In this article, we will review one of the most important and critical phases on the cyber kill chain - command and control (often abbreviated as C2, CNC, CnC,or C&C). Let’s dig deeper into C2 communications and discuss what they are, how they work, their impact on the network, and how Stamus Security Platform (SSP) can help.
At Stamus Networks we talk about threats often, but we realized that we hadn’t spent much time highlighting what threats we were talking about. This series — Threats! What Threats? — seeks to solve that problem.
What are command and control communications and why are they bad?
Unlike the subjects of previous articles in this series, Command and Control is not a type of threat, but rather a phase along the cyber kill chain. Essentially, Command and Control is the phase that provides attackers with “hands on keyboard access” into a target environment. While malware infects a target system and beacons are used to exfiltrate data or check back with the attackers’ server, command and control communications are the way the attacker gives instructions to malicious programs.
Command and control communications can allow attackers to take over entire networks or create botnets out of individual machines within the target ecosystem. You might have heard about this recently when the United States FBI gained access into the “Cyclops Blink” botnet and scrubbed the malware off of some of the infected devices.
Attacks using C2 servers can begin several ways. First, the attacker must gain access to the target system. This is often done by phishing tactics, security holes in browser plug-ins, piggybacking off of seemingly legitimate software downloads, or in some cases a physical installation through a storage drive. Once communication is established and the machine is compromised, it will communicate with the C2 server to receive further instructions.
This communication often happens by sending signals at regular intervals - malware beaconing - but as detection systems become more advanced, attackers have started communicating in more creative ways. Because many organizations still allow unfiltered access over known ports used for HTTP, HTTPS, FTP, and secure shell (SSH), malware operators have adjusted their methods to tunnel their communications over these ports. Advanced malware may even use SSL certificates, encrypt the communications, and make the traffic masquerade as Web traffic.
The C2 server will then typically instruct the infected system to download additional loaders and backdoors or other remote access tools and then attempt to move laterally through the system to infect additional hosts and avoid detection.
There are three different types of command and control server/client architectures that may be used in an attack. The architecture determines how the infected machine communicates with the server.
- Centralized Command and Control
This is the most common architecture but also the simplest and easiest to detect. In this scheme, all the infected machines communicate with one central server. Because all of the commands come from a single source, the control server's IP address can easily be located and blocked. Some attackers try to get around this by using proxy servers, redirectors, and load balancers. - Peer-to-Peer Command and Control
This model is similar to a BitTorrent file transfer where there is no central server. In this architecture, each infected computer acts as a node in the botnet, passing messages (i.e., commands) to any other node in the botnet, removing the need for a central server. However, this architecture is often used in a hybrid setup where the attacker uses the nodes as a fallback in case the central server fails. - Random Command and Control
This structure is the most difficult to detect and works by sending commands to the infected host or botnet from different random sources. Those sources could be links in social media comments, content delivery networks (CDNs), email, IRC chat rooms, etc. Attackers tend to choose trusted and frequently-used sources to send the malicious commands – heightening their chances of success.
Command and control attacks can enable an attacker to accomplish a variety of tasks:
- Data theft - Sensitive data such as financial documents, proprietary information, or private customer data (including PII) can be copied or transferred to the command and control server.
- Shutdown - An attacker can shut down any compromised machines or in a larger attack shut down an entire network.
- Reboot - The attacker could reboot all the infected machines, causing a disruption in business operations.
- Move laterally - The attacker may schedule jobs and tasks to establish persistence and to move laterally within the network.
- Ransomware attacks - Once access has been granted to sensitive data, the attacker can use ransomware to hold the data hostage until they are financially compensated.
- Distributed denial of service (DDoS) - Once an attacker has established a botnet, they can take down a server or network by flooding them with traffic.
How does Stamus Security Platform help with command and control communications?
Stamus Security Platform (SSP) helps security teams identify command and control servers in four primary ways:
1. C2 Beacon Detection
SSP applies a machine learning algorithm to identify suspected C2 beacons. The system generates a score that helps the security team quickly assess the likelihood that a communication is a malware beacon based on several behavioral factors. The higher the beacon score, the higher the possibility that communication is a potential beacon. By investigating the assets impacted on these beacon profiles, a user can identify command and control server activity based on IP address communications or JA3S fingerprinting.
2. Declarations of Compromise™
When SSP detects that an organization is facing a serious and imminent threat, SSP issues what we call a Declaration of Compromise™. This is the most definitive and high-confidence assertion that SSP can deliver. Technically speaking, a DoC is the association of a single threat impacting a single asset and includes a stateful association of related activity such as when it was first seen, when it was last seen, the killchain phase the threat is in, and so on. For each DoC event, the security team can review the context surrounding the impacted asset(s), including a timeline view with threat events mapped to stages in the cyber kill chain. Because command and control is a phase in the cyber kill chain, users can identify C2 server activity within the DoC interface, including all the contextual information surrounding the attack, its communications with the C2 server, and any information about the server made available in the findings.
3. Suspicious Host Activity Detection via Sightings
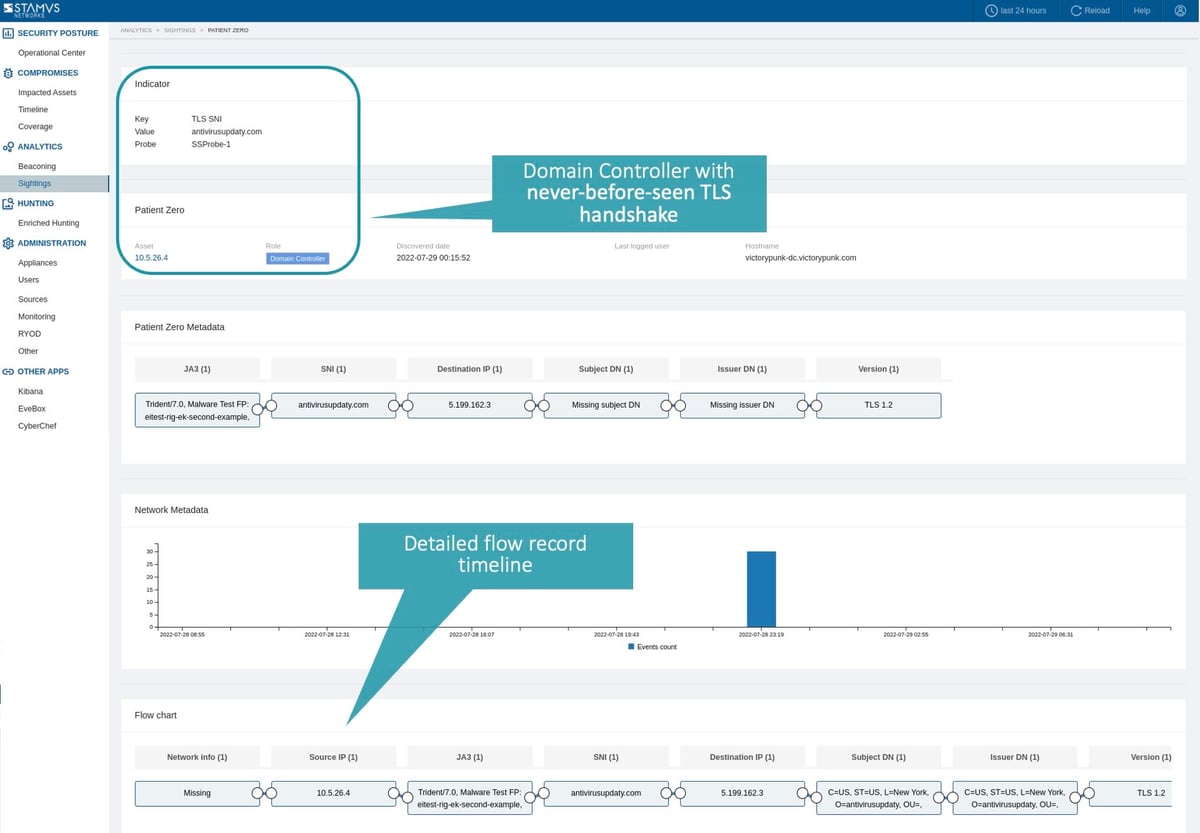
Security teams may uncover C2 activity using one the anomaly detection mechanisms within SSP, called “Sightings”. This anomaly detection algorithm identifies the initial occurrence of never-before-seen artifacts from critical infrastructure, giving security teams a quick view of potentially suspicious activity. These sightings include new connections based on their discovered Host roles - domain controllers, DHCP servers, proxies, printers, etc. Using this approach an analyst reviewing newly discovered servers and communication artifacts can identify C2 activity and the offending server associated with it.
4. Guided Threat Hunting
Stamus Security Platform includes over 100 guided threat hunting filters which enable users to hunt for specific threats, investigate anomalous behaviors, and create automations to escalate or deescalate future alerts based on custom metrics. One of the predefined filters is focused entirely on hunting for alert events that have command and control activity present. Using this filter, a user can quickly identify possible C2 communications and conduct further investigations. Other filters enable users to use MITRE technique detection over C2 channels, as seen in the image below.
Oftentimes, C2 servers are identified in the process of threat detection by first locating specific malware like Remote Access Trojans (RATs) or Advanced Persistent Threats (APTs), detecting lateral movement, rootkits, botnet activity, or the presence of ransomware. By detecting threats early, they can be removed from the network before they ever reach the command and control phase in the kill chain.
The common difficulty that comes with detecting these threats is the sheer number of alerts produced by most intrusion detection (IDS) or network security monitoring systems (NSM). With such a high volume of alerts – sometimes hundreds of thousands – occurring on a daily basis, it can become exhausting to find the handful of indicating threats that actually designate a true positive.
Thankfully, SSP uses numerous detection and prioritization algorithms that silence the noise of the classic IDS alert cannon and escalates only the most serious, imminent threat indicators. By providing Declarations of Compromise™, SSP gives security teams high-confidence events with extensive supporting evidence and attack timelines.
The StamusLabs team is continually updating SSPs detection capabilities, and new covered threats and detection methods are being added on a daily basis. In fact, as of publication time, SSP currently ships with 8034 detection methods for identifying C2 communications. To get an idea of the various coverage areas, see the screenshot below.
More information on Stamus Security Platform
Hopefully you’ve gained a greater understanding of what command and control servers are, how they affect your network, why they are harmful, and some of the many ways our network detection and response platform can detect their use. Now, when you see the terms “command and control,” “C2,” or “CNC”, you’ll know exactly what we are talking about.
If you would like to see a live demonstration of how Stamus Security Platform detects command and control communication or want to discuss how it could help you detect and respond to threats in your network, please click on the button below to request a demo.







