One of the most common challenges many cybersecurity professionals face is the prevalence of alert fatigue. If your organization uses an intrusion detection system (IDS) then you might already be concerned with alert fatigue and seeking potential solutions like network detection and response (NDR) to help minimize its effects. For those still deciding on the best way to implement network security at their organization, alert fatigue is an important issue to address proactively.
What exactly is alert fatigue? What causes it, and how can an organization prevent it? To answer these questions, the NDR experts at Stamus Networks have prepared this guide to help you understand alert fatigue and address its root cause.
In cybersecurity, alert fatigue is the state of desensitization experienced by security analysts due to an excessive volume of security alerts. Constant notifications often signaling false alarms from systems like IDS can impair an analyst’s ability to differentiate between critical and non-critical threats. IDS is not the only culprit, however. Alert fatigue can result from a combination of tools and systems detecting a range of threats and suspicious activities.
With numerous cybersecurity tools generating alerts for various security events — both malicious and benign — it is easy to overlook or entirely miss serious and imminent threats or have drastically slower response times. We believe that all alerts are important, serving the function of flagging information that could be relevant for more than just threat detection, but that doesn’t negate the fact that the sheer number of alerts produced by many network security tools, such as IDS, can be overwhelming.
While signature-based detection, such as that found in intrusion detection systems (IDS), is often one of the main causes of alert fatigue, it is not the only factor that causes it. Complex IT environments, inefficient processes, redundancy-based strategies, and false positives all contribute to the prevalence of alert fatigue in cybersecurity.
Mitigating alert fatigue is essential for maintaining an effective cybersecurity posture. Thankfully, there are ways to minimize alert fatigue without sacrificing the detection provided by signature-based systems like IDS, but we will go more into detail on that later.
For an example of cybersecurity alert fatigue, let’s look at a hypothetical:
Let’s say a healthcare organization’s Security Operations Center (SOC) is tasked with monitoring a large network encompassing patient data, administrative systems, and connected medical devices. Their IDS is configured to detect a broad spectrum of activity on the network, generating thousands of alerts daily.
In this scenario, the IDS identifies a series of failed login attempts originating from an unfamiliar IP address. An alert is triggered, notifying the SOC analyst. Shortly after, another alert appears, indicating unusual data transfer patterns from a specific medical device. These alerts are followed by a continuous stream of notifications regarding potential malware activity on various workstations.
The constant influx of alerts, some of which might be false positives (non-threatening events flagged as threats), can desensitize the analyst. They might start prioritizing responding to the most recent alert or overlooking alerts with seemingly generic descriptions. In this scenario, the initial failed login attempt, potentially indicating a hacking attempt, could be overshadowed by the subsequent alerts. This might lead to a delayed investigation, allowing the attacker time to exploit vulnerabilities. The analyst must spend significant time investigating each alert only to find that one was serious, leading to inefficiency and potential burnout. This hinders their ability to focus on in-depth analysis and proactive threat hunting.
An overwhelming volume of alerts, paired with false positives, can contribute to alert fatigue. This example emphasizes the importance of implementing strategies to prioritize critical alerts and streamline security tools to minimize desensitization and ensure timely response to genuine cyber threats.
So how can you diagnose whether or not the analysts in your organization are experiencing alert fatigue?
Alert fatigue in cybersecurity can manifest in both individual analysts and in organizational processes. Recognizing these alert fatigue symptoms is the first step in diagnosing an alert fatigue problem and working towards solving it:
Symptoms in Individual Analysts:
Symptoms in Organizational Processes:
Organizations can identify alert fatigue through a combination of monitoring metrics and direct communication with security analysts. Analyzing trends in response times, alert dismissal rates, and the number of escalated incidents can reveal potential issues. Additionally, conducting surveys and holding open discussions with the security team can provide valuable insights into their workload and experience with alert volume.
So, you’ve determined that your organization is dealing with an alert fatigue problem. What now?
There isn’t any fix-all solution to overcome cybersecurity alert fatigue; however, there are several strategies that can help minimize its impact within your organization:
Alert fatigue can quickly become an organization’s biggest weakness in cybersecurity. This is especially true for many organizations using intrusion detection systems (IDS). While IDS plays a vital role in flagging suspicious activity, they can inadvertently contribute to a state of desensitization and hinder effective threat detection.
The primary challenge is the sheer volume of alerts generated by IDSs. These systems are often configured to detect a broad spectrum of activities, leading to a constant stream of notifications. This includes not only genuine threats but also false positives – non-threatening events mistakenly flagged as suspicious.
The overwhelming number of alerts, coupled with the presence of false positives, creates several issues:
This reliance on IDSs creates a situation where the very tool designed to enhance security can inadvertently weaken it. Therefore, a crucial aspect of strengthening cybersecurity lies in mitigating alert fatigue within organizations. One way to do this is by replacing your IDS with a more advanced network detection and response (NDR) system that can automatically highlight the most serious and imminent threats.
While the above strategies are great ways to minimize the potential impact of alert fatigue within your organization, one of the most effective methods to fix alert fatigue caused by IDS is to transition to a more modern system that solves the challenges of IDS.
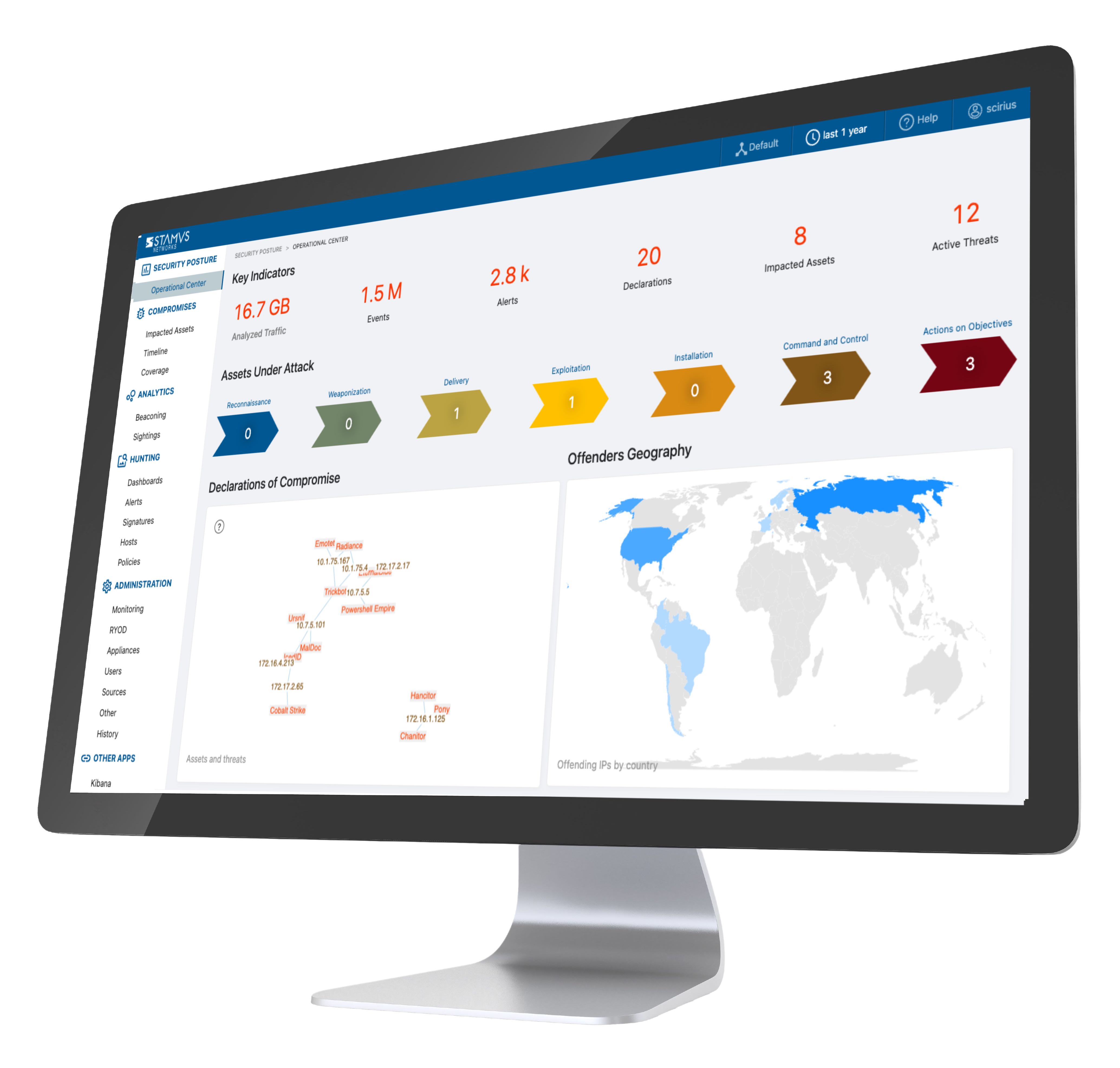
The Stamus Security Platform (SSP) is a broad-spectrum, open network-based threat detection and response system (NDR). SSP can be deployed on-premise or in cloud environments and uses deep packet inspection to directly extract and build security insights from network traffic. Built on top of Suricata – the powerful open-source network security engine – SSP combines signature-based IDS, network security monitoring (NSM) capabilities, and other advanced threat detection methods.
In order to combat alert fatigue and provide accelerated incident response, SSP adds automated event triage with extensive data enrichment and a unique capability called Declarations of Compromise™.
A key element of SSP’s ability to combat alert fatigue is the Declaration of Compromise™ (DoC). A DoC event is the highest confidence assertion SSP provides, highlighting a specific threat and the asset it is impacting. SSP then builds a detailed timeline of activity and collects the supporting evidence and context associated with the attack on the impacted asset. These events are automatically escalated, and the analyst is notified via webhook in a variety of applications - SOAR, SIEM, Discord, web chat, etc.
This dramatically reduces the number of security events that need to be investigated, essentially eradicating alert fatigue. Organizations that deploy SSP are able to redeploy their staff to focus on more proactive security measures and dramatically improve incident response times.
If you're considering upgrading from IDS to a modern alternative, we recommend looking at the following resources.
ABOUT STAMUS® NETWORKS
Stamus Networks is the global leader in Suricata-based network security and the creator of the innovative Clear NDR® system. Designed to close visibility gaps and reduce alert fatigue, Clear NDR transforms raw network traffic into actionable security insights with unmatched transparency, customization, and effectiveness. Trusted by leading financial institutions, government agencies, and battle-tested over 9 years in NATO’s largest cybersecurity exercises, Stamus Networks delivers proven, high-performance network detection and response solutions. Stamus empowers security teams – delivering clarity amidst complexity – with greater control, fewer false positives, faster response times, and a more responsive, open approach than legacy vendors.
© 2014-2025 Stamus Networks, Inc. All rights Reserved.