This week we are taking a closer look at Shadow IT, which is the use of information technology by employees without the organization’s approval. We are going to learn what Shadow IT is, why it can be harmful, and how Stamus Security Platform (SSP) can help.
At Stamus Networks we often talk about threats and threat detection, but until recently we haven’t spent much time describing those treats in any detail. This series - Threats! What Threats? - seeks to fix that by covering a different threat each week and sharing how SSP helps security teams detect these threats on your network.
What is Shadow IT and why is it bad?
Shadow IT can be presented in multiple ways. In the simplest terms, it is the use of systems, software, devices, or services without explicit approval from an organization’s IT department. Often Shadow IT is not installed and operated with malicious intent, but rather in an effort to improve productivity.
Unfortunately, the use of unapproved technology on the organization’s network poses significant security risks by potentially introducing new vulnerabilities and attack entry points. IT teams wish to control technology deployments for a number of reasons.
For example, the organization needs to control access to sensitive information and the systems where it is stored. In addition, hardware and software must be maintained and patched regularly to ensure their vulnerabilities are minimized.
When employees deploy unapproved outside systems, they introduce a greater risk of malware, ransomware, an outsider impersonating an employee gaining access into the network.
Often employees deploy Shadow IT because they wish to use technology that makes their jobs more efficient than that which is approved by the organization. In other cases, employees find their organization’s security policies cumbersome, so they opt to use alternative systems that circumvent these policies without notifying the IT or security teams.
Not all Shadow IT is inherently dangerous. However, certain applications like those for file sharing and remote storage can lead to unintentional leaks of sensitive data. Another common example of Shadow IT that can lead to a data leak occurs when employees send proprietary work documents to their personal email accounts so they might work on them from their home.. This seemingly-noble action exposes sensitive data to networks that can’t be monitored by an organization’s security team.
Other examples of Shadow IT include:
- Creating cloud workspaces using personal accounts or credentials
- Deploying unapproved systems (on-prem or in the public cloud) to support “skunk works” software development
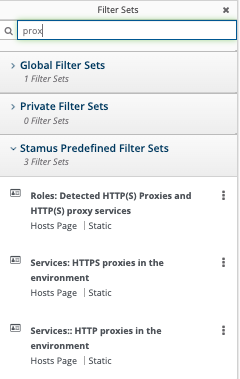
- Using an unauthorized proxy to bypass the official proxy gateway in order to gain unrestricted application downloads
- Using productivity or project management apps like Trello, Asana, Notion, or Evernote without approval
- Conducting work related communication on messaging platforms like Slack or Zoom
- Purchasing software-as-a-service (SaaS) applications without IT team approval
How does Stamus Security Platform help with Shadow IT?
Stamus Security Platform (SSP) is a response-ready, broad-spectrum, and open network-based threat detection and response (NDR) platform helps organizations detect threats faster with greater levels of informational context. Stamus Security Platform is highly effective at automatically detecting serious and imminent threat events on the network, escalating the highest priority (and highest confidence) ones into Declarations of Compromise™, and summarizing all the relevant details about the incident so the analyst can quickly get to patient zero.
When it comes to Shadow IT, security teams can use the SSP Enriched Hunting interface to proactively uncover policy violations, unauthorized proxy applications, unauthorized ftp usage, and more. SSP provides users with over 100 guided threat hunting filters with numerous options to search for policy violations and other common signs of Shadow IT.
Here are a few examples of Shadow IT related filters:
Unauthorized proxies may be found using one of the three proxy-related guided threat hunting filters:
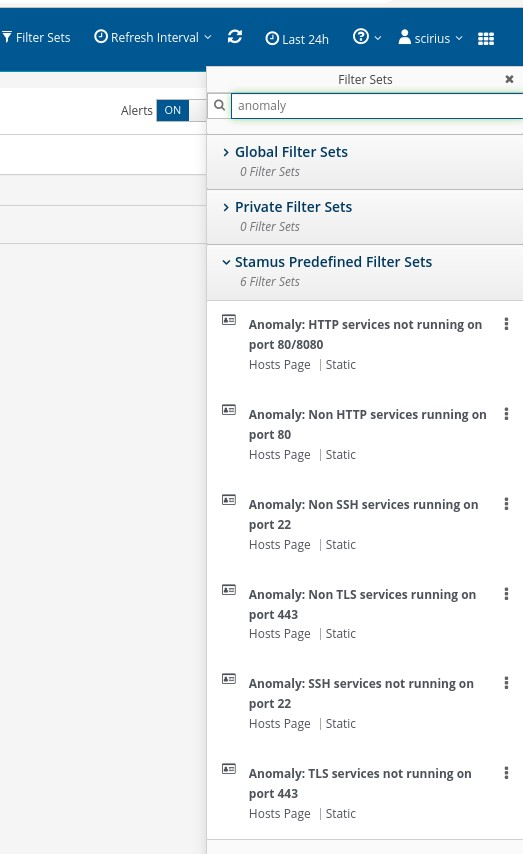
Analysts can use one of the many anomaly filter sets to identify unusual services or unusual ports running on the network.
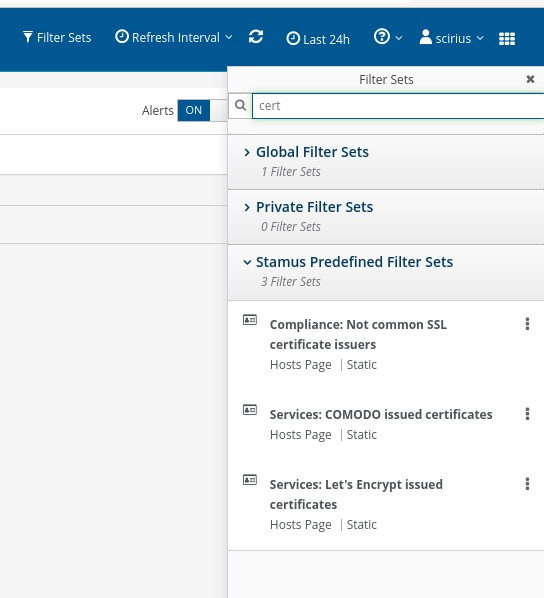
Unauthorized servers and applications are often running with rogue SSL/TLS certificates. To help analysts identify these, SSP includes several filters to spot certificates from issuers .
Automating and Escalating Shadow IT Detection
Because every organization defines “Shadow IT” differently, SSP allows security teams to automate and escalate any of these hunting filters into what we call a “Declarations of Compromise™” or DoCs. SSP includes built-in DoC detections for hundreds of serious and imminent threats identified by our threat research team at Stamus Labs.
Users also may use the DoC construct to escalate and automate threats that are specific to their organization. A custom DoC is an automated detection logic based on the user’s filter criteria that can be applied to historical data and future network traffic to automatically identify activity.
For more information on how to create a DoC from a hunting filter, please check out this recent blog, entitled “After the Hunt” (https://www.stamus-networks.com/blog/after-the-hunt).
By actively assessing the presence of Shadow IT on their network, security teams can minimize the risk that their organization and its employees face. Even though not all Shadow IT activities are dangerous, it is important that their presence is known so that the risk they pose can be managed effectively.
We detailed a very specific Shadow IT case study in this “Uncovered with SSP” blog from last year: https://www.stamus-networks.com/blog/uncovered-with-ssp-shadow-it
More information on Stamus Security Platform
Stamus Security Platform (SSP) covers thousands of different threats, and the Stamus Labs team adds new coverage areas daily. By detecting different types of threats in different ways, SSP gives users the ability to efficiently protect their organizations whether the threat comes from an external source or from their own employees.
To learn more about SSP and see its ability to detect on your network Shadow IT for yourself, click the button below and schedule a demo.







