In addition to deploying advanced detection technologies, many security teams make threat hunting an important element of their proactive defenses. Given the number of tools in the cybersecurity tech stack at many organizations, it can be difficult to know where to begin. For this reason, Stamus Networks has developed some simple tools to help uncover threats that may not have been found by automated detection technologies.
Stamus Security Platform (SSP) is highly effective at automatically detecting serious and imminent threat events on the network, escalating the highest priority (and highest confidence) ones into Declarations of Compromise™, and summarizing all the relevant details about the incident so the analyst can quickly get to patient zero.
But what happens to the other security events (e.g. alerts) that were captured but were not escalated with high confidence ? Well, proactive organizations allocate time for security practitioners to search through historical data, looking for evidence of specific threats, anomalous activity, and suspicious behaviors. This is where the Stamus Enriched hunting interface comes into play.
Included with Stamus Security Platform, there are currently over 100 ready-to-use hunting filters which cover numerous aspects of metadata hunting. Any one of those filters would be a great place to start when it becomes time to begin practicing more proactive defensive measures.
Hunting for Potentially Unwanted Programs (PUPs)
To kick things off in week 1 of this new series, “Discover SSP: Guided Threat Hunting” we are going to begin by reviewing a hunting technique to locate unwanted software or programs within an enterprise network. These potentially unwanted programs (PUP) we are searching for are ones which are not authorized to be installed and could be harmful due to the risk of malware deployment and financial loss.
For an overview of the Stamus Enriched Hunting interface, read our "Introduction to Guided Threat Hunting".
What are Potentially Unwanted Programs (PUPs)?
Potentially Unwanted Programs (PUPs) are programs that are downloaded unintentionally. Oftentimes, PUPs are bundled into existing software download packages, hiding within the install client or end-user licensing agreements. These programs are typically considered “unwanted” because they bring no benefit to the downloader and sometimes function as spyware or adware.
A common misconception is that PUPs are malware. This technically isn’t true because PUPs are installed with user consent whereas malware is not. A lot of PUP software does, however, target the user in a malicious way. For example, a PUP might slow down the computer, display unwanted ads, track the user's online activity, and even steal private information. This is why it is important to identify and then remove PUPs when they become present on an organization’s network.
Identifying PUPs using Stamus Security Platform
Let’s take a look at an example:
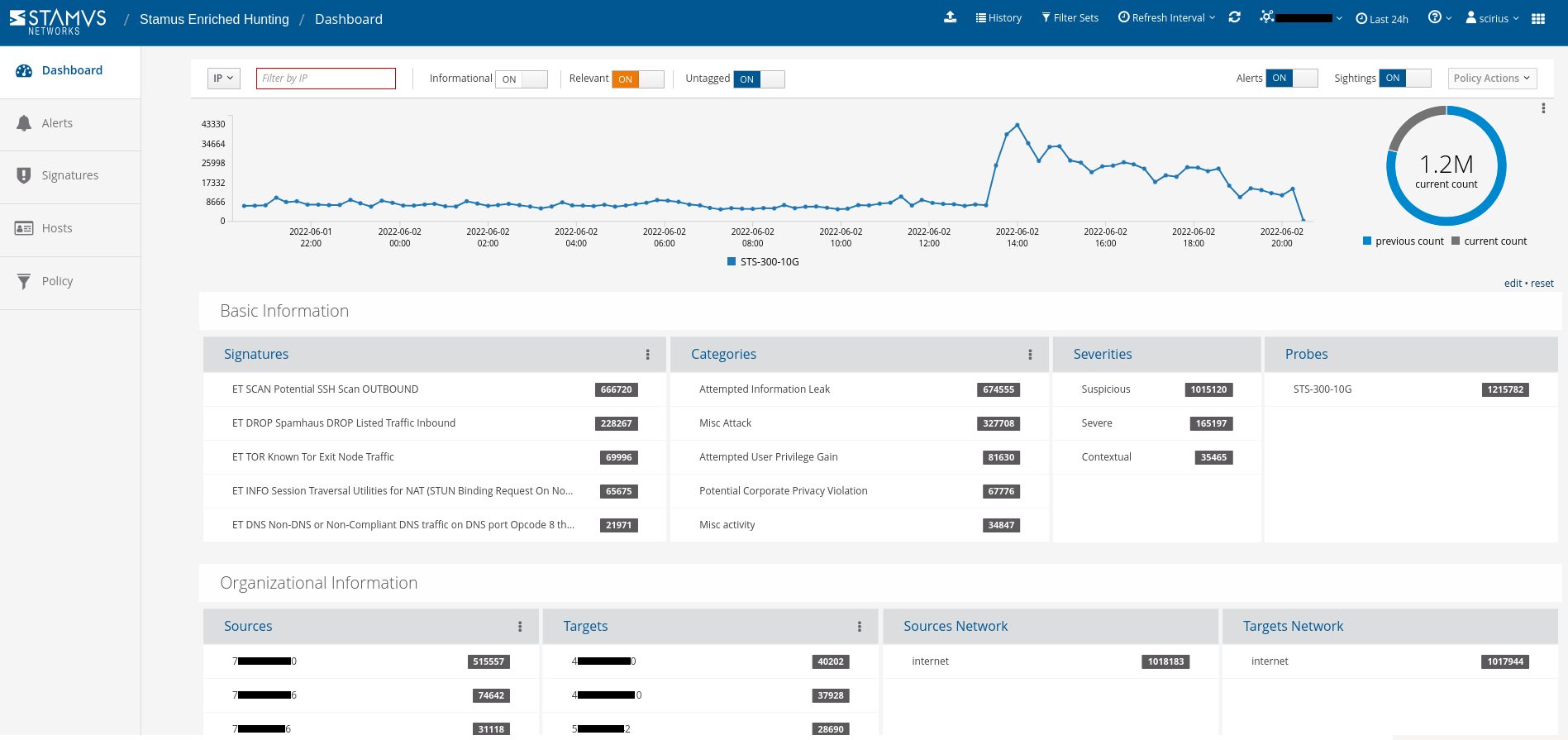
In the past six hours, this SSP installation has generated about 1.2M legitimate alert events. Now, for some of these, SSP may have automatically escalated them to a Declaration of Compromise and notified the security team to take immediate action. But let’s assume that’s not the case, and that we are interested in starting a proactive hunt.
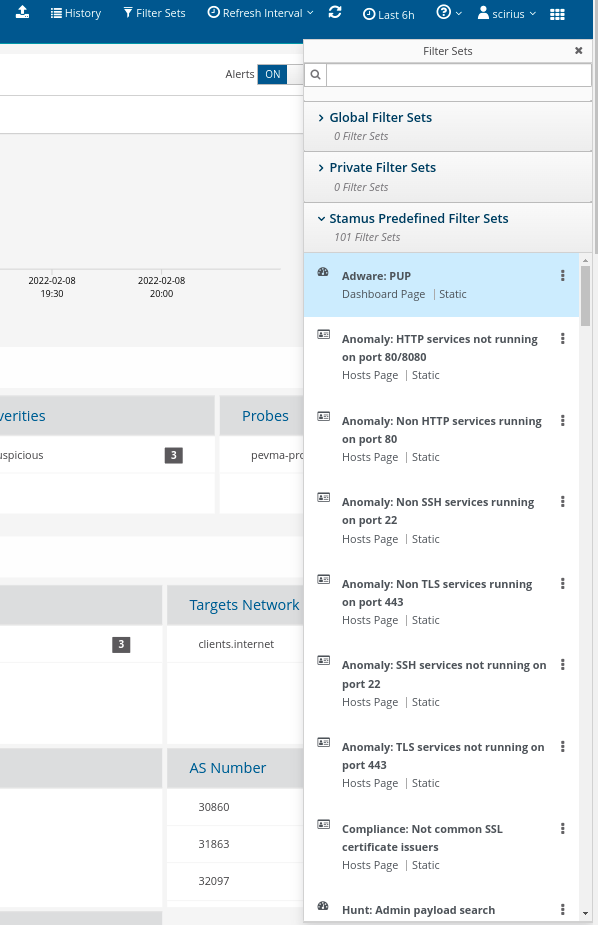
Let’s zoom in directly on potentially unwanted programs installed in the clients that communicate actively on the network. First, we need to select the PUP Filter.
For this hunt, we also want to zoom in specifically on “clients”. For that, we simply enter a wildcard selection on the “*clients” aggregated network label.
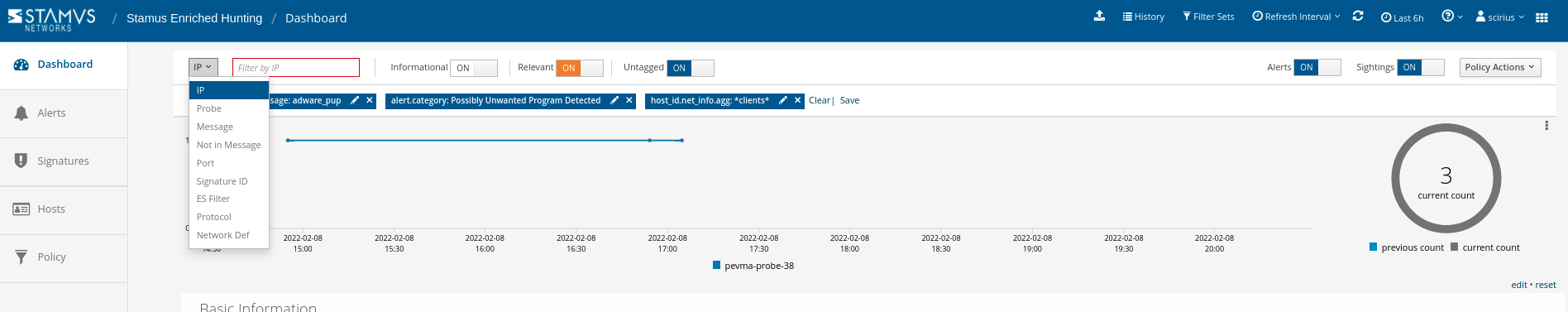
This filters us down to 3 events out of 1.2 million in the past 24 hours. From this page, we can also quickly determine sources, asset targets, and network regions at a glance. Note: SSP identifies the source and “target” hosts - different from the traditional “source” and “destination” IPs present in most security logs.
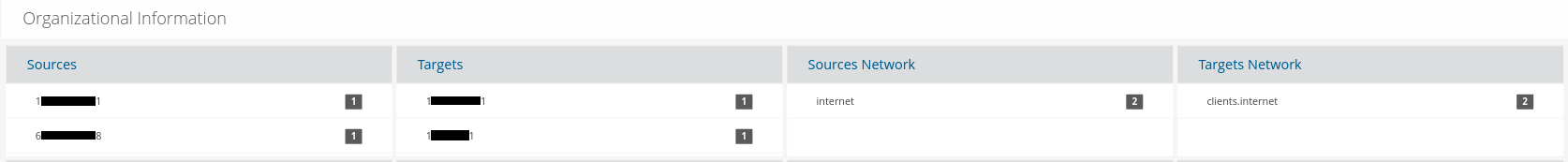
All of those alert events are enriched with network forensic-oriented context in the form of protocol data (file transactions, flow, etc), including new transaction sightings which have not been seen on the network before. In the screenshot below, we can see the communication between a previously unseen http user agent and http server.
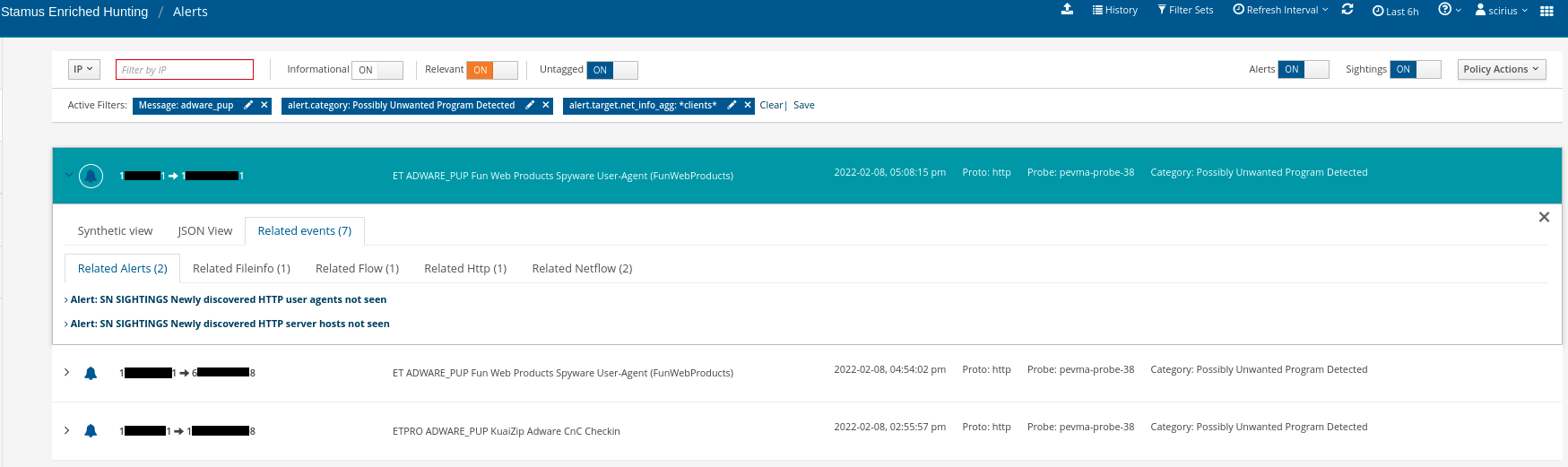
In just a matter of seconds, we were able to filter through 1.2 million events on the network to locate 3 specific events and their contextual evidence. We can now easily view unauthorized programs within the client’s area.
But what do we do next now that we have found what we were hunting for? Let’s walk through some options:
The first step is to find out the user account that is currently logged in. To view this information, we need to select the “Hosts” menu from the left hand navigation.
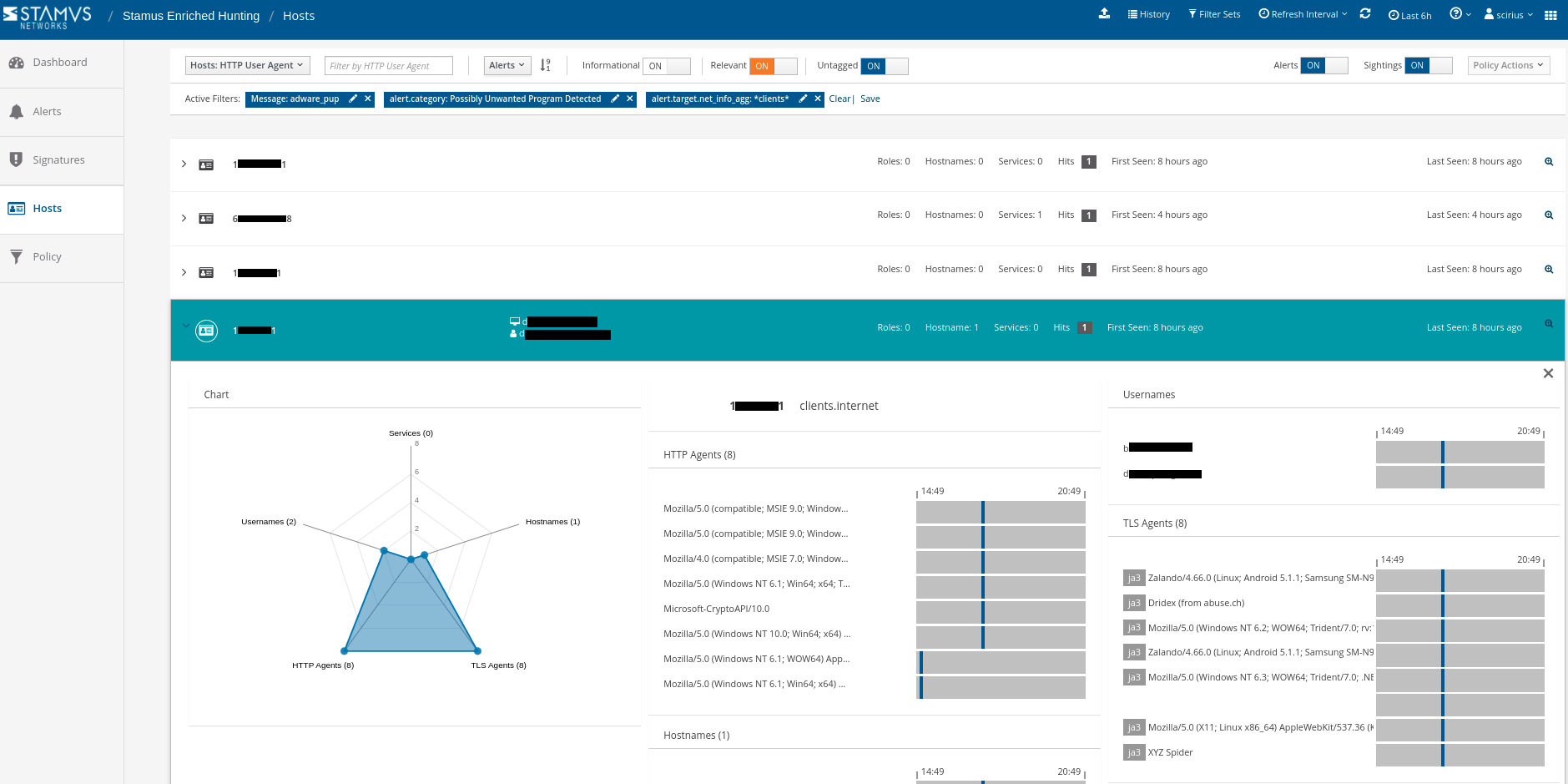
From here, we can further review the services, other Host Insights metadata, and the protocol transaction logs to determine if an incident should be raised.
Additionally, we can create an automation to further streamline the next hunt. By adding a tag action, we can classify future similar events as “relevant” to make them easier to locate.
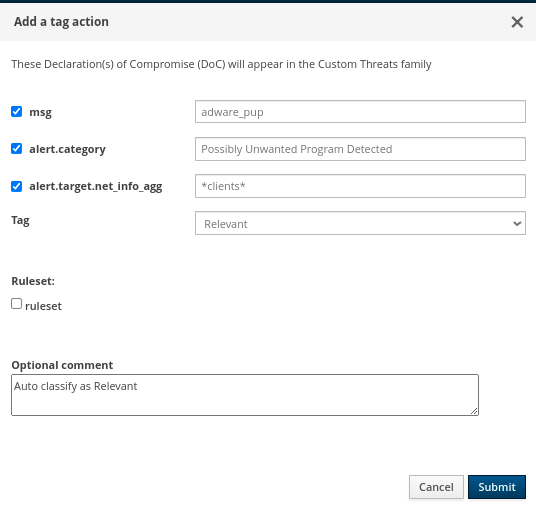 By creating this automation, we can accelerate future hunts. So, next time, we can filter by relevance by simply toggling the switch in the top navigation. The results will include all relevant events from previous hunts and may include classifications of tags set by other members of the security team.
By creating this automation, we can accelerate future hunts. So, next time, we can filter by relevance by simply toggling the switch in the top navigation. The results will include all relevant events from previous hunts and may include classifications of tags set by other members of the security team.
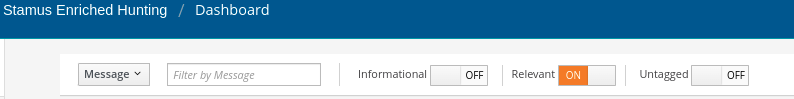
If we want to automate further, we can escalate those future events using the Policy Actions menu (SSP refers to these escalations as “Declarations of Compromise” or “DoC”) so that you can be notified of an occurrence directly in your SOC chat system of choice, such as Slack, Discord, Mattermost, etc. As part of this DoC automation, you may also automate the system to transfer supporting evidence as it opens an IR ticket in a system like Hive or ServiceNow. This escalation can also trigger executions like quarantines via SOAR, EDR, or XDR.
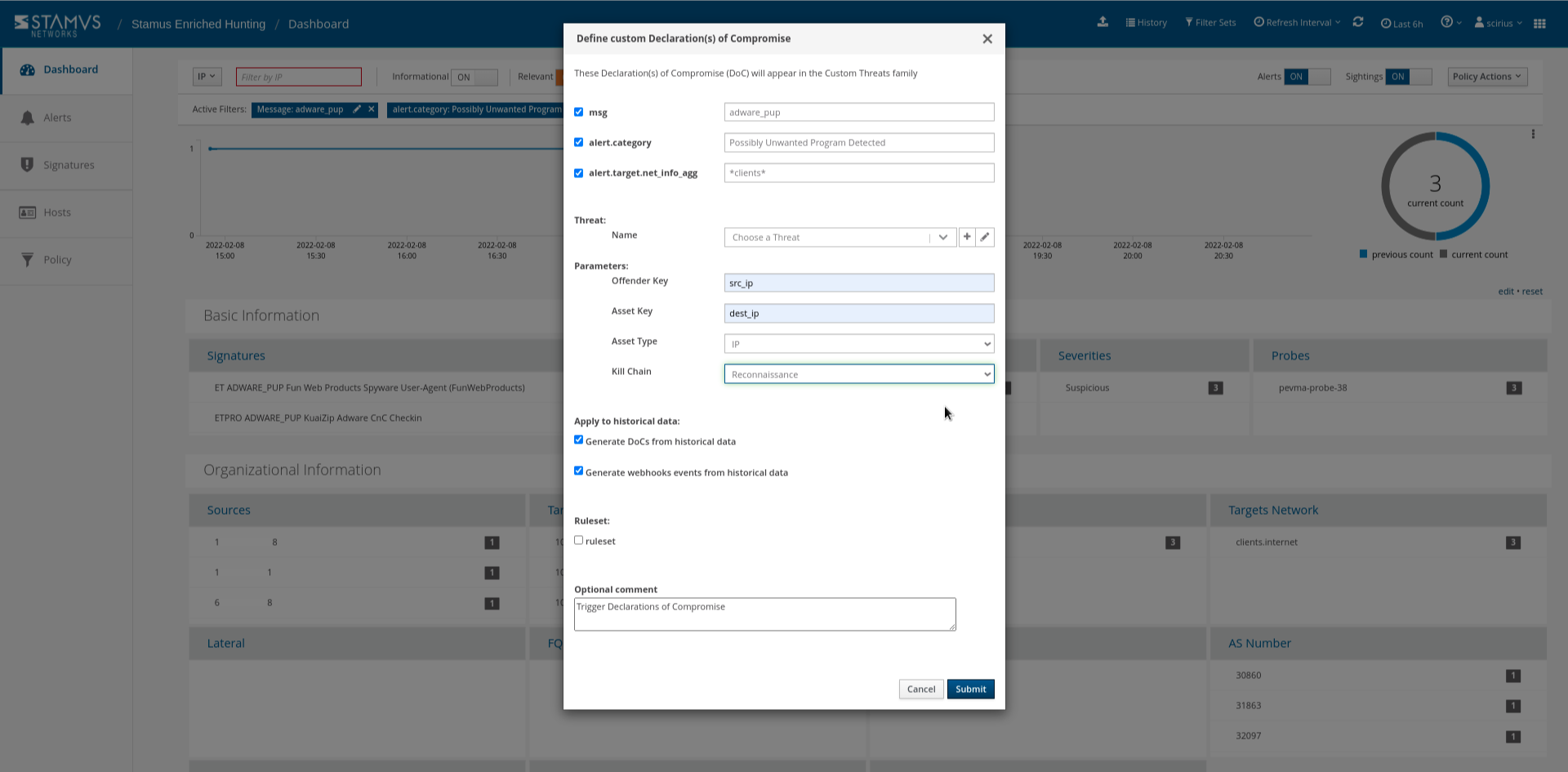
Conclusion
This guided hunting filter is just one of many that an analyst could use to identify unwanted activity or potentially dangerous threats on their organization’s network. Locating the PUP is just the first step. As we mention above, once a PUP has been identified, there are other automations and escalations that could be implemented to further protect the organization. To learn more about what to do after the hunt, view our article on automation and escalation with the Stamus Enriched Hunting interface.
If you want to see Network Detection and Response (NDR) from Stamus Networks and the hunting interface in action, click the button below to schedule a demo to run through Stamus Security Platform (SSP).







