In this series of articles, we will explore a set of use cases that we have encountered in real-world customer deployments of our network detection and response solution, Clear NDRTM. In each case we work to explain what we found, how we found it, and why it matters.
Background
Earlier this year the MoDi RAT was recognized by CISecurity in its top 10 Malware list. https://www.cisecurity.org/blog/top-10-malware-may-2020/.
Recently I had a regular check up call with a colleague from a financial institution customer of ours where we detected a dangerous instance of MoDi RAT on their network. Our setup there is pretty traditional with network deployments in a headquarters office, datacenter location, and multiple branch offices.
The customer has a classic network and application infrastructure with lots of local and cloud services, customer facing applications and frequent changes in network traffic patterns. They deploy a solid defense in depth strategy with security at all layers and all activities being monitored. All their firewalls, security gateways, endpoint, and single sign-on installations are with well-known security vendors representing a pretty substantial investment.
Their Stamus Networks deployment consists of:
- 1x Clear NDR, integrated with an existing external Elastic store cluster
- 4x Clear NDR Network Probes (some Stamus hardware and others virtual)
- Threat intelligence from Proofpoint ETPro, Scirius Threat Radar, and custom rules
- Custom policy definitions based on metadata, advanced filtering, and classification
- Organizational context enabled
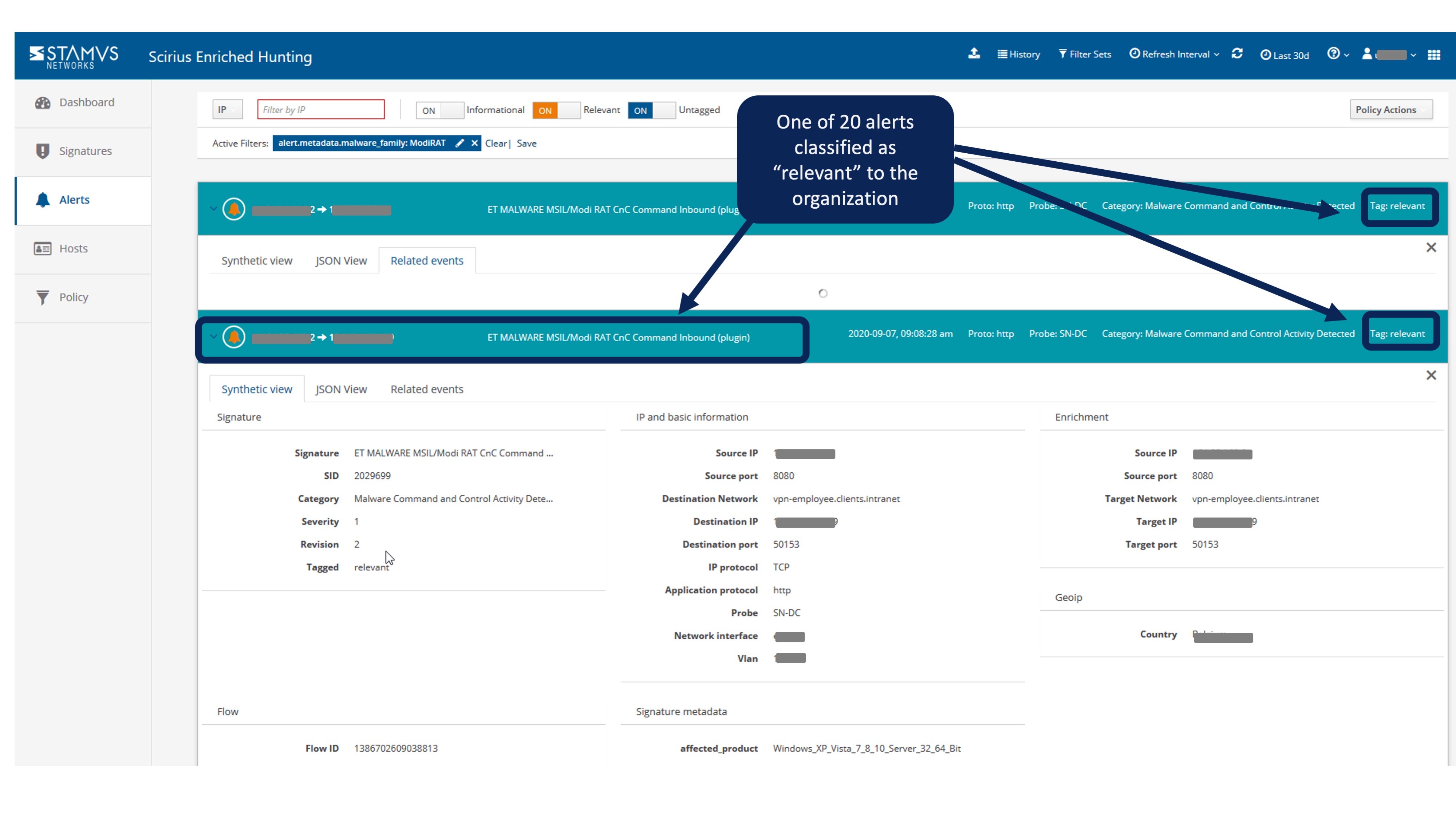
As part of a proactive daily process, the financial institution’s security team hunts for threats by reviewing a handful of events that Clear NDR has automatically classified as “relevant” to the security posture of the organization. Additionally, the system allows the security team to proactively hunt for potential threats presenting all related data available on the same screen to make a fast decision for action.
Incidentally, these classifications go beyond the traditional “known bad” emails/alerts containing minimal IP data. Rather the system is trained to review complex combinations of correlated indicators, such as signature event, protocol transactions and logs, user agents, organizational network context, host id, user id, among others and classify them as “relevant” or “informational”.
What we Found and How We Found It
In this case, the discovery was made easy as we were presented with only 20 “relevant” alerts to review from the past 24 hours. By way of comparison, the system observed and captured over 500 million events over the same period. For example, in this particular deployment, SMB protocol versions, variations and logs alone generated over 100 million events per day.
Out of those 20 events, one especially grabbed our attention - an IDS event (an ETPro MALWARE rule) triggered by a visit to a Wordpress blog page after a Google search and its associated flow events, http transactions along with the organizational data.
Here's what that looks like in the Enriched Hunting console.
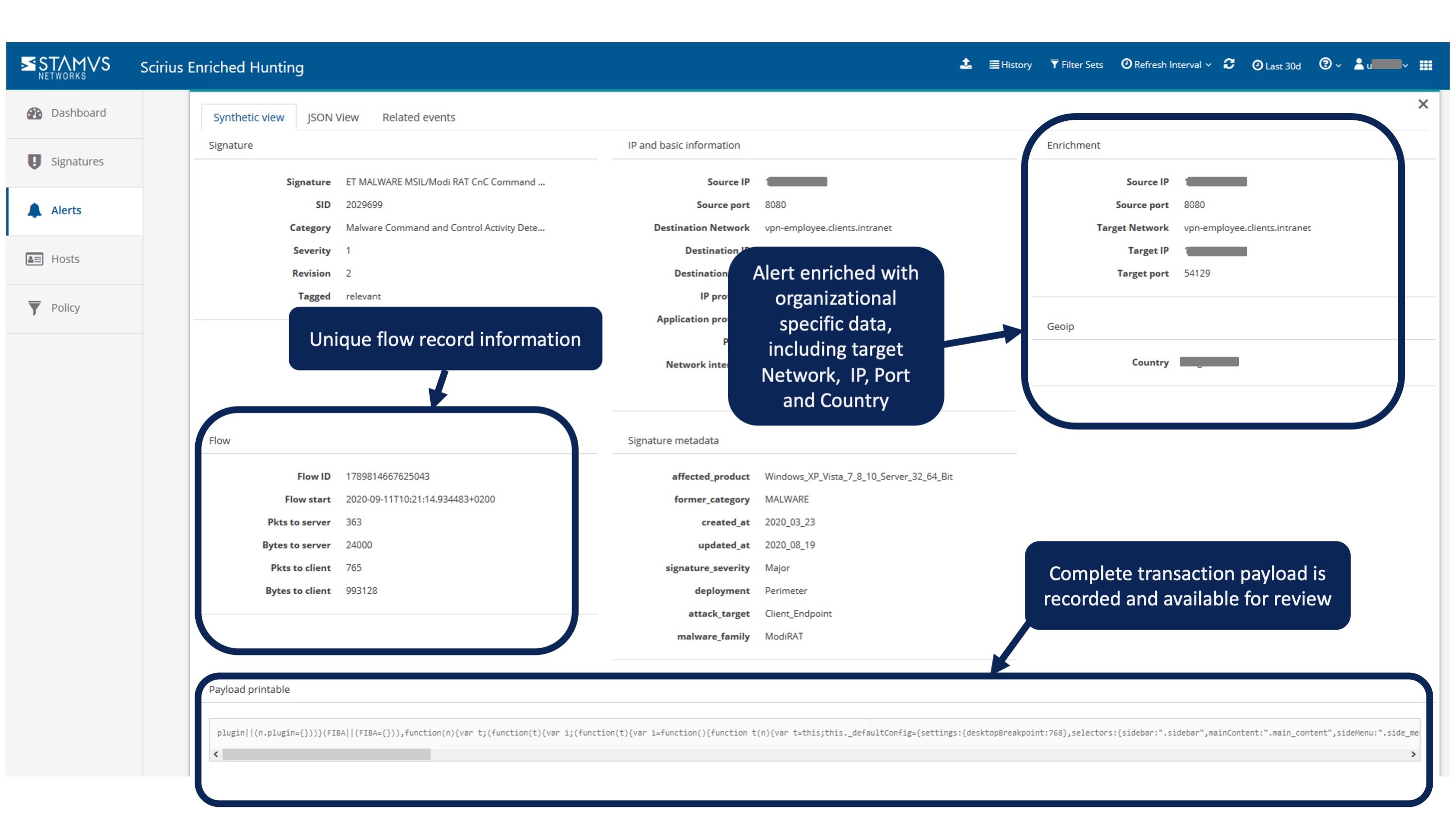
We were able to quickly identify unusual connections from certain parts of the organization's network - a particular user and device working remotely - unusually communicating with SMB servers and then separately with HTTP servers in patterns never seen to date. All of this information and context was available from a single click from this original screen.
The two screenshots below detail some of the event and enrichment data we used to confirm this threat. 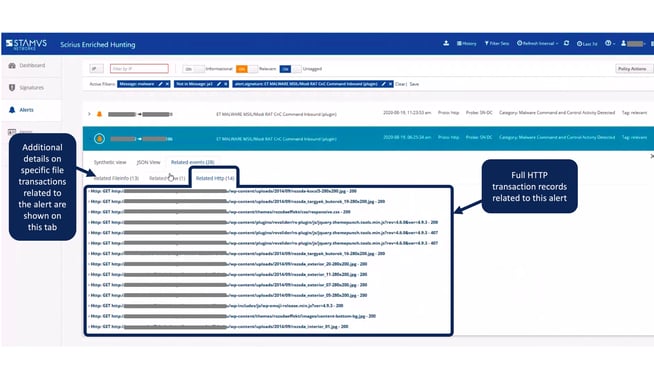
Detection was not based on an AI-based anomaly, nor because the IP address was contained in a threat intel feed, nor because an endpoint security system triggered an alarm, nor because of geoIP location uniqueness. In fact, the blog, user, and the hosting company were all based from the same city.
Instead, we found it quickly through proactive review of threats that Clear NDR had automatically tagged as “relevant” to the financial institution. The automatic tagging criteria was based on organization-specific metadata contained in standard policy definitions that Clear NDR applied to the live network traffic.
Naturally, we also needed to consider the possibility it might be a false positive. In this case, the evidence provided by Clear NDR proved this to be an actual communication between a MoDi RAT infected Wordpress blog page and the user’s PC in the organization.
A Closer Look
The classification of those events was based on a policy that included a combination of network name, metadata, threat intelligence / signature, application protocol, organizational data filtering, wildcarding and tagging of events sequences - all taking place at the point of ingestion in the network probe in real time.
That made possible to define policy actions that helped the active hunting by automating:
- Communications specific protocol data
- Organizational context
- Metadata
- Thread intelligence
- Self learning host specific assets fingerprinting
- Relevance into the events
The team passed along the information to the endpoint security team who opened an incident investigation. The two teams maintained a continuous dialog during the investigation, with the network security team's providing additional evidence including:
- Username and which endpoints the user has been seen logging into
- Various IPs, domains, web servers, urls, user agents, and tls agents
- All services relevant to the discovery
- Future network activity and connections that are of interest to internal systems.
The investigation is ongoing as the teams continue to monitor for additional activities. And the owner of blog/hosting site was notified so they could also take appropriate remediation actions.
Why this Matters
In this case, no other system among the customer’s security toolkit was able to detect the threat. They had a network security gateway, a firewall and an endpoint detection and response (EDR) in place - all of which missed it. This is a great example of how critical network based detection mechanisms can be to a defense-in-depth strategy, when done effectively.
This example also reinforces the point that while automation is essential to streamlining the detection and response process, it is crucial that the analysts also have access to all the evidence needed to proactively investigate and confirm the incident.
Threats such as the likes of MoDi RAT are unpredictable and have the potential to do tremendous harm to an organization. Cached connections, stored credentials, permission rights and such can provide visibility to the threat actors that can be exploited further - all going completely unnoticed by the users.
Often a foothold of one threat carrier can involve another actor/malware to further breach the organization inside.
Ready to learn more?
Hopefully this gives you a taste of how Clear NDR can help security teams know more, respond sooner, and mitigate the risk to their organizations. If you’d like to learn more about optimizing your network detection and response and how it might help your organization or schedule a live demonstration, please click on the link below to contact us.