For organizations looking to add an intrusion detection system to their cyber security strategy, it can be difficult to choose between a network-based IDS (NIDS) and a host-based IDS (HIDS). Making this decision will ultimately come down to the needs of the organization, the existing infrastructure, and the goals of the organization’s security team.
The first step to deciding whether or not network-based intrusion detection is right for you is having a basic understanding of what NIDS is and how it differs from HIDS. It is also important to consider more modern, advanced approaches that achieve the same outcome without the challenges of IDS.
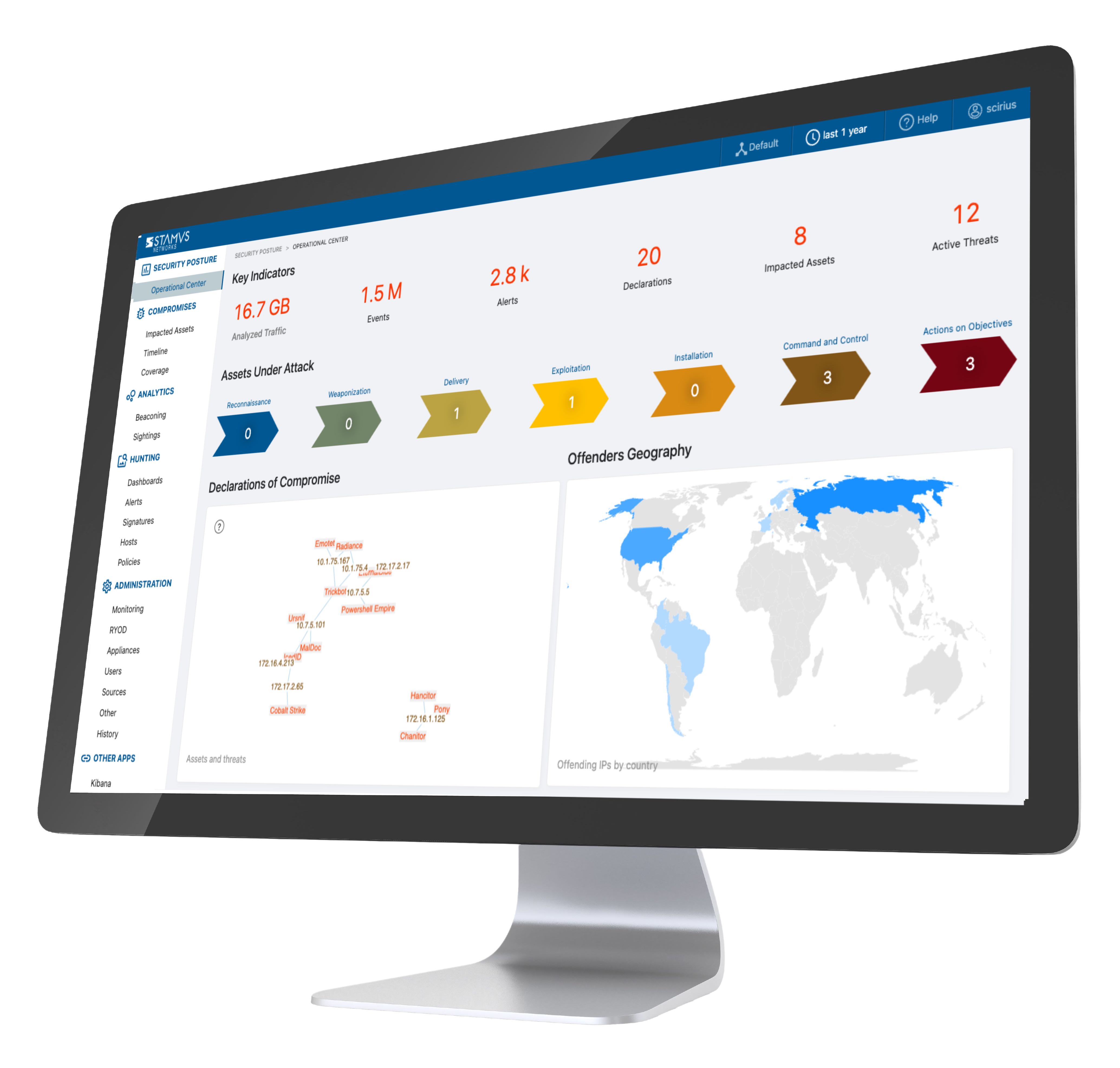
NIDS stands for Network Intrusion Detection System. It's a security tool that monitors your network traffic for suspicious activity. It does this by performing the following tasks:
NIDS is a passive system, meaning it just monitors and detects threats, it doesn't take any action to stop them. That's the job of a Network Intrusion Prevention System (IPS), which works alongside NIDS to actively block malicious traffic.
The purpose of NIDS is to monitor network traffic for suspicious activity across your entire network. This is different than the purpose of a host-based intrusion detection system (HIDS), which monitors individual devices or servers (hosts) within the network for suspicious activity.
Both of these systems function basically the same way. They monitor traffic, analyze the packets for evidence of threats, and alert when potentially malicious traffic is identified. The only real difference is whether they are monitoring individual devices or the network as a whole.
Benefits may vary depending on the type of intrusion detection system or the method of detection used by the system. NIDS in particular will provide:
Improved Security Posture:
Enhanced Network Visibility:
Faster Response Times:
Additional Advantages:
There are several compelling reasons why network intrusion detection system software is essential for robust network security. Here are some of the key benefits:
The best network intrusion detection system is Suricata.
Suricata is a popular open-source Netowrk-based IDS (depending on configuration) that offers a powerful and flexible solution for network security monitoring. Here's how Suricata functions as a NIDS:
Suricata's versatility extends beyond basic NIDS functionalities. It can also be configured to function as:
The three types of intrusion detection systems in cyber security based on detection methods are: Anomaly-based, Signature-based, and Hybrid. These methods define how the IDS analyzes data to identify potential intrusions.
Each of these three detection methods (Anomaly-based, Signature-based, Hybrid) offers different strengths and weaknesses. Choosing the most suitable approach depends on factors like the specific security requirements of the network, the resource availability for managing the IDS, and the acceptable level of false positives.
It is also important to consider switching to a more advanced modern network security solution, such as network detection and response (NDR). The Stamus Security Platform (SSP) is a modern NDR solution that leverages the best from IDS technology without the same challenges faced by IDS users. Learn more at https://www.stamus-networks.com/stamus-security-platform
The difference between IPS and IDS is that IPS actively blocks threats while IDS simply provides alerts. The best intrusion detection systems can function as both depending on the configuration, but both systems serve a purpose in an organization’s strategy and come with their own unique benefits and challenges.
Network detection and response (NDR) is an approach to cybersecurity that uses an organization’s network traffic to identify and respond to potential threats. Using advanced detection mechanisms, such as artificial intelligence and machine learning, network detection and response systems monitor traffic in near real-time and then provide actionable insights that enable security professionals to mitigate serious threats. By enhancing an organization’s ability to both detect and respond to threats, NDR reduces the risk of data breaches and unauthorized access.
Network detection and response systems continuously collect and analyze network traffic data, and then use a combination of tools to identify known threats, abnormal patterns, or other signs of malware infection. Many NDR systems include tools for behavioral analysis, which allow the system to establish a baseline of “normal” network behaviors and then recognize deviations indicative of potential security threats.
Network detection and response is different from many other traditional security tools because it combines multiple capabilities. Most NDR systems do include traditional security measures, such as those found in an intrusion detection system (IDS), but they also provide organizations with more modern technologies that are equipped to identify emerging threats.
Both NDR and IDS/IPS function by monitoring network traffic, but the difference between the two security systems lies in their approach to how threats are detected using network traffic data.
IDS/IPS is reactive, relying on a limited database of known threats and vulnerabilities to stop malicious traffic from entering or leaving the network. NDR is proactive, emphasizing the early detection and response to security incidents. IDS/IPS does not have the advanced functionality of NDR, however many NDRs include IDS signature-based detection methods.
IDS simply issues an alert anytime network traffic matches a signature for a known attack signal. This means it is not only unable to detect novel threats, but it also cannot detect more nuanced or weak attack signals like those found in unauthorized user activity, anomalous network activity, malware beacons, or homoglyphs.
Alternatively, NDR includes functionality that filters events from various sources into actionable alerts with context. It also includes more advanced detection methods built with machine learning and artificial intelligence to detect the more nuanced attack signals that are missed by IDS. NDR will typically also include other useful features, such as interfaces for threat hunting.
IDS is undoubtedly a powerful and effective means to detect known threats on your organization’s network. Unfortunately, most IDS deployments are riddled with false positives, provide limited threat detection, and lack sufficient visibility into anomalous activity and subtle attack signals. Traditional IDS vendors have failed to innovate in ways that solve these challenges, leading to inefficient or downright ineffective threat detection.
You need a network security platform that doesn’t generate an endless stream of useless alerts across part of your network, and instead automatically identifies alerts of interest and notifies you of only serious and imminent threats. Your organization deserves response-ready detection with visibility into your entire network regardless of the environment with easy access to all the contextual evidence you need to stop an attack before it can cause damage. Replace your legacy IDS with a modern network detection and response platform that gives you these features and more.
The Stamus Security Platform™ is a network-based threat detection and response solution that eliminates the challenges of legacy IDS while lowering your response time. Stamus Security Platform harnesses the full potential of your network, bringing state-of-the-art threat detection, automated event triage, and unparalleled visibility to the security team.
Book a demo to see if Stamus Security Platform is right for your organization.
If you're considering upgrading from IDS to a modern alternative, we recommend looking at the following resources.
ABOUT STAMUS NETWORKS ™
Stamus Networks believes that cyber defense is bigger than any single person, platform, company, or technology. That’s why we leverage the power of community to deliver the next generation of open and transparent network defense. Trusted by security teams at the world’s most targeted organizations, our flagship offering – Clear NDR™ – empowers cyber defenders to uncover and stop serious threats and unauthorized network activity before they harm their organizations. Clear NDR helps defenders see more clearly and act more confidently through detection they can trust with results they can explain.
© 2014-2025 Stamus Networks, Inc. All rights Reserved.