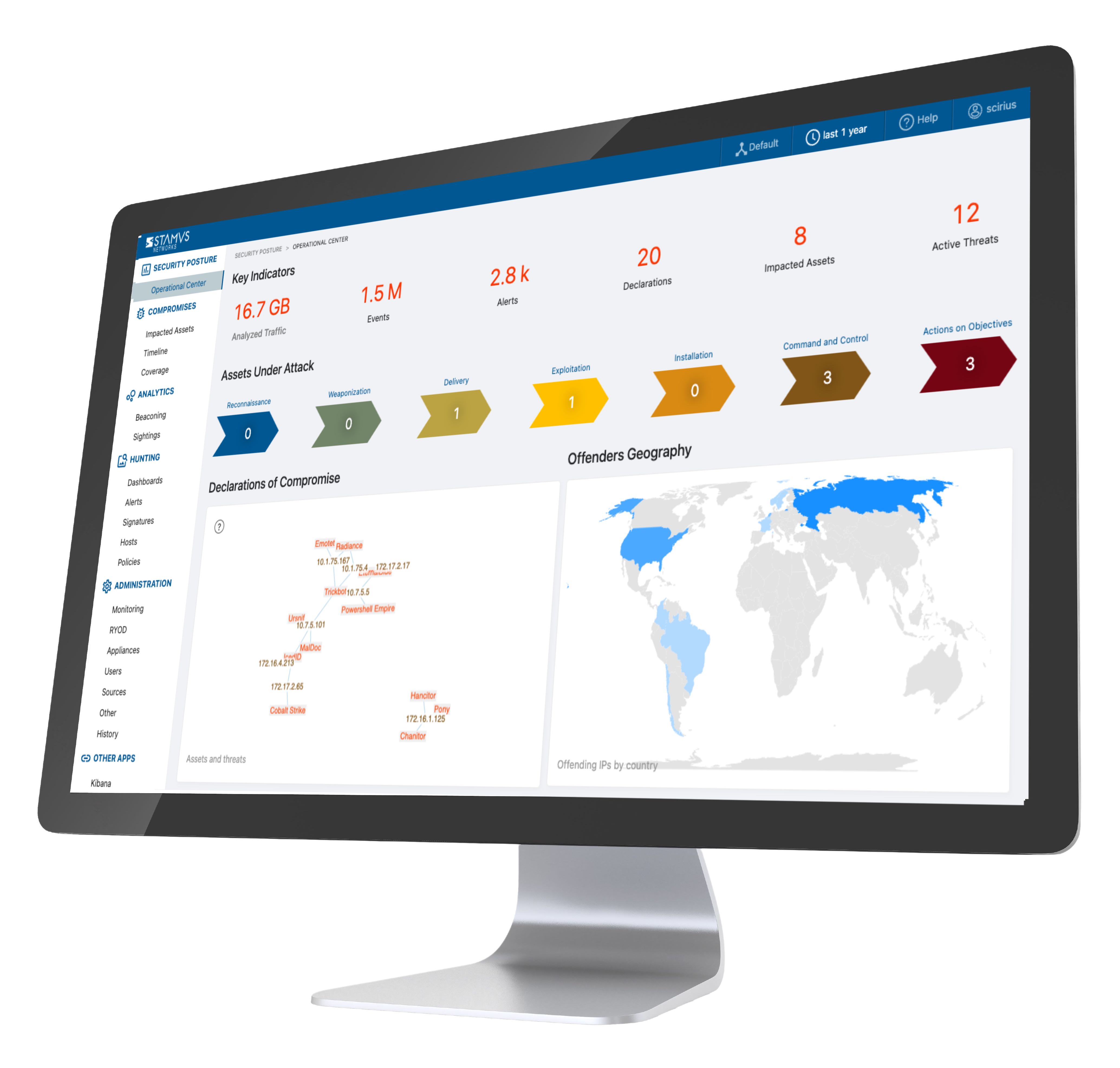
For many, searching for Gartner’s recommendations when evaluating a new product is an important part of the buying journey. Gartner is well known for their magic quadrant, which gives a visual representation of how various vendors stack up against one another. Unfortunately, Gartner has not released a magic quadrant for network detection and response (NDR).
With that in mind, buyers must seek alternative means of understanding this relatively young product category. By understanding NDR, the challenges it solves, and how it compares to other products, your organization will be better equipped to determine whether or not network detection and response (NDR) would be a good fit for your security strategy.
Despite the lack of a magic quadrant, Gartner still has a wealth of relevant information in their "2024 Market Guide for Network Detection and Response". Stamus Networks is pleased to offer a complimentary copy, available to download for free.
As defined by Gartner, network detection and response (NDR) products:
“Network detection and response (NDR) products detect abnormal system behaviors by applying behavioral analytics to network traffic data. They continuously analyze raw network packets or traffic metadata between internal networks (east-west) and public networks (north-south). NDR can be delivered as a combination of hardware and software appliances for sensors, and a management and orchestration console in the form of an on-premises software or SaaS.”
By this definition, an NDR is a system that analyzes network traffic on both internal and public networks to detect unusual activity. This is a relatively broad definition of NDR. While many products that claim to be NDR will fit within this definition, each product will likely perform their data collection, analysis, threat detection, and incident response in different ways.
The “2022 Market Guide for Network Detection and Response” suggests NDR is becoming more mainstream. This report claims that the network detection and response market is growing steadily at a 22.5% rate.
Gartner first recognized network detection and response as a market category in 2020. Since then, they have also published other helpful reports such as the “2023 Top Use Cases for NDR” and the “2023 Voice of the Customer for Network Detection and Response”. It is important to note that Gartner’s reports cannot be accessed without becoming a Gartner client, however Stamus Networks has made the "2024 Market Guide for Network Detection and Response" available to download for free.
Gartner is well-known for their “magic quadrant”. This chart places different cybersecurity vendors based on their “completeness of vision” and “ability to execute”, leading each vendor to be placed in one of four categories: niche players, visionaries, challengers, and leaders.
Currently, there is no network detection and response magic quadrant, however it is hopeful that one might be included in future reports. For now, the best option is identify the challenges NDR can solve and determine whether those challenges are faced by your organization. If so, NDR might be a good fit for your security strategy.
Network detection and response (NDR) solutions solve several challenges centered around threat detection, visibility, incident response, and more. By solving these challenges, NDR enhances an organization’s ability to safeguard digital assets and data. The following use cases should be considered when evaluating whether or not NDR is a fit for your organization:
Understanding these use cases can help fill in the gaps of information that are unavailable or inaccessible in a Gartner report. However, it is not only important to know what challenges NDR solutions solve, but also to know the difference between NDR and other common cybersecurity products.
Intrusion detection / prevention systems (IDS/IPS) are reactive network security systems, while network detection and response (NDR) products are proactive network security systems. Both systems rely on network traffic data to detect threats, but they differ in what they can detect.
IDS/IPS monitors network traffic and then detects threats using a rule or signature-based detection method. These systems contain a limited database of known threats and vulnerabilities, and when network traffic data matches one of those known signatures it will either issue an alert (in the case of IDS) or block that traffic (in the case of IPS).
Network detection and response products emphasize early detection and response to security incidents. Most NDR products do include IDS/IPS signature-based detection for known threats, but NDR also usually includes a combination of other more advanced detection methods like AI, machine learning, and behavioral analytics. These advanced detection methods are designed to catch potentially malicious traffic before it breaches the network, identifying anomalies or patterns indicative of malicious activity early on.
Network detection and response (NDR) software monitors network traffic data to identify and respond to threats, and endpoint detection and response (EDR) monitors individual devices to detect and respond to threats.
NDR and EDR often seek to solve similar challenges and in some cases will even share certain feature sets. The biggest difference between the two is their source of data. EDR systems need to deploy an endpoint agent software onto each individual device. That device could be a laptop, desktop, server, mobile phone, tablet, or any other device with a compatible operating system. The endpoint agent will then communicate with the central EDR system, alerting the security team of any malicious software or unauthorized activity on the device.
EDR is a very common cybersecurity system, however there are some environments where EDR is not feasible:
In these instances, network detection and response software becomes a much more viable option. An NDR would allow security teams to maintain maximum visibility with a fully passive monitoring system.
NDR is a fully passive system that is purpose-built to monitor network traffic data and integrate with other systems, whereas extended detection and response (XDR) often requires active monitoring through the use of endpoint agents and are commonly “closed” systems.
Extended detection and response (XDR) is the newest product category in threat detection and response systems. As a result, there is not a single definition that encompasses all XDR systems. Generally, XDR describes a system that combines multiple telemetry sources — network, endpoint, cloud, servers, and more — and then analyzes the data from all sources to detect security threats.
XDR seems great in theory, and for some organizations it is a good fit, but problems arise when a single vendor attempts to integrate so many systems into a single platform. Primarily, the system often becomes “closed”, meaning integration with other threat detection systems, 3rd party threat intelligence sources, and other data enrichment services becomes incredibly difficult or impossible.
Oftentimes, it is much more effective for an organization to use products from multiple best-in-class vendors and then integrate independently. Choosing an NDR vendor that fits your organization and pairing it with EDR, security information and event management (SIEM), and security orchestration automation and response (SOAR) systems will likely produce better results than a single-vendor XDR platform.
Network traffic analysis (NTA) preceded network detection and response tools, and in time NDR built upon the foundation of NTA and the terms became synonymous. NTA is a method of network monitoring using either flow data (from devices like routers) or packet data (from SPAN, network TAPs, or mirror ports). Network detection and response tools expanded on the capability of NTA systems by adding increased functionality for investigating historical metadata, threat hunting, and automated threat response.
Many NDR tools began as more simple NTA solutions, and have since expanded. Generally, the two terms are now interchangeable.
You need an NDR because network detection and response provides additional visibility, operates in environments where other methods fail, and enables a more comprehensive and proactive security strategy. Here are four reasons why you need an NDR:
Hopefully, Gartner will release a network detection and response (NDR) magic quadrant in the future, but until then we are left looking for other ways to evaluate different NDR solutions. The best way we can do that now is by understanding the qualities that make a sophisticated NDR as well as the other cybersecurity products an organization might use. This can give us a good picture of what to look for and what our organizations might need.
If you are ready to see NDR in action, book a demo call with one of our experts below.
Choosing an NDR isn't an easy decision. These resources could help:
ABOUT STAMUS® NETWORKS
Stamus Networks is the global leader in Suricata-based network security and the creator of the innovative Clear NDR® system. Designed to close visibility gaps and reduce alert fatigue, Clear NDR transforms raw network traffic into actionable security insights with unmatched transparency, customization, and effectiveness. Trusted by leading financial institutions, government agencies, and battle-tested over 9 years in NATO’s largest cybersecurity exercises, Stamus Networks delivers proven, high-performance network detection and response solutions. Stamus empowers security teams – delivering clarity amidst complexity – with greater control, fewer false positives, faster response times, and a more responsive, open approach than legacy vendors.
© 2014-2025 Stamus Networks, Inc. All rights Reserved.