In this series of articles, we explore a set of use cases that we have encountered in real-world customer deployments of our network detection and response solution, Clear NDRTM. In each case we work to explain what we found, how we found it, and why it matters.
Background
We recently made an interesting discovery while helping a customer understand the advanced hunting capabilities of Clear NDR. The customer is a large financial institution with vast datacenter and cloud based resources and a substantially-remote workforce. Their web and mobile applications provide numerous services to the public and government.
In their environment, many of the clients have short IP leasing times, with most devices changing their IP address every 30 minutes. This makes it nearly impossible to lean heavily on IP addresses for threat detection. So, we were going to need to use a different approach. In addition, their network traffic consists of massive cross communication between datacenter and cloud based services.
They manage a broad security infrastructure, deploying numerous security solutions from the industry’s top security vendors.
Their network security solution from Stamus Networks is deployed with a mixture of physical and virtual probes along with the hunting and Clear NDR features.
What we Found and How we Found It
While demonstrating a new detection mechanism in Clear NDR with the customer, we discovered that a laptop belonging to a trusted member of the infrastructure team had unintentionally installed an adware program. The agent appeared to change its objectives, and was now attempting a spyware-like exfiltration.
The new detection mechanism in Clear NDR - called dynamic dataset - continuously evaluates connections and traffic patterns for DNS server requests, encrypted connections, hosts, HTTP user agents, usernames, and other protocol attributes in order to identify new values, never encountered. When combined with the knowledge of an organization's critical assets, this “not seen before” event can be used to detect anomalies and otherwise unknown threats.
How it Happened
A few days after enabling the new feature in Clear NDR, we noticed that the system was highlighting unusual communication sequences. Among the hundreds of millions of analyzed events, a specific new/unknown communication began appearing that had the following characteristics:
It highlighted numerous communications (previously unknown) coming in from the same organizational area with the following characteristics:
- To new domains and hosts
- At times it was repetitive
- It was blocked on the local firewall
- It was coming from the PC belonging to a datacenter floor manager
The Challenges
The concept of highlighting unusual data flows is not new. And it can generate an extraordinary amount of noisy events and is problematic if not handled properly. For example, the newly discovered activity can be triggered by a number of behaviors such as a DNS request to an encrypted connection or a DNS request over HTTPS (DoH) DNS over TLS. There are constantly changing and dynamic public cloud services available too. Here, there are many EDR/AV solutions that use DNS tunneling for regular updates/sync etc making detections like this appear to be false positives.
What is important here is to not rely on one factor alone. In this case Clear NDR allowed us to pinpoint everything very quickly based on a set of features combining multiple metadata factors, such as: flow data and size, protocol logs, organizational information, communication age.
Clear NDR provides the user with the tools to take this combination of factors into consideration, including auto classification and alert triage. So we were able to quickly filter out through those hundreds of millions of events and zoom right in on the trusted user belonging to a trusted infrastructure team.
At first glance it looked like the communications were blocked by the firewall, making it appear as though it was successfully blocked and harmless. However, Clear NDR highlighted the communication coming from a laptop currently inside the organization trying to get out. Imagine if this laptop moves outside the network - to a public WiFi in a coffee shop somewhere downtown, for example. This spyware would likely make similar exfiltration attempts. And this time it would be successful.
As we look more closely, we will want to answer some really important questions:
- What is it?
- Who is it?
- What does the data look like?
- What is it trying to do ?
The answers were easy to come - in just a few clicks - by using the enriched hunting capabilities of Clear NDR.
Here are some forensic logs and detection evidence we can share.
Highlighted “Not Seen Before” communications
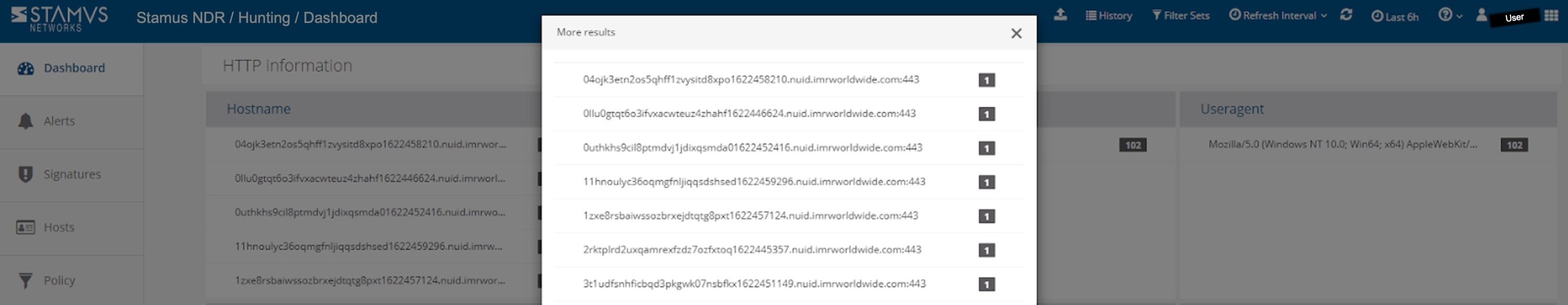
The enriched communications data
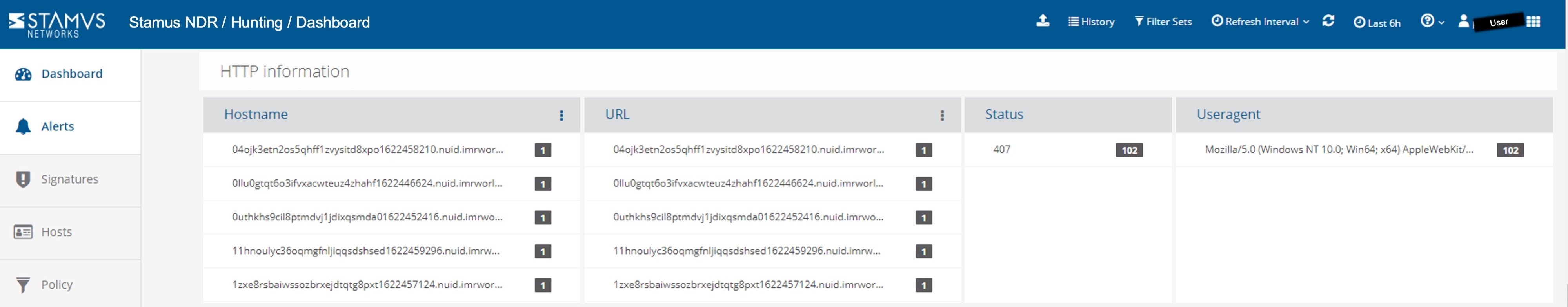
A more detailed view
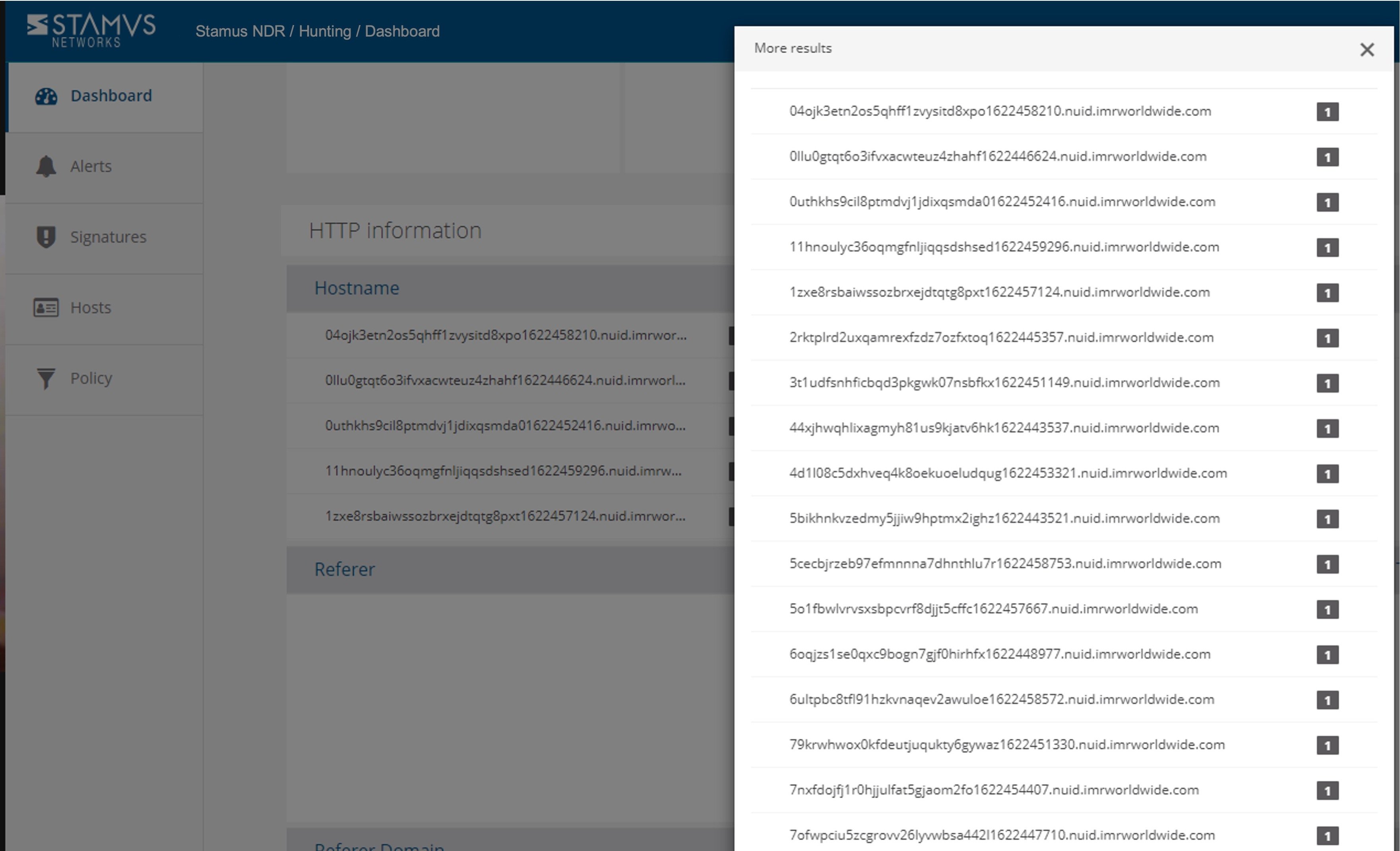
Here you can see that the attempted transfers used periodic time windows when it tried to exfiltrate the system and personal data.
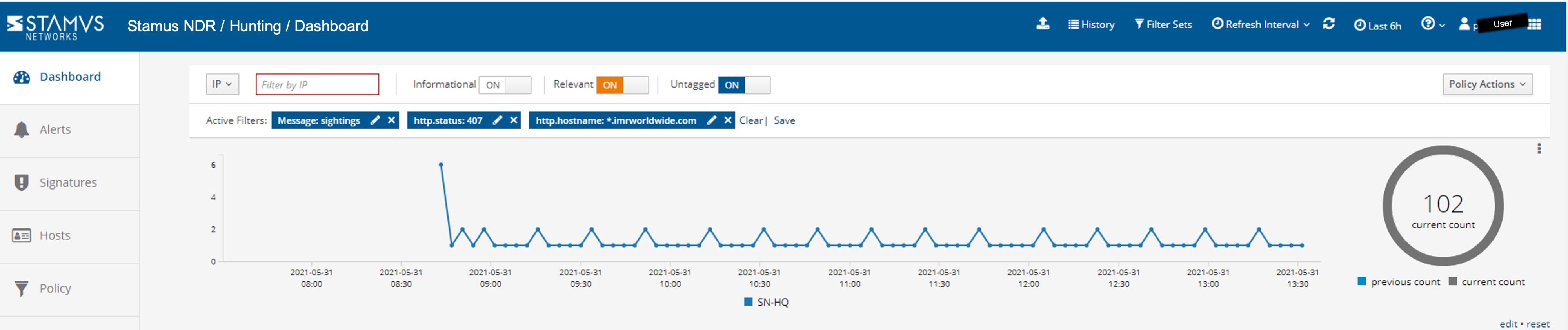
The user and relevant organizational role were quickly identified (User A, job position: datacenter floor manager.)
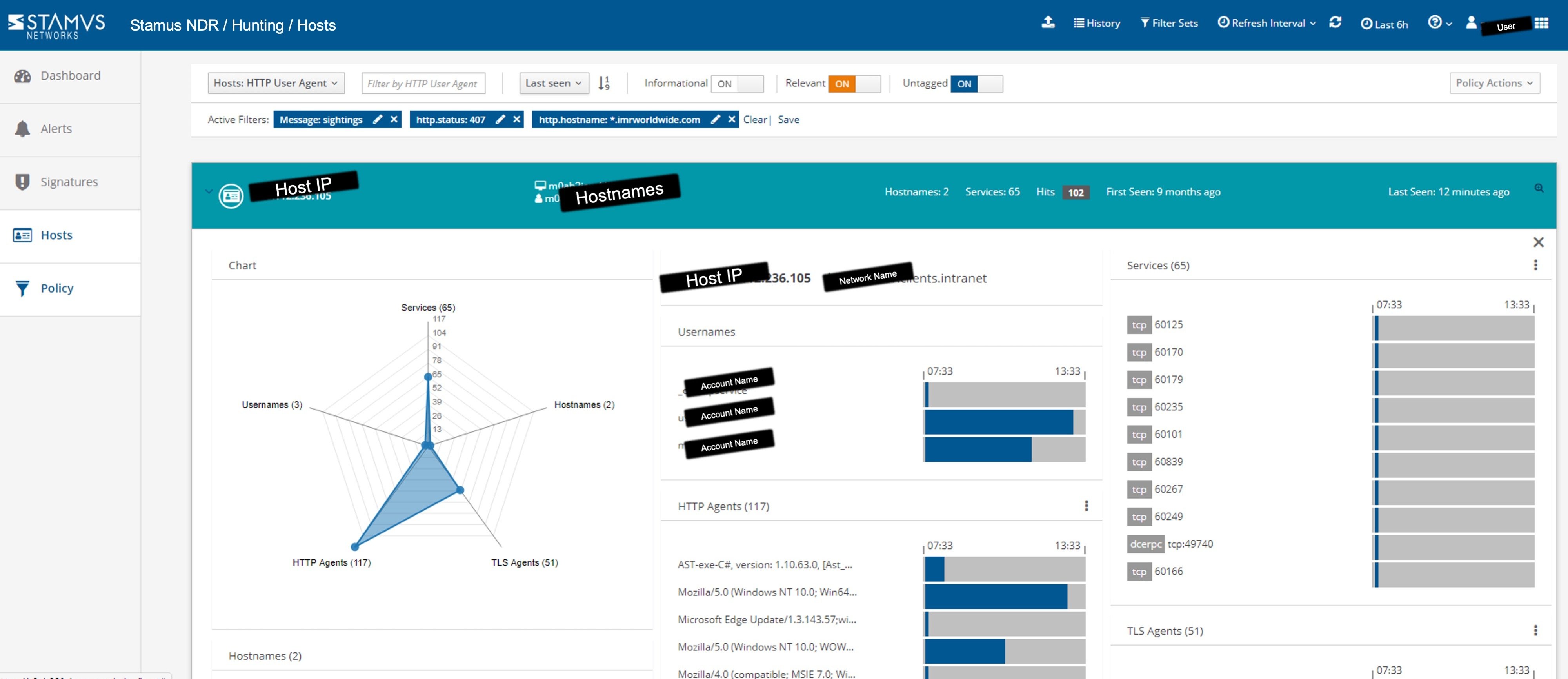
The “Host Insights” function of Clear NDR (shown above) automatically identifies and fingerprints all user and computer accounts associated with a specific host. That allowed us to quickly determine that the account of the user currently exhibiting this behavior was actually a floor manager on duty in one of the corporate data centers.
The customer helped us investigate the relevant endpoint logs, and we identified those exfiltration requests as coming from an unauthorized adware extension installed in the user’s standard browser included with PC kits.
Why this Matters
In the end, we confirmed that this spyware had managed to evade the endpoint defenses (EDR) and the company-wide browser restrictions.
Detecting this from the network allowed the customer to open an incident and engage their EDR/SoC teams to evaluate further impact and other potential points of quarantine that may be needed.
This is an example of an unintended/unwanted software install that escalated to an attempted exfiltration of company and personal data. And the attack was perpetrated through a user with trusted administrative privileges to the organization's critical IT infrastructure.
We are confident that if this incident was not detected, it would have escalated to become much worse and result in monetary or infrastructure damages to the company.
More Information
Hopefully this gives you a taste of how Clear NDR can help security teams know more, respond sooner, and mitigate the risk to their organizations.
To read more articles in this series, check out these "Uncovered with Stamus NDR" blogs:
- Uncovered with Clear NDR: ModiRAT
- Uncovered with Clear NDR: Shadow IT
- Uncovered with Clear NDR: Danger in the Data Center
- Uncovered with Clear NDR: User Agents Tell the Story
And if you’d like to see Clear NDR in action, please click on the link below to schedule a live demonstration.





.jpg)


