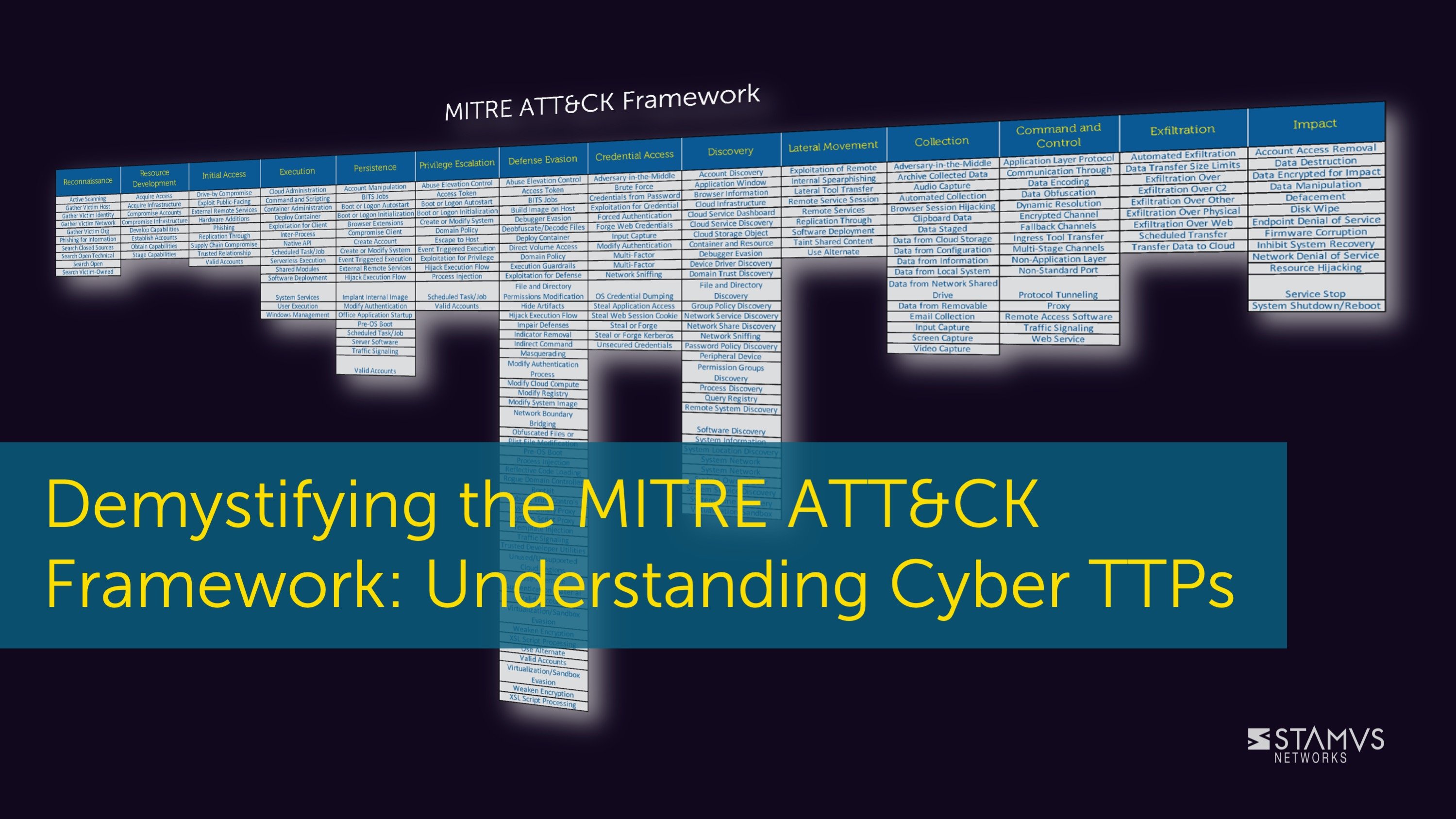
When an organization wants to learn more about the tactics, techniques, and procedures (TTP) used...
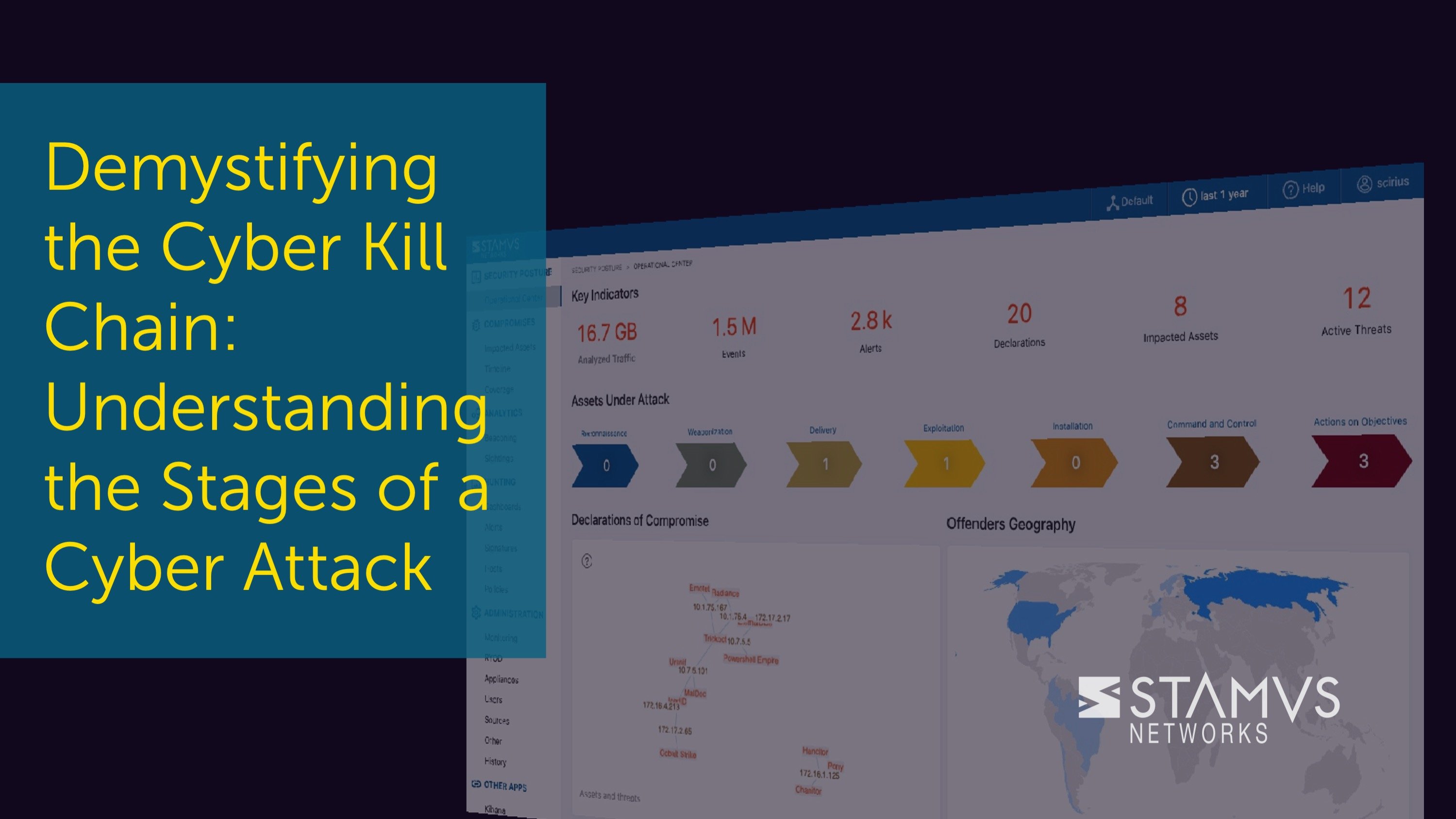
The cyber kill chain is a widely-used framework for tracking the stages of a cyber attack on an...
On 15-June-2023 the OISF announced a new release of Suricata (6.0.13) which fixes a potential...
Network security plays a crucial role in today's digital landscape as it safeguards sensitive...
Threat hunting is a common practice for many mature security organizations, but it can be time...
Today, we announced the general availability of Update 39 (U39) - the latest release of the Stamus...
Stamus Security Platform (SSP) users can now integrate the Malware Information Sharing Platform...
Intrusion Detection Systems (IDS) can be powerful threat detection tools, but IDS users frequently...
In a recent conversation, one of our customers shared their concerns about the use of ChatGPT in...
This blog describes the steps Stamus Networks customers may take to determine if any of your...
This week’s guided threat hunting blog focuses on verifying a policy enforcement of domain...
It is not uncommon to see executable file transfers within an organization. However, it is...
Punycode domains have traditionally been used by malware actors in phishing campaigns. These...
The latest version (1.0.1) of the Stamus App for Splunk adds TLS cipher suite analysis. Conducting...
When you see a domain request from a user/client to a non-local or otherwise unfamiliar or...
This blog describes the steps Stamus Networks customers may take to determine if any of your...
TL;DR
Stamus Networks uses OpenSSL in the Stamus Security Platform (SSP) as well as our open source
Non-local domain requests from the user/client network could signal trouble for an organization....
DNS over HTTPS (DoH) is a network protocol used to protect the data and privacy of users by...
Plain text executables (such as those downloaded from a PowerShell user agent) are often seen on...
This week in our series on guided threat hunting, we are focusing on locating internal use of...
This week’s guided threat hunting blog focuses on hunting for foreign domain infrastructure usage...
This week’s guided threat hunting blog focuses on hunting for Let’s encrypt certificates that were...
In this week’s guided threat hunting blog, we will focus on hunting for Let’s Encrypt certificates...
In this week’s guided threat hunting blog, we focus on using Stamus Security Platform to identify...
This week’s threat detection blog dives deeper into a common type of malware, remote access trojans...
In this week’s guided threat hunting blog, we focus on using Stamus Security Platform to uncover...
In this week’s threat detection blog, we will be reviewing a financially-motivated threat that is...
This week’s guided threat hunting blog focuses on a specific policy violation - the use of...
This week we are taking a closer look at Shadow IT, which is the use of information technology by...
This week’s guided threat hunting blog focuses on policy violations; specifically, violations...
For week 2 of our series on guided threat hunting, we will be reviewing a hunting technique to...
So, what’s next? You’ve had a successful hunt, uncovered some type of threat or anomalous behavior...
In addition to deploying advanced detection technologies, many security teams make threat hunting...
Stamus Security Platform is loaded with features that help security teams leverage network traffic...
Phishing is commonly regarded as the most common and effective way attackers can gain access into a...
In this article, we will review one of the most important and critical phases on the cyber kill...
One of the first network-related indications of a botnet or peer-to-peer (P2P) malware infection is...
In this article I want to highlight one of the tactics used by malicious actors to move within your...
In the first article of this series -- Threats! What Threats? -- I mentioned that my colleague,...
In this series of articles we share hands-on experience from active hunts in the real world. We...
Today I want to give you a brief tour of what’s new in Update 38 of the Stamus Security Platform...
Existing systems that aggregate network security alerts and metadata do not properly detect and...
In the first article of this series –Threats! What Threats? – I mentioned that my colleague, Steve...
We talk often about “threats” and “threat detection” in our marketing materials and in discussions...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
In the previous article of the “Feature Spotlight” series, we discussed how to pivot from IDS alert...
Sometimes, even after extensive training, we forget about important features or ways of using a...
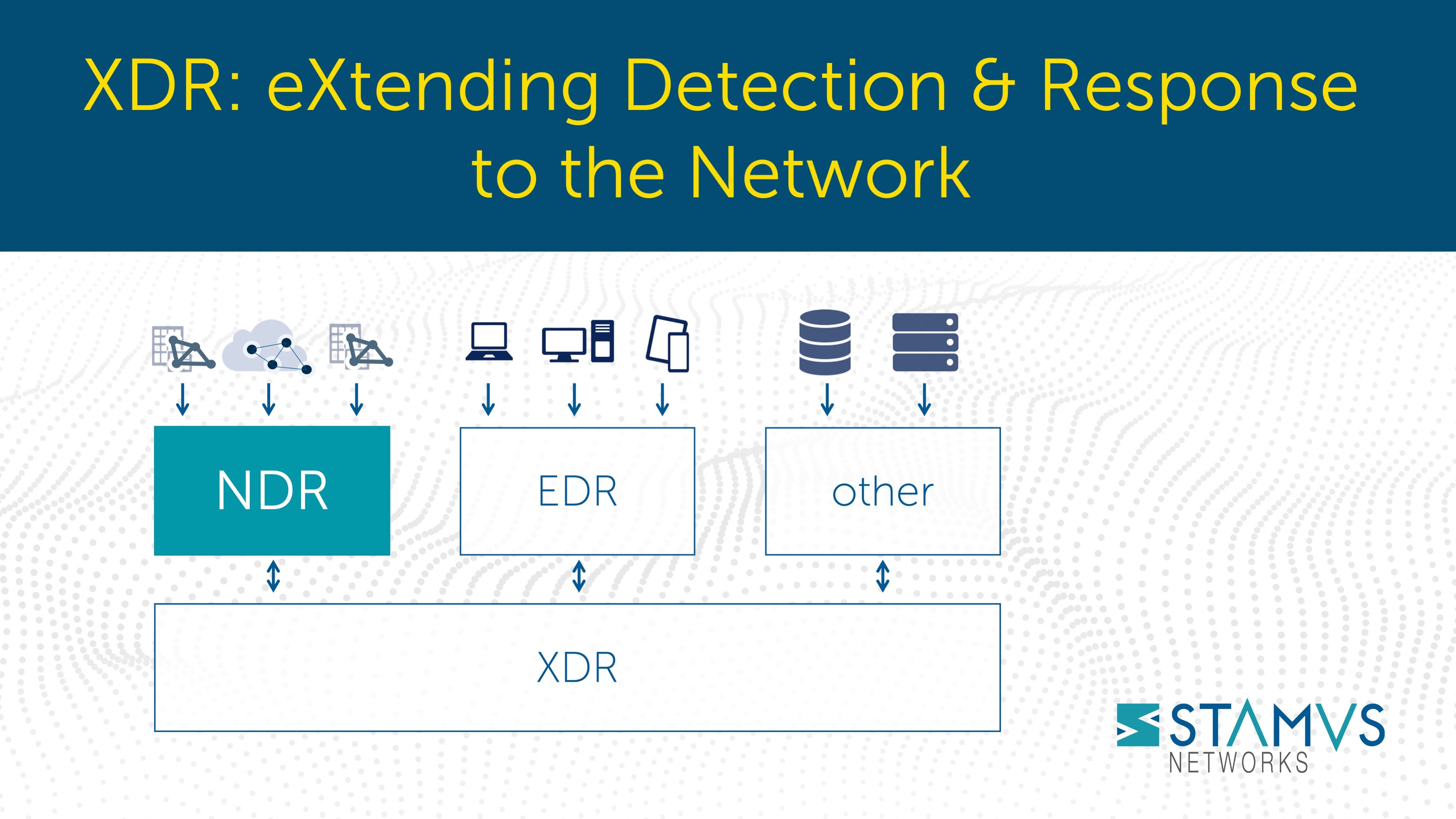
Extended detection and response, or XDR, has generated substantial interest in recent years - and...
On 16 November 2021, my colleague Ed Mohr and I will be giving our second talk entitled “The Case...
On 12 October 2021, my colleague Ed Mohr and I will be giving a talk entitled “The Case for...
When the blue team needs to mount a network defense, they must answer some very common questions:
- ...
In my last blog article, I introduced some of the factors that have contributed to our successes...
Last month, I posted a blog article (Read it here >>) that introduced the new capabilities of our...
In cybersecurity as soon as you stand still, you’re falling behind. Change, whether it’s in the...
Hello and welcome to my first blog article here at Stamus Networks. My name is Phil Owens and I am...
Clear NDRTM helps bank identify threat to its accounting network
With the help of the Clear NDR, ...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
Recently, Stamus Networks introduced outgoing webhook capabilities to its Stamus Security Platform....
Background
As we have previously written, for all Suricata’s capabilities, building out an...
Background
As we have previously written, for all Suricata’s capabilities, building out an...
Background
As we have previously written, for all Suricata’s capabilities, building out an...
For all Suricata’s capabilities, building out an enterprise-scale deployment of Suricata with...
In this series of articles, we will explore a set of use cases that we have encountered in...
Stamus Networks? They are the Suricata company aren’t they? And Suricata? It’s an open source IDS...
As mentioned in an earlier article, organizations seeking to identify cyber threats and mitigate...
Organizations seeking to proactively identify and respond to cyber threats in order to mitigate...
Today we announced the general availability of Scirius Threat Radar (now called Stamus NDR), a...
Every great story begins with the first chapter. And with each new chapter the characters develop...
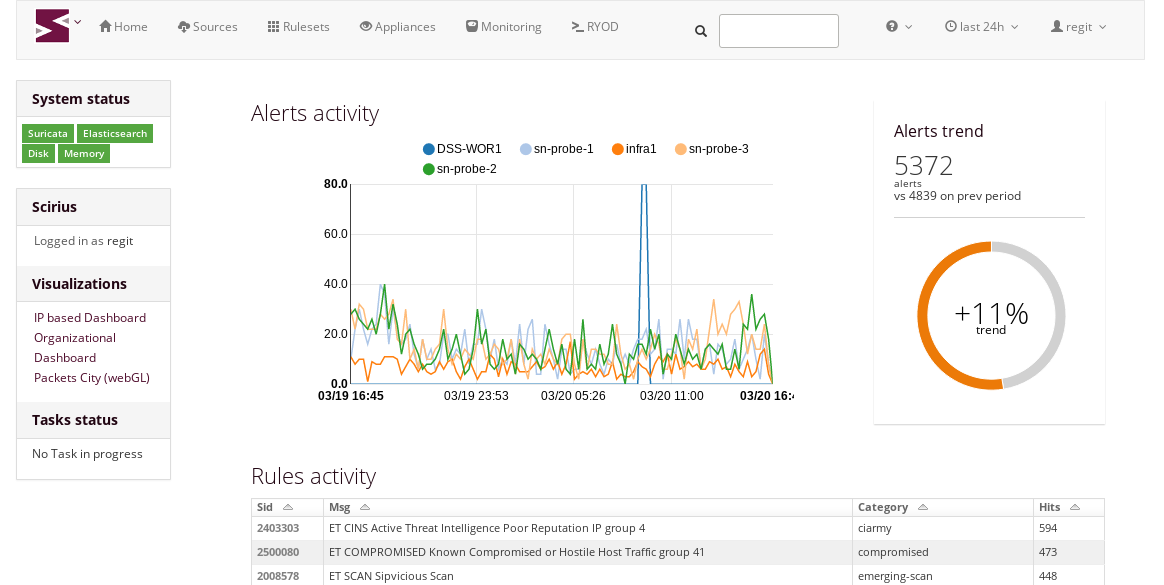
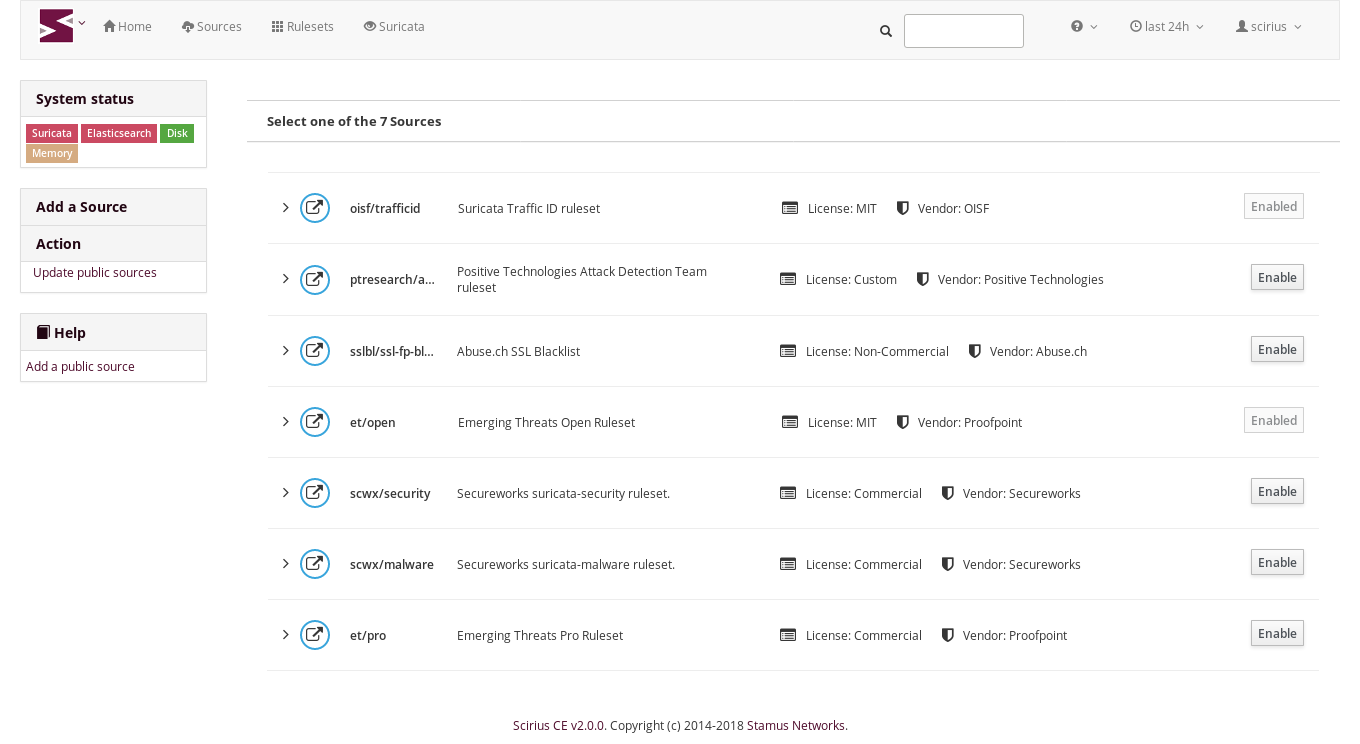
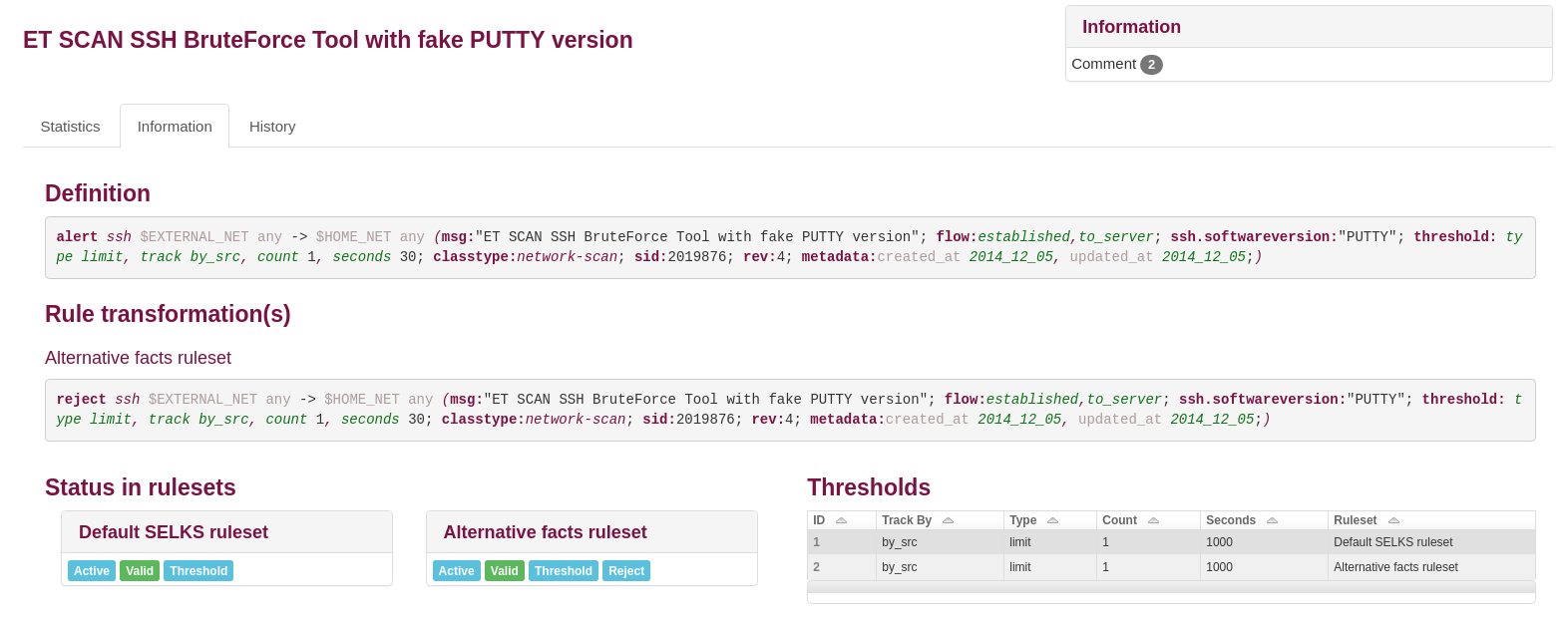
Following the release of Scirius Community Edition 2.0, Stamus Networks is happy to announce the...
Stamus Networks is proud to announce the availability of Scirius Community Edition 2.0. This is the...
Stamus Networks is proud to announce the availability of Scirius 1.2.0. This release of our...